This content originally appeared on DEV Community and was authored by SALES
❔ Intro
We are currently working on the following topics :
- Native Docker images delivery through Github Actions, on various registries (mainly GHCR.io and Docker Hub)
- Java native experience : migration to Spring Boot Native & Quarkus experimentations
- Security for our Images Continuous Deployment pipeline
🛡️ Security
For our source code & dependencies, we are applying security strategy thanks to Dependabot :


Dependency management automation with Dependabot
SALES for opt-nc ・ Apr 7 ・ 1 min read
...and GitHub Advanced Security for some repositories.
🖕 Controlling Docker images releases
More and more we release and rely on an ever growing set of Docker images.
To make short, as Software Developers and DEVOPS engineers, the ones that interest us currently are :
- The images we rely on
- The image we build ourselves (on top of previous ones)
👉 What we want need to be able to do is : to be able to control the security level of the images we are building...
⚠️ And not release them if they do not reach the expected level of security, depending of the target service.
As all services do not have the same criticity, vulnerabilities level may have different impacts on runtime security governance.
👐 Experimentation and solutions
Fortunately anchore provides a set of ready to use tools that helps... a lot :
- grype (vulnerability scanner for container images and filesystems)
- syft (CLI tool and library for generating a Software Bill of Materials from container images and filesystems)
-
grypeas a Anchore GitHub Action :
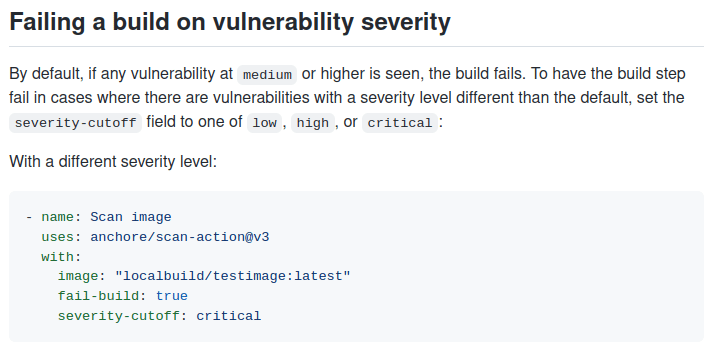
👉 So you can easily protect your Continuous Delivery pipeline thanks to the severity-cutoff :
🤔 Bytecode vs. native impact on security
We wanted to give a quick look at if - and so how - native strategy impacts security, discover the grype output below:
🔖 Resources
A vulnerability scanner for container images and filesystems. Easily install the binary to try it out. Works with Syft, the powerful SBOM (software bill of materials) tool for container images and filesystems.
Join our community meetings!
- Calendar: https://calendar.google.com/calendar/u/0/r?cid=Y182OTM4dGt0MjRtajI0NnNzOThiaGtnM29qNEBncm91cC5jYWxlbmRhci5nb29nbGUuY29t
- Agenda: https://docs.google.com/document/d/1ZtSAa6fj2a6KRWviTn3WoJm09edvrNUp4Iz_dOjjyY8/edit?usp=sharing (join this group for write access)
- All are welcome!
Features
- Scan the contents of a container image or filesystem to find known vulnerabilities.
- Find vulnerabilities for major operating system packages
- Alpine
- Amazon Linux
- BusyBox
- CentOS
- Debian
- Distroless
- Oracle Linux
- Red Hat (RHEL)
- Ubuntu
- Find vulnerabilities for language-specific packages
- Ruby (Gems)
- Java (JAR, WAR, EAR, JPI, HPI)
- JavaScript (NPM, Yarn)
- Python (Egg, Wheel, Poetry, requirements.txt/setup.py files)
- Supports Docker and OCI image formats
If you encounter an issue, please let us know using the issue tracker.
Installation
Recommended
curl -sSfL https://raw.githubusercontent.com/anchore/grype/main/install.sh | sh -s -- -b /usr/local/bin
You can also choose another destination directory and release version for the installation…
This content originally appeared on DEV Community and was authored by SALES
SALES | Sciencx (2022-04-07T22:12:05+00:00) About Java Bytecode, native binaries & security (short Grype benchmark). Retrieved from https://www.scien.cx/2022/04/07/about-java-bytecode-native-binaries-security-short-grype-benchmark/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.