This content originally appeared on Level Up Coding - Medium and was authored by Mohammed Shamim
An overview of syscalls and strace tool
When applications/processes running on Linux want to use the resources managed by the Linux kernel such as — reading files, creating processes, etc. The application process makes system calls to the Linux kernel, The Linux kernel performs the necessary operations, and then leaves control back to the calling program. The strace tool provides the ability to trace system calls on Linux.
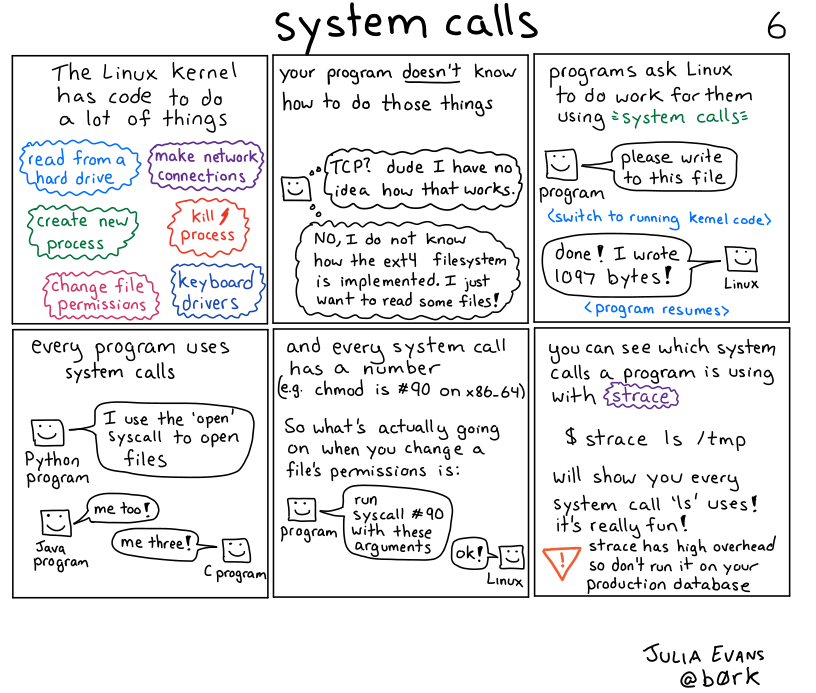
For creating a file in Linux, we can simply run atouch command with the desired filename. It looks so simple, right? But underneath this easy task, there are so many system calls involved. To find out all the system calls we can run the following command :
$ strace touch test.txt
-------------------------------------------------------------------
execve("/usr/bin/touch", ["touch", "test.txt"], 0x7fff42d6fe38 /* 18 vars */) = 0....
After executing the above command we will see a lot of information about the system calls made during the creation of a simple file. We can see that a system call named “execve” is being called and this system call will execute a program residing under “/usr/bin/touch” directory.
View Real-time System Calls by a running process
To trace system calls made by a running process we need to get the PID of the process. And by using the PID of that particular process we can view the real-time system calls made by the process. Let’s get the PID of the “kube-proxy” process:
$ pidof kube-proxy
----------------------------------------------------------------
25166
Now, using the PID we can view the future system calls made by the kube-proxy process:
$ strace -p 25166
-------------------------------------------------------------------
strace: Process 25166 attached
epoll_pwait(4, [], 128, 0, NULL, 140720404847384) = 0
epoll_pwait(4, [], 128, 832, NULL, 140720404847448) = 0
epoll_pwait(4, [], 128, 0, NULL, 140720404847384) = 0
epoll_pwait(4, [], 128, 4999, NULL, 140720404847448) = 0
epoll_pwait(4, [], 128, 0, NULL, 140720404847384) = 0
epoll_pwait(4, [], 128, 4484, NULL, 140720404847448) = 0
getrandom("\x20\xa7\xb0\xd9\x16\x22\x76\x58", 8, 0) = 8
write(11, "\27\3\3\0\"Zl\25dan\2711i\361.K\215\343\207A>\327\5_xZ\370P:H\17"..., 39) = 39
.....
Summary of System Calls
To view a complete summary of how many system calls are being made by a command use the following command:
$ strace -c touch test
-------------------------------------------------------------------
% time seconds usecs/call calls errors syscall
------ ----------- ----------- --------- --------- ----------------
0.00 0.000000 0 1 read
0.00 0.000000 0 6 close
0.00 0.000000 0 2 fstat
0.00 0.000000 0 8 mmap
0.00 0.000000 0 3 mprotect
0.00 0.000000 0 1 munmap
0.00 0.000000 0 3 brk
0.00 0.000000 0 6 pread64
0.00 0.000000 0 1 1 access
0.00 0.000000 0 1 dup2
0.00 0.000000 0 1 execve
0.00 0.000000 0 2 1 arch_prctl
0.00 0.000000 0 3 openat
0.00 0.000000 0 1 utimensat
------ ----------- ----------- --------- --------- ----------------
100.00 0.000000 39 2 total
Check Certain System Calls
To check for certain system calls run the following command:
$ strace -e trace=read touch test1.txt
-------------------------------------------------------------------
read(3, "\177ELF\2\1\1\3\0\0\0\0\0\0\0\0\3\0>\0\1\0\0\0\300A\2\0\0\0\0\0"..., 832) = 832
+++ exited with 0 +++
********************************************************************
$ strace -c -e trace=read,close touch test2.txt
-------------------------------------------------------------------
% time seconds usecs/call calls errors syscall
------ ----------- ----------- --------- --------- ----------------
0.00 0.000000 0 1 read
0.00 0.000000 0 6 close
------ ----------- ----------- --------- --------- ----------------
100.00 0.000000 7 total
If you found this article helpful, please don’t forget to hit the Follow and Clap buttons to help me write more articles like this.
Thank You 🖤
Linux: System Calls and Strace was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Mohammed Shamim
Mohammed Shamim | Sciencx (2022-11-10T03:22:47+00:00) Linux: System Calls and Strace. Retrieved from https://www.scien.cx/2022/11/10/linux-system-calls-and-strace/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
