This content originally appeared on Level Up Coding - Medium and was authored by Zied BT
In this article we are going to see how to use “AWS Parameters and Secrets Lambda” Extension. This extension allows to request and cache secrets and parameters during the lifecycle of the Lambda function without requiring use the SDK and to handle caching by ourselves.

We will be building a sample Lambda that references and uses this extension. On the IaC side, we will use CloudFormation in order to use this extension, added as a layer, for that Lambda.
TL;DR
You will find the complete repo here 👉https://github.com/ziedbentahar/aws-parameters-and-secrets-lambda-extension-sample
About Lambda extensions
Lambda extensions can run supporting tools along with a Lambda function. Generally these extensions cover concerns such as security and observability.
They run internally as part of the lambda process or externally as another process in the execution environment and have access to the lambda life-cycle events, allowing to perform actions specific points of the function execution (e.g. retrieving a secret when the lambda runtime is initialized).
Acting as a sidecar, lambda extensions do not require to change your lambda function code. They are provided as Lambda layers.
Using the extension
AWS parameters and secrets extension exposes internal HTTP endpoints to retrieve the secrets or parameters values.
For example, to get the value of a secret named some-third-party-api-key we will need to:
- Query this endpoint GET: http://localhost:2773/secretsmanager/get?secretId=some-third-party-api-key directly in the lambda code. 2773 is the default port for the extension local HTTP server, this can be changed by defining this environment variable PARAMETERS_SECRETS_EXTENSION_HTTP_PORT used by the extension. When querying this endpoint, we need to set this header X-Aws-Parameters-Secrets-Token to the value of AWS_SESSION_TOKEN environment variable.
- Grant the lambda execution role the permission to secretsManager:GetSecretValue for some-third-party-api-key secret
Caching secret value is already handled by this extension. The default cache TTL value is 300 seconds . It is possible to define a custom TTL by setting a value to SECRECTS_MANAGER_TTL environment variable.
You can follow this link for the complete list of the parameters and environment variables supported by this extension.
What are we going to build ?
To illustrate the use of the extension, We are going to build an API providing the weather forecast and air quality given a location (a city name and a country). We will use OpenWeather Api as geocoding and weather provider.
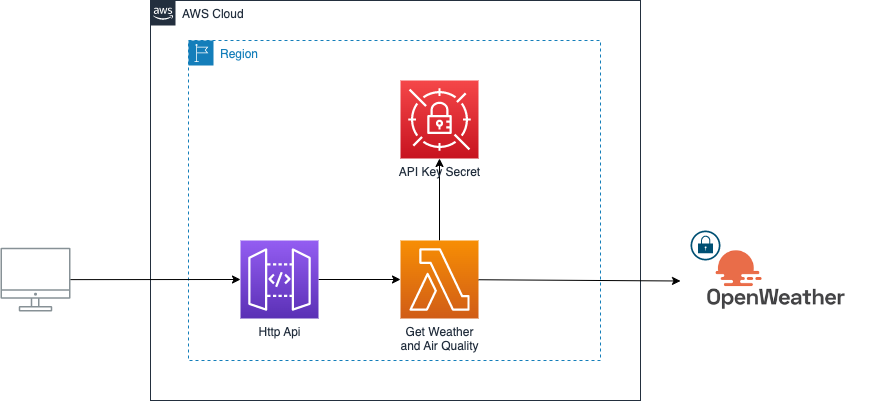
A pretty basic architecture: an AWS Lambda, an API Gateway and a secret containing the API key for OpenWeather API.
We will be using node 16 runtime and typescript for Lambda code.
Let’s see the code
The “get weather and air quality” lambda is quite simple. It gets the city and the country from the request context and calls getWeatherAndAirQualityForCity
getWeatherAndAirQualityForCity will then call OpenWeather API. It needs the API key stored in the Secret.
Here how we use the AWS Parameters and Secrets extension in the Lambda code👇
you will find the full lambda code here
Creating the Lambda resource and using the extension Layer
The relevant bits:
we will need to add the ARN of the extension in the Layers list in order use the extension in the Lambda execution environment.
Since we have a different ARN per region, we are declaring the extensions ARNs as a map of regions:
Regarding the secret
We will inject the secret name as an environment variable OPEN_WEATHER_API_KEY_SECRET_NAME And this lambda function needs to allow secretsManager:GetSecretValue policy to be able to read the secret:
You will find the full CloudFormation template of this lambda function here
Wrapping up
AWS parameters and secrets extension is a nice addition to the lambda ecosystem but it might be not needed for basic use cases (e.g. calling simply the SDK at Lambda startup might be enough on some use cases)
⚠️ An important note: At the time of writing, this extension does not support Lambda with ARM architecture in some regions.
You can find the complete application with a complete CI/CD Github actions workflow here 👉 https://github.com/ziedbentahar/aws-parameters-and-secrets-lambda-extension-sample
Further readings
Using AWS Parameters and Secrets Lambda Extension was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Zied BT
Zied BT | Sciencx (2022-11-03T19:43:40+00:00) Using AWS Parameters and Secrets Lambda Extension. Retrieved from https://www.scien.cx/2022/11/03/using-aws-parameters-and-secrets-lambda-extension/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
