This content originally appeared on Level Up Coding - Medium and was authored by Samiran Ghosh

If you’re my age, you will remember the critical premise of the 1992 classic “Sneakers”, starring Robert Redford and Ben Kingsley — a top-secret black box that can break the encryption of any computer system. Quantum computing is that “black box.” In the next 2–7 years, quantum computers could change the face of cybersecurity. Once they can factor products of large prime numbers (the basis of current cryptography) (expected between 2024 and 2030) — existing cyber-defense mechanisms will be rendered obsolete. We need to plan for encryption in the quantum future.
What is Quantum Computing?
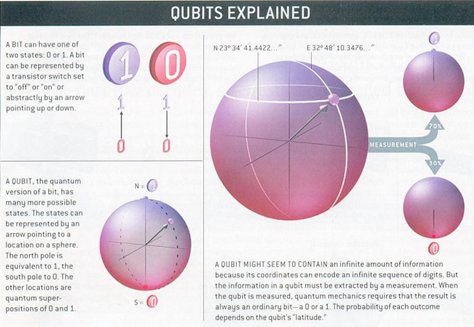
Classical computers use binary arithmetic — all numbers are a sequence of bits — either a 1 or a 0. However, a quantum bit (qubit) exists not as a 0 or 1 but as a superposition of the two (think Schrödinger’s cat). Every additional qubit doubles the processing power of a quantum computer, allowing it to execute multiple computational paths simultaneously. Similarly, as per Grover’s algorithm, it is a known fact that quantum computing divides the key space of symmetric cryptography algorithms by two, meaning that their key sizes have to be doubled to keep the safety margin of today[1].
In October 2019, Google demonstrated quantum supremacy with Sycamore. It performed a series of operations in 200 seconds that Google claimed would take a supercomputer about 10,000 years to complete. In December 2020, physicists from the University of Science and Technology of China in Shanghai performed a Gaussian boson sampling technique with their photon-based quantum computer, named Jiŭzhāng. They declared that Sunway TaihuLight (the fourth fastest supercomputer in the world) would require 2.5 billion years (approx. half the age of the Earth) to finish the computations done by their quantum computer in a mere 200 seconds.
Cryptography: The gatekeepers of security
As the wise Spider-Man said — “With great power comes great responsibility. And great risk.” Much of the world’s encrypted data is protected using mathematical equations with millions of reasonable solutions. These encryption models are too complicated for even supercomputers to solve within an acceptable period, which quantum systems can quickly solve.
Modern cryptography relies on symmetric and asymmetric standards. The significant difference is that symmetric cryptography is based on substitution and permutation (there is no underlying mathematical assumption) and uses a single key for encryption and decryption. In contrast, asymmetric key / public key cryptography uses two different keys for encryption and decryption.
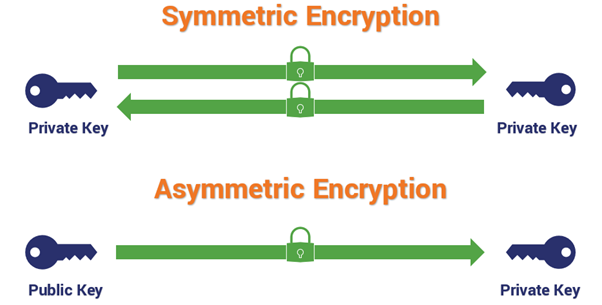
Since the mid-90s, researchers have theorized that quantum computers can break current public-key cryptographic (PKC) systems. Their ability to concurrently test multiple hypotheses (using Shor’s factorization OR Grover’s exhaustive search) at unprecedented speeds will make both asymmetric and symmetric cryptosystems redundant.
5G Vs 4G — is 20X faster, covers 10x more devices per sq. km. and has 25x less latency
Understanding 5G
5G is one of the most eagerly awaited technologies in the digital world, and with good reason. In the years ahead, 5G coupled with IoT, could revolutionize the integration of digital and physical worlds. What sets it apart from its predecessor?
1. 5G speed — it is nearly 20x faster than 4G. An average-length movie takes 6 minutes to download on 4G and less than 20 seconds on 5G
2. 5G supports 10x more devices per sq. km. It will seamlessly handle many more devices within the same area — a boost for IoT infrastructure
3. 5G latency is 25x less than 4G. According to McKinsey, 5G will speed up the mainstream adoption of IoT across multiple industries: Transport, Manufacturing, Healthcare, to name a few
5G and Quantum — the Perfect Storm
While quantum systems provide the compute, 5G provides the channel to connect more than just mobile networks (self-driving cars, personal medical tech), thus expanding the ‘threat surface.’ In a 5G world, secured communications are a critical component of connectivity, and post-quantum cryptography will play a key role.
Researchers globally are devising ways to embed quantum-safe cryptography into 5G networks without compromising QoS. I even came across a patent for a quantum-resistant 5G SIM card by a Swiss company that set an industry best practice in ITU-T X.1811 for quantum-safe 5G[2].
Cryptocurrency Wallets: A prime candidate for Quantum hacking
Imagine you forget the password of your Bitcoin wallet, which in theory had millions of dollars in the balance. With a quantum computer, you could unlock your wallet and save yourself many worries, which worries all cryptographers. If malicious players had a quantum computer, the first thing they would try and break is the Elliptic Curve digital signature algorithm, reverse-engineer your private key, forge your digital signature, and subsequently empty your wallet. Thankfully, we are still years away from that scenario, yet that is a telling tale for designing national digital currencies that are supposed to withstand the test of time. Likewise, this vital subject — including applications with legal consequences such as smart contracts enabled by blockchain technologies, which share the same technical basis and, therefore, vulnerabilities to quantum IT -, would need a dedicated article, hopefully soon as time enables it!
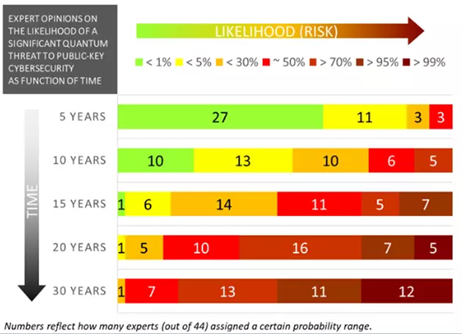
The real question is: when will quantum computers become a threat to public-key cryptography? As of December 2020, IBM claims to have a 65 qubit quantum computer and already delivering a 53-qubit model to a client[3] (it would take around 1500 qubits to hack Bitcoin private keys). Quantum computers could achieve the required processing power range from as soon as 2024 to as far as 2040 per estimate.
How do we solve it?
Public Key Cryptography enables over 4.5 billion users to securely access over 200 million websites and engage in over $3 trillion of e-commerce transactions. Further, an estimated 20% of all IT applications rely on PKC and an even higher percentage on symmetric cryptography. According to Prof. Davor Pavuna of the École Polytechnique Fédérale de Lausanne, “several quantum prototypes might already become functional in 2023 (specifically in China),” and that potentially poses a severe protection challenge much earlier!”
Many companies are developing “post-quantum cryptography” (PQC) or “quantum-safe cryptography” (QSC) — algorithms whose security is not degraded by any known quantum computing algorithms. Typical ones are McEliece cryptosystem, Lattice-based cryptosystems, Code-based Cryptography, and Hash-based cryptography. While these developments promise ‘quantum resistance,’ they only reflect our current knowledge of quantum computing capabilities and have a relatively low benchmark set for their security. These methods aim to create mathematical problems that are too difficult for even a quantum computer to solve, with the US National Institute of Standards and Technology (NIST) planning to recommend a PQC standard by 2022–23 and already having done so specifically for hash-based signatures. Similarly, German BSI issued official guidance for using post-quantum key exchange mechanisms, somewhat differing from NIST, and the IETF standardized two hash-based signature schemes, LMS and XMSS, independently, also with differences. Last but not least, the ITU-T issued without much publicity an amended recommendation on IPTV security X.1197 Amd1 that provides comprehensive guidance on state-of-the-art standard PQC options available as of late 2019, for use in multimedia transmission, with a corrigendum issued in early 2020.
The transition to PQC standards requires a staged approach. To successfully navigate the impending cryptographic change, companies and governments must embrace crypto-agility — the ability to rapidly adapt and switch between multiple cryptographic standards at varying levels
Applying the Solution
Post Quantum cryptography is a developing field. Although these algorithms are quantum-resistant in theory, there is an unpredictability about their efficacy. Secondly, these algorithms are heavy on memory and compute requirements, making it challenging to apply them universally. On the other hand, symmetric cryptography is more efficient and shows more resilience to quantum IT, yet needs an upgrade to accommodate larger key sizes. One such system I came across was a patent of the aforementioned Swiss company is eAES®, which enhances AES’s quantum resistance. It makes safely increasing the key size a reality (as per NIST’s IR 8105 guidance), a claim confirmed in a report by their competitor Kudelski Security on the former’s implementation for Intel® processors.
The transition to PQC standards requires a staged approach. To successfully navigate the impending cryptographic change, companies and governments must embrace crypto-agility — the ability to rapidly adapt and switch between multiple cryptographic standards at varying levels. We must support algorithms from different standardization bodies such as NIST, ETSI, the ITU-T, ISO/IEC, and the IEEE in a connected world with fractured standards.
We should adopt agile, integrated cybersecurity strategies now to ensure we are prepared for the age quantum computers will usher in
Building a global quantum security alliance
We are just laying the foundations of this new security ecosystem; however, more work is needed to drive broader adoption. While the academic, innovation labs, and specialist technical communities are making some progress, challenges abound:
- maturity of the technology and standards
- building the quantum security ecosystem itself and
- awareness and availability skills
Quantum computers will be revolutionary in their compute capability, so much that they can undermine the foundation of internet security. They are not just a technical achievement to be proud of, but a phenomenon that requires us to plan for without delay since they can undermine internet security. We should adopt agile, integrated cybersecurity strategies now to ensure we are prepared for the age quantum computers will usher in.
The time to prepare for a quantum-safe future is NOW (2021), as all experts in the field, starting with NIST’s head for PQC, Lily Chen, tell us.
[1] Depending on their construction, this is not an easy task. For instance, standard AES has construction issues making the mere augmentation of its key size insecure.
[2] handle.itu.int/11.1002/ps/X5Gsec_q-01
[3] https://www.cnet.com/news/ibms-first-retail-quantum-computer-in-the-us-headed-to-cleveland-clinic/
How Safe is Our Quantum Future? was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Samiran Ghosh
Samiran Ghosh | Sciencx (2021-06-29T15:23:23+00:00) How Safe is Our Quantum Future?. Retrieved from https://www.scien.cx/2021/06/29/how-safe-is-our-quantum-future/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
