This content originally appeared on Bits and Pieces - Medium and was authored by Alicia Jones
What is Social Engineering and how can you be safe?

With the rapid development in technology, we can also expect an equal level of increase in the number of cyber threats faced by us in our daily lives. Our current era is sometimes also referred to as the “Era of Data”. There is so much data out there where experts even consider data as another form of wealth. When there is a lot of wealth in play, the bad guys come into the picture.
These cybercriminals try to somehow access this data and use them for their own advantage. This can vary from ransoms to even using the data cause chaos.
There are several types of methods used by cybercriminals to cause problems for companies and individuals. One such method is known as Social Engineering. Let’s have a look at what this is.
What is Social Engineering?
Although the term “Social Engineering” sounds like some sort of society for engineers, it refers to something else. Social Engineering is the art of manipulating human psychology to accomplish malicious tasks. Social Engineering does not involve any sort of technical hacking in the process.
In a typical hacking scenario, a hacker tries to gain access to a company network by identifying and exploiting a vulnerability in its network. But in a social engineering attack, an attacker would try to manipulate an employee into divulging sensitive information, which can be used by the attacker to execute various actions.
Social Engineering attacks have become more and more common these days, where attackers are more focused on finding newer ways of fooling employees. Social Engineering attacks are not simple tasks. The attacker initially selects their target, monitors them for their activities, and finds any sort of psychological weakness. Then the attacker tries to gain the trust of the employee by using their weakness to their advantage. Once the employee falls for it, the attacker makes their move.
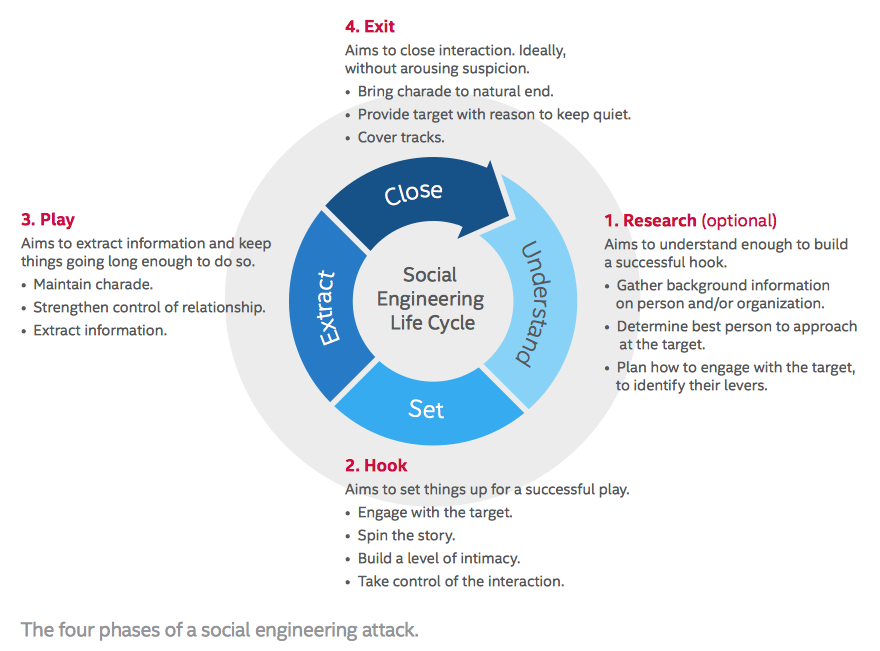
You can have the best security protocols in your organization, but a skilled social engineer can find their way around your high-end security and still manage to launch an attack. There have been numerous social engineering attacks even on the largest of tech companies. We will look at some of these later below.
Who Are Mainly Targeted?
Social Engineering attacks are mainly aimed at employees of organizations with high value and a lot to lose. Attackers would not waste their time exploiting a small-scale business, but rather they try to target large-scale companies and sometimes even governments to cause the most damage.
Several surveys have revealed that new hires are the most vulnerable to social engineering attacks as they still haven’t mentally prepared themselves for these kinds of attacks. These attacks are so complicated to the fact that you will never realize you are being manipulated until the damage has been caused.
Let’s have a look at the most commonly used attack techniques.
Most Commonly Used Attack Techniques
Phishing
Phishing is one of the most commonly used social engineering attack techniques. Phishing is a fraudulent attempt to extract sensitive information through the means of email or text messages by posing as a legitimate person.
Phishing attacks are mostly targeting a huge number of people and there is no single specific target point. Think of it as Fishing, where you do not try to catch a specific fish, but rather try to catch any fish. Therefore these phishing campaigns are done in bulk, in order to reach a large number of unsuspecting individuals.
An example of a phishing attack would be an email sent to users highlighting that their PayPal accounts are being blocked due to suspicious behavior. This creates a sense of panic amongst the recipients causing them to not think twice before clicking the links in the email. Once these links have been clicked, you will be redirected to a “spoof” website that will look exactly similar to PayPal with a near-identical URL as well. Once you submit the account credentials, the attacker will have access to your credentials as well. Another possible scenario would be that malware would be downloaded once you click on the link and it will execute itself on your local system.
Since Phishing attacks are done in bulk targeting many users, it is easy for mail servers to detect and block these types of attacks before they cause trouble for the end-user.

Spear Phishing
Spear Phishing is a more targeted version of Phishing where an attacker targets a selected employee or company. This form of attack requires a huge effort from the attacker and can even take several months of planning and preparation. The attacker needs to gather personal information regarding his subjects such as job, personality, characteristics, and even contacts. Once these are collected, the attacker sends a message via email, or text messages similar to Phishing, but these messages are tailormade to each target, making them look less obvious.
These types of attacks are the most successful ones if executed flawlessly. Since they are only sent in small numbers, it is hard for mail servers to detect and block these types of attacks.
Baiting
Baiting is an attack that uses a false promise to trigger the victim’s greed or curiosity and using it to the attacker’s advantage. Its main characteristic is the promise of goods that hackers use to deceive the victims. The attacker either steals the sensitive information or forces malware onto the unsuspecting victim’s device.
Baiting attacks are done in the form of physical and online attacks. In a physical attack, a malware-infected device will be kept in a publicly accessible area where potential victims are known to hang around. These devices will look very authentic and will contain labeling that denotes something very interesting.
An example scenario would be where an attacker leaves a malware-infected pen drive on a common area accessible to the victim. This pen drive would be labeled as something irresistible like high performing clients of the company, or some pornographic material. Once the victim plugs this device onto their computer, the malware infects the host and allows the attacker to take action.
In case of an online attack, the victim will be baited with a “too good to be true” ad that seduces them and leads to malicious sites or encourages users to download a malware-infected application.
Quid Pro Quo
Quid Pro Quo can be identified as a variant of Baiting. Quid pro quo is a Latin phrase used in English to mean an exchange of services. Instead of promised goods, this form of attack will promise a service or an action from the attackers’ end.
One of the most common Quid Pro Quo attacks is when attackers impersonate the US Social Security Administration(SSA). These imposters contact unsuspecting individuals and ask them to confirm their social security number citing technical reasons. Once this has been done, the attackers can easily perform identity theft.
In other cases found by the Federal Trade Commission (FTC), fraudulent actors have set up bogus SSA websites that claim they can help people register for new Social Security cards but actually steal their personal details.
Pretexting
Pretexting is a social engineering attack technique that mainly involves the manipulation of a victim solely based on the trust built. Attackers present themselves usually as someone who has a right-to-know authority like co-workers, police, bank, and tax officials. The attacker then asks questions under the pretext of confirming the victim’s identity and then uses sensitive information for their own use.
Although these attackers mostly gather only personal data, there have been events where attackers have gained security information related to a physical plant.
The success of this form of attack heavily depends on the level of trust the attacker was able to build with their victims. Many sophisticated types of pretexting attacks attempt to trick the victims into an action that allows the attacker to find and exploit a point of vulnerability within an enterprise.
Scareware
Scareware is a type of attack where the victim gets bombarded with popups and emails with false alarms and fictitious threats. These are very common and the least effective. You probably would have seen popups with the text “Your computer may be infected with harmful spyware programs” on several websites. Once you click on these links, you will either be directed to install a “malware removal” application which itself would contain malware or will direct you to a malicious site where your computer becomes infected.
The other type of scareware is pretty commonly found in your email spam box. Your spam box will be filled with emails from senders promising “too good to be true” offers or bogus threats. Your mail server would probably do a good job identified and isolating these emails, and therefore this form of attack is amongst the least effective.
Social Engineering attackers use several strategies to implement their attacks successfully. One of the most common strategies is to offer something irresistible. This strategy will exploit human greed to achieve the desired outcome. Another common strategy would be to fake it till you make it. This strategy involves playing the victim card and eventually making the employee believing in your story. Showing your level of authority is also another strategy used by attackers when impersonating someone. As people tend to respect people with authority — or show authority, this trick works most of the time.
Most Notable Social Engineering Attacks in History
Facebook and Google
Both Facebook and Google were scammed over 100 million USD in a span of over 2 years. A Lithuanian hacker was able to send fake invoices impersonating an Asian vendor of these two companies. This is known as one of the costliest Phishing attacks.
Barbara Corcoran — Shark Tank
Shark Tank judge Barbara almost got caught in a social engineering attack which would have cost her a staggering 400,000 USD. An attacker had impersonated her assistant and contacted her bookkeeper requesting a payment for the renewal of her real estate investments. The attacker had used an email address very similar to the legitimate assistant’s. This fraud was detected when the bookkeeper had contacted the assistant regarding the wire transfer.
Although the money had left Barbara’s account, they were able to freeze the transaction before it reached the attacker’s account in China.
Toyota
Toyota Boshoku Corporation is a Japanese automotive component manufacturer. It is a member of the Toyota Group of companies. They were the victims of a social engineering attack in 2019. They lost around 37 million USD. It is still not known whether Toyota was able to recover the lost money. The attacker was able to convince someone with financial authority to change account information on an electronic funds transfer.
Ethereum Classic
The Ethereum Classic website was hacked in 2017 making users lose thousands of dollars worth of cryptocurrency. The social engineering attackers were able to impersonate the owner of the website and gain access to its domain registry. Once they received the access, they redirected the domain to their own server. The attackers were later able to extract the cryptocurrency from the victims after viewing their private transactions.
Sony Pictures
This social engineering attack was one of the biggest topics during its time. Sony Pictures was under attack in 2014 where it had lost several important documents including business agreements, financial documents, and employees’ information. It was later identified that this attack was a spearfishing attack and the targeted employees were lured using Apple product emails.
How to Stay Safe as an Individual?
- Do not open emails and attachments from suspicious sources. Always make sure to check the email address of the sender. Even an email address from a trusted sender can be spoofed.
- Use multifactor authentication. Attackers are very interested in your login credentials. But if you use multifactor authentication, the attacker will not able to do anything with your credentials alone.
- Be careful about “too good to be true” offers. If an offer sounds too good to be true, do a bit of Googling regarding that topic to get an idea on whether the offer is legitimate.
- Keep your antivirus up to date.
- Always keep your device locked when not in use.
- Always be cautious when talking with people. Think before you speak. You might unintentionally say something that may be confidential.
How to Stay Safe as an Organization?
According to Dan Lohrmann,
- Focus on training your employees, especially the new hires. Ensure that there is a comprehensive security awareness training program in place that is regularly updated to address both the general phishing threats and the new targeted cyber threats. Remember, this is not just about clicking on links.
- Keep regular “roadshow” briefings explaining the latest attack trends. Make sure all levels of employees attend these briefings, including senior executives and those who have authority over financial transactions.
- Hire external independent security teams to audit your company security. These audits should happen regularly.
It is essential that we maintain proper security practices to avoid ourselves and our companies from getting into trouble. As we have seen above, these attacks can be very costly. It is up to us to stay safe from all the nasty eyes around us.
Build & share independent JS components with Bit
Bit is an extensible tool that lets you create truly modular applications with independently authored, versioned, and maintained components.
Use it to build modular apps & design systems, author and deliver micro frontends, or simply share components between applications.
Related Stories
Resources
Social Engineering explained by Josh
Social Engineering by Imperva
Social Engineering Attacks by Nate
Article by Gatefy
Article by David
Common Social Engineering Attack Strategies was originally published in Bits and Pieces on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Bits and Pieces - Medium and was authored by Alicia Jones
Alicia Jones | Sciencx (2021-08-18T14:20:10+00:00) Common Social Engineering Attack Strategies. Retrieved from https://www.scien.cx/2021/08/18/common-social-engineering-attack-strategies-2/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
