This content originally appeared on DEV Community and was authored by Davide 'CoderDave' Benvegnù
In Azure DevOps, you can add checks and pipeline permissions to your repository, to have more control on what pipelines can and cannot do with your code.
And today I'm gonna show you how to do it.
Video
As usual, if you are a visual learner, or simply prefer to watch and listen instead of reading, here you have the video with the whole explanation and demo, which to be fair is much more complete than this post.
Link to the video: https://youtu.be/a7k-mAjTbas
If you rather prefer reading, well... let's just continue :)
Why Protect a Repo?
Today we talk about using Repos as protected resources in YAML Pipelines to have a more granular level of security on them.
So, first things first... why would you even want to use this feature? Let me give you an example.
It is fairly common having multiple repositories in an Azure DevOps project, for example to host many sub-projects, and each repository may have one or more pipelines. In this scenario, by default the Pipelines can access the code on every and each repository in the Team project. You may want however to control which pipelines can access which repositories.
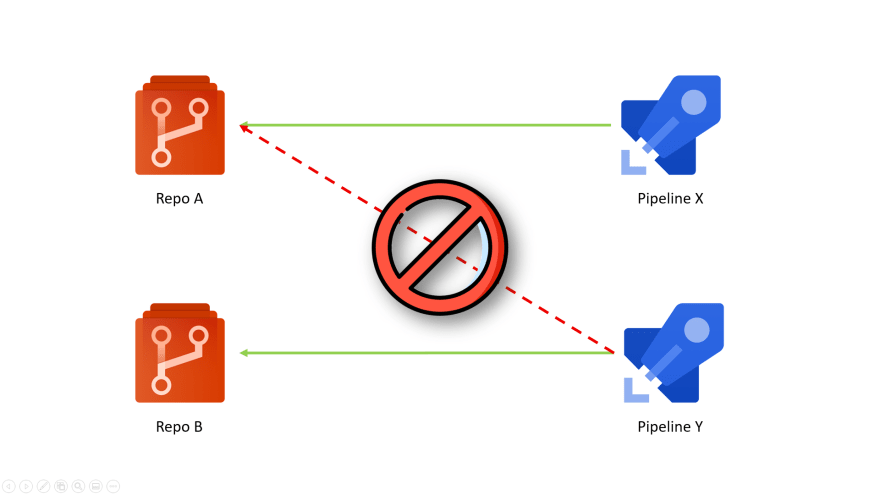
For example, let's say you have two repositories A and B in the same project and two pipelines X and Y that normally build these repositories.
You may want to prevent pipeline Y from accessing repository A. In general, you want the contributors of A to control which pipelines they want to provide access to.
As a contributor of repo A, you can add checks and pipeline permissions to your repository. Let's see how to do this.
How To Do It
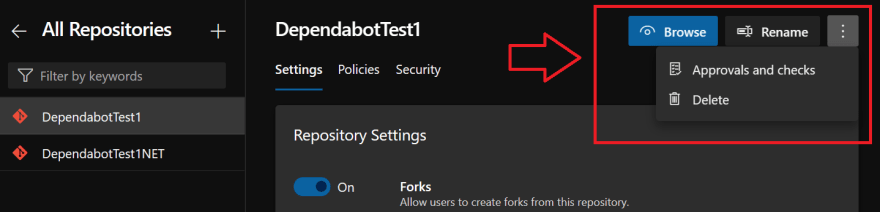
To access those settings, navigate to the Project Settings, select Repositories, and then the repo you want to add checks to.
You will notice a new menu called "Approvals and Checks" in the ellipses, where you can configure any of the approvals and checks like you have on Service Connections, Environments, etc.
And, Under the "Security" tab, you can manage the list of users, pipelines, and even branches and tags that can access the repository.
Anytime a YAML pipeline uses a repository, the Azure Pipelines infrastructure verifies and ensures that all the checks and permissions are satisfied.
Remember that these permissions and checks are applicable only to YAML pipelines. Classic pipelines do not recognize these new features.
Conclusions
Hope this was helpful, let me know in the comment section below if you have any question and what are your scenarios for using this feature.
Also, check out this video here, where I talk about How to disable a repository in Azure Repos and why you may do it.
Like, share and follow me ? for more content:
? YouTube
☕ Buy me a coffee
? Patreon
? Newsletter
? CoderDave.io Website
? Merch
?? Facebook page
?? GitHub
?? Twitter
?? LinkedIn
? Podcast
This content originally appeared on DEV Community and was authored by Davide 'CoderDave' Benvegnù
Davide 'CoderDave' Benvegnù | Sciencx (2021-09-16T16:29:30+00:00) Protect your Repository from Azure Pipelines!. Retrieved from https://www.scien.cx/2021/09/16/protect-your-repository-from-azure-pipelines/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.