This content originally appeared on Level Up Coding - Medium and was authored by David E Lares S
The Internet Protocol is used to address and route datagrams sent between connected machines to a network. This protocol has no guarantees at all and is extremely used in modern computing, specifically in the network spectrum.
Since there are no guarantees, a “new” approach came up to fix that, and that’s the reason why the IPsec framework exists. Internet Protocol Security is a collection of tools to ensure security in IP communications, basically providing security to the IP protocol in many ways, but we can generalize the functionality in datagrams encryption and device authentication with more reach than SSL.
IPSec is available for IPv4 and IPv6 notations with added information to the datagram, in a few words, new headers to the packet.
From all the features IPSec offers it is worth mentioning these foundational elements.
- IPSec provides a mechanism for Encapsulating securing payload (ESP), this encryption is used to guarantee integrity and confidentiality of the transmitted information
- Also provides an authentication header (AH) for integrity and confidentiality too, however, this performs a hash calculation with a secret shared key, the datagram content, and the remaining elements of it.
- A complete key management system, based on the IKE protocol.
The IP datagram
In order to understand how the IP datagram is improved with IPSec, please refer to this image.
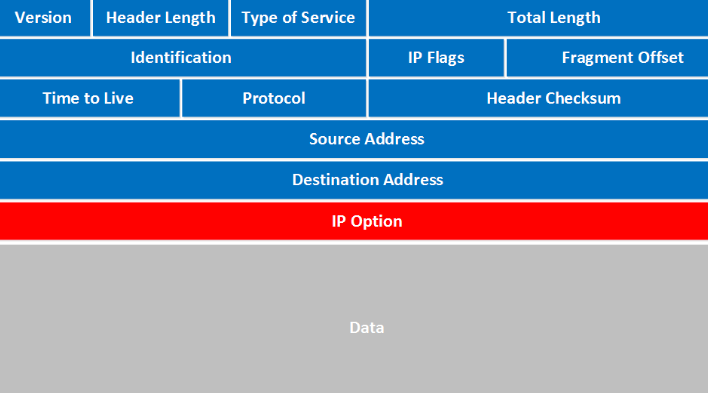
This is a conventional IP datagram header, it contains a lot of information used for identification and the correct delivery of it. Now, let’s explore the new features, most of them are present in IP headers.
Let’s first talk about the IPSec authentication.
The authentication process is achieved by using an identification code addressed to a particular device, this code is available only to authorized devices and prohibits that different devices can participate in the referred communication. The authentication header is not compatible with NAT processes, as a matter of fact, this header value protects the data payload and the complete header itself.
The key management in IPSec helps on avoiding interception and it’s used to decrypt communications. However, it can be applied in devices, VPNs, routers, or tunnels.
Let’s compare the differences.
If you refer to the image above, you will see an IP packet structure in a detail. It’s fully represented by an IP header and the TCP payload, right? With IPSec, this panorama improves a lot.
We have two approaches, the IPSec with ESP and the IPSec with AH
IPSec with ESP
The whole datagram now is composed by.
- IP Header
- ESP
- Encrypted payload
- NH: The Next Header byte(s)
- Sender authentication data
IPSec with AH
This is almost the same thing as the ESP, but, instead of sending the ESP, the AH hash is set instead.
Great. Let’s move on.
When IPSec is implemented in the transport mode, communications between devices are generated, the datagram gets encrypted but the header. At some point, this whole confidentiality and integrity can be compromised.
In this particular mode, NATing processes aren’t allowed because of the AH. Anytime a NAT is done, the hash varies and the integrity of the datagram gets invalidated. A solution for this can be to perform a transversal NAT process, with this, the rest of the routing process remains the same.
Another IPSec usage is found in the Tunneling process, in a few words, this is for IPSec between different networks, and it really doesn’t change a lot, the original datagram is completely encrypted and then gets encapsulated in another plain datagram. This will let you perform NATting in an easy way.
This mechanism is a common method between different separated networks in non-trusted or insecure security.
Nevertheless, this is still the IP protocol but improved, since the routing is made through the IP protocol it can go to/from different ways. IPSec implement indexes and security params to identify data flows, rules, and even algorithms.
Another important component here is the keys exchange and how can be managed. The thing is, that you can perform manual assignations or even automate everything, this can vary based on the size of the network, but it’s not strictly evaluating factor.
The manual key assignation is done to each device typically for small and static networks. The automatic (on-demand) key assignation can be done dynamically between connected devices using the IKE protocol.
This is a simple overview of what you can expect about IPSec and how changes the IP protocol.
Happy networking :)
The IPSec Framework overview was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by David E Lares S
David E Lares S | Sciencx (2022-02-21T02:19:40+00:00) The IPSec Framework overview. Retrieved from https://www.scien.cx/2022/02/21/the-ipsec-framework-overview/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
