This content originally appeared on DEV Community 👩💻👨💻 and was authored by Marcel.L
Microsoft Security DevOps (MSDO) Overview
Microsoft Security DevOps (MSDO) is a command line application which integrates static analysis tools, for security and compliance into the development cycle.
Today we will take a closer look at how we can use the MSDO GitHub action and how it integrates with Microsoft Defender for DevOps.
MSDO installs, configures and runs the latest versions of static analysis tools. It is data-driven with portable configurations that enable deterministic execution across multiple environments.
The MSDO toolkit can output and convert results to Static Analysis Results Interchange Format (SARIF) which can display the results in your repository on GitHub.
MSDO integrates with Microsoft Defender for DevOps which enables a central console as part of Microsoft Defender for Cloud to provide security teams DevOps insights across multi-pipeline environments, such as GitHub and Azure DevOps.
These insights can then be correlated with other contextual cloud security intelligence to prioritise remediation in code and apply consistent security guardrails throughout the application lifecycle. The benefits of Defender for DevOps, available through Defender for Cloud are:
- Unified visibility into DevOps security posture.
- Visibility of rich security insights to help strengthen cloud resource configurations throughout the development lifecycle.
- Prioritise remediation of critical issues in code.
MSDO tools
At the time of this writing, Microsoft Security DevOps uses the following tools:
| Name | Language | License |
|---|---|---|
| Bandit | Python | Apache License 2.0 |
| Binskim | Binary--Windows, ELF | MIT License |
| ESlint | JavaScript | MIT License |
| Credscan | - | Free during Defender for DevOps preview |
| Template Analyzer | ARM templates, Bicep files | MIT License |
| Terrascan | Terraform (HCL2), Kubernetes (JSON/YAML), Helm v3, Kustomize, Dockerfiles, Cloud Formation | Apache License 2.0 |
| Trivy | Container images, File systems, Git repositories | Apache License 2.0 |
Getting started
Before we dive into the MSDO toolkit we first need to connect our GitHub repository to Microsoft Defender for Cloud.
Log into the Azure portal.
Navigate to Microsoft Defender for Cloud > Environment Settings.
Enter a name, select your subscription, resource group, and region.

Select Next: Authorize connection and Authorize the GitHub connection after reviewing the permission request.

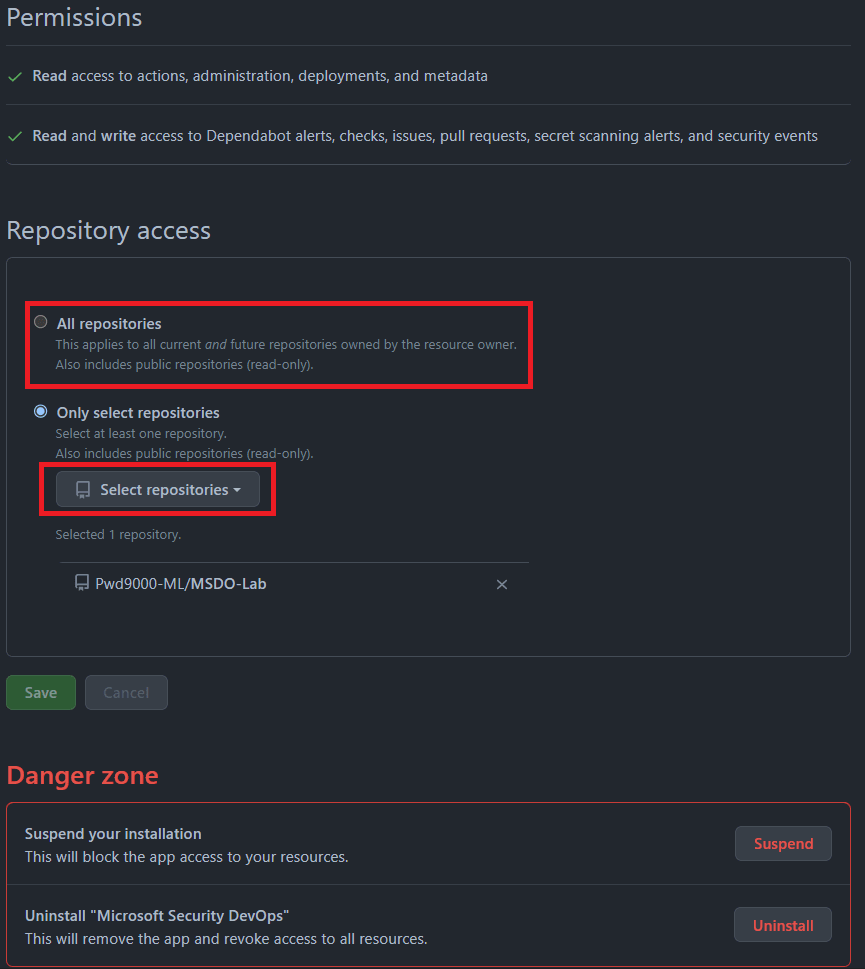
After Authorizing click on Install under Install Defender for DevOps app.

You can install the Defender for DevOps app on All or Individual repositories as necessary.

Select Next: Review and create. Review the information and select Create.
NOTE: You will see the GitHub connector under Microsoft Defender for Cloud > Environment Settings. If you only added one repository and wanted to later change and add/onboard more repositories onto the same Defender for DevOps plan, you can do so by navigating to your GitHub Settings > Applications.
After installing Defender for DevOps on the selected repositories you want to onboard, they will be integrated with Microsoft Defender for Cloud and insights will be accessible from the DevOps Security dashboard under Defender for Cloud in the Azure portal.
Next we will look at the MSDO GitHub action and see how we can use certain tools and populate the dashboard with rich security insights about our code.
NOTE: GitHub Advanced Security features are available on public GitHub repositories. If you are using private repositories, follow this guidance to set up GitHub Advanced Security in your organisation/account.
Configuring the MSDO GitHub action (with Terrascan)
The following examples can also be found on my MSDO-Lab GitHub page.
As mentioned MSDO features a few different tools (I will cover some of the other tools in a future blog post), but I want to concentrate on a specific tool today called Terrascan which is part of the MSDO toolkit.
Terrascan is a static code analyzer for Infrastructure as Code (IaC). Let's take a look at an example on how we can use MSDO integration with Defender for DevOps to get security insights and detect compliance and security violations in a Terraform configuration to mitigate risk before provisioning cloud infrastructure.
On my GitHub repository under the path 01_Foundation I have the following terraform configuration that simply builds a Resource Group and a Key Vault.
### Data Sources ###
data "azurerm_client_config" "current" {}
#Create a Resource Group
resource "azurerm_resource_group" "rg" {
name = var.resource_group_name
location = var.location
tags = var.tags
}
#Create a Key Vault for the Resource Group
resource "azurerm_key_vault" "kv" {
name = "${lower(var.key_vault_name)}${random_integer.kv_num.result}"
location = azurerm_resource_group.rg.location
resource_group_name = azurerm_resource_group.rg.name
enable_rbac_authorization = var.use_rbac_mode
enabled_for_disk_encryption = true
tenant_id = data.azurerm_client_config.current.tenant_id
soft_delete_retention_days = 7
purge_protection_enabled = false
sku_name = "standard"
tags = var.tags
}
resource "random_integer" "kv_num" {
min = 0001
max = 9999
}
Let's take a look at how we can use Terrascan using the MSDO GitHub action to scan our terraform code and how the results will be displayed on the Defender for DevOps dashboard in the Azure portal.
Sign in to GitHub and select a repository you added earlier to Defender for DevOps on which you want to configure the MSDO GitHub action.
Give the workflow file a name. For example,
msdevopssec.yml.
Copy and paste the following sample action workflow into the Edit new file tab.
# My Microsoft Security DevOps (MSDO) Terrascan workflow
name: MSDO windows-latest
on:
workflow_dispatch:
jobs:
MSDO:
# MSDO runs on windows-latest and ubuntu-latest.
# macos-latest supporting coming soon
runs-on: windows-latest
steps:
- name: Checkout
uses: actions/checkout@v2
# Run MSDO analyzers
- name: Run Microsoft Security DevOps Analysis
uses: microsoft/security-devops-action@preview
id: msdo
env:
terrascan_scan: 'scan'
terrascan_outputtype: 'sarif'
terrascan_iacdir: '01_Foundation'
# Upload alerts to the Security tab
- name: Upload alerts to Security tab
uses: github/codeql-action/upload-sarif@v1
with:
sarif_file: ${{ steps.msdo.outputs.sarifFile }}
After creating the workflow you can run it manually under the Actions tab:
After running the workflow you can review the steps. Note that the MSDO toolkit is installed and runs Terrascan against the repo path 01_Foundation containing the terraform IaC configurations.
Let's take a closer look at the MSDO GitHub action being used:
# Run MSDO analyzers
- name: Run Microsoft Security DevOps Analysis
uses: microsoft/security-devops-action@preview
id: msdo
env:
terrascan_scan: 'scan'
terrascan_outputtype: 'sarif'
terrascan_iacdir: '01_Foundation'
How to configure different MSDO analyzers
There are a few ways configure tool inputs:
-
By creating a
*.gdnconfigfile to save configurations:- Great for reuse between team members and local/remote runs.
- Can save multiple tool configurations in a single file to run all configurations.
-
By using environment variables:
- Great for quick configurations in build pipelines.
- They follow the format
[GDN_]<ToolName>_<ArgumentId>, whereGDN_is optional andToolNameandArgumentIdare defined by the tool integration file to (*.gdntool).
As you can see in the workflow step we have specified the tool inputs for (Terrascan) are defined as environment variables on the action itself e.g:
steps:
- uses: microsoft/security-devops-action
env:
<key>: '<value>'
You can see all the different tool inputs/environment variables for the MSDO toolkit on the following Wiki Documentation
Terrascan options
The MSDO GitHub action inputs specifically relating to Terrascan can be found here: https://github.com/microsoft/security-devops-action/wiki#terrascan-options
Defender for DevOps Dashboard
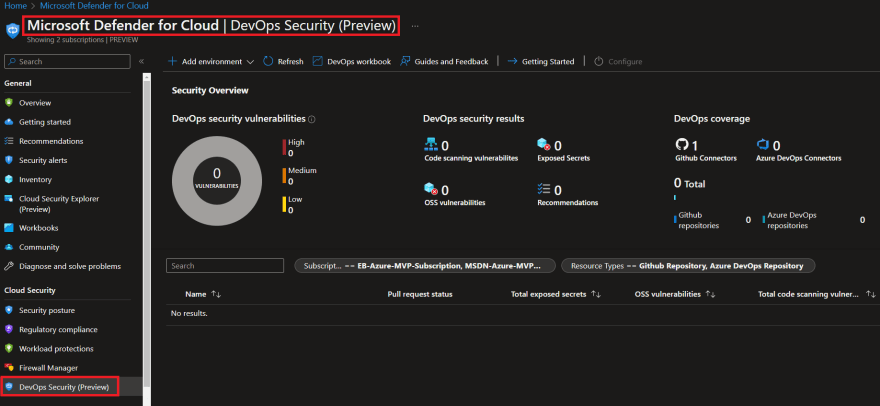
As mentioned MSDO closely integrates with Microsoft Defender for Cloud and has its own 'DevOps Security' dashboard, to review and observe security insights across DevOps and your codebase.
In the Azure portal navigate to Microsoft Defender for Cloud, select the DevOps Security pane and then click on the GitHub connector:
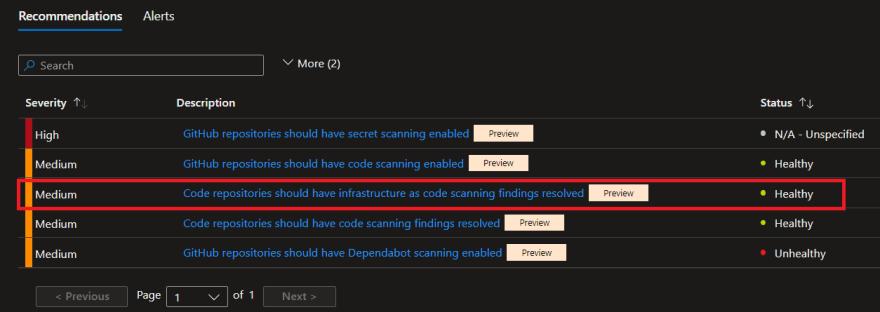
Notice there are some Unhealthy recommendations to resolve detected by MSDO infrastructure as code scanning (Terrascan):
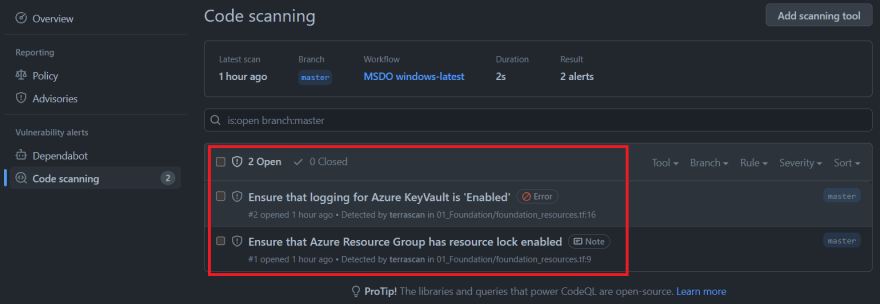
Let's navigate back to the GitHub repository, select the security tab and Code Scanning:
Because we selected the output format to be SARIF and used another action in our workflow; github/codeql-action/upload-sarif@v1 to upload the SARIF file we can now see the MSDO Terrascan results and issues that needs to be resolved directly from the repository Security tab:
Code scanning severities
You can also define code scanning severities which will fail a pull request check to prevent security issues from being committed and introduced into your code.
This can be configured under the GitHub repository Settings > Code security and analysis:
Once the IaC security findings are resolved you will notice that the status of the recommendation on the Defender for DevOps dashboard has changed from Unhealthy to Healthy:
Stay tuned for my next blog post where we will use MSDO on Azure DevOps instead of GitHub and also demonstrate how to use the Azure DevOps MSDO Marketplace extension instead of the MSDO GitHub action, integrating Defender for DevOps on Azure DevOps.
I hope you have enjoyed this post and have learned something new. You can find the code samples used in this blog post on my GitHub page. ❤️
Author
Like, share, follow me on: 🐙 GitHub | 🐧 Twitter | 👾 LinkedIn
This content originally appeared on DEV Community 👩💻👨💻 and was authored by Marcel.L
Marcel.L | Sciencx (2022-10-19T15:31:23+00:00) Defender for DevOps on GitHub (Terrascan edition). Retrieved from https://www.scien.cx/2022/10/19/defender-for-devops-on-github-terrascan-edition/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.