This content originally appeared on DEV Community 👩💻👨💻 and was authored by openappsec
Written by: Rubaiat Hossain
Web application firewalls (WAFs) are the first layer of defense for protecting your apps or services from threat actors. Amazon Web Services (AWS) WAF is a popular choice due to its seamless integration with other AWS services as well as its ability to protect from a wide range of common attacks.
However, rule-based firewalls, like the one AWS offers, are only as secure as the rules they follow. As a result, traditional WAFs often fail to block sophisticated attacks faced by critical systems. In these cases, it's best to opt for an advanced WAF solution, like open-appsec. open-appsec uses an innovative machine learning (ML)–based threat engine that automatically prevents and blocks suspicious requests.
In this article, you'll compare these two WAFs based on their core feature set, installation experience, documentation quality, ease of use, and pricing and support.
Core Features
AWS WAF and open-appsec both offer a robust set of features for blocking malicious HTTP requests. However, each tool has certain features that the other lacks.
AWS WAF Features
AWS WAF is a security service from AWS that monitors and blocks suspicious traffic using a rule-based system. Rules in AWS WAF are definitions of how to parse the HTTP request for inspection and what to do when a rule matches. You can define rules for inspecting various parts of a web request, including the body, header, and cookie.
In addition, it uses signature-based threat detection to prevent many common web attacks, including SQL injections, cross-site scripting (XSS) attacks, distributed denial-of-service (DDoS) attacks, and botnets.
Traditional Threat Detection
AWS WAF's threat detection model can be effective against both regular and targeted attacks. However, signature-based detection models are reactive by design. As such, AWS WAF only detects known attack types and cannot protect from zero-day attacks. In addition, frequent rule updates are required to block newer threats.
Reliable Rule Sets
The effectiveness of rule-based WAFs depends mainly on the quality of the rules. Therefore, you need a strong rule set to protect your app from complex attacks. The managed rule sets that are included with AWS WAF offer some protection; however, you may still need to create a custom rule set that fits your specific use case.
You can buy these rule sets from the AWS Marketplace or supported partners. However, as you'll soon learn, managed services, like AWS WAF, can quickly become costly if you start purchasing premium add-ons.
Request Inspection with Rules
Another drawback of AWS WAF is that it doesn't support inspecting large chunks of the request body. Instead, it only checks the first 8 KB. This means that if an attacker knows this and includes the payload after the first 8 KB of the request, AWS WAF will not block it in default settings.
You can inspect oversize contents by specifying oversize handling in the component specification. But handling oversize content depends on various factors and must be done correctly. If you're using vendor-supported rules for AWS WAF, you'll need to tune the inspection levels accordingly.
Reliable Bot Control
The AWS WAF Bot Control mechanism provides adequate protection against bot attacks. For instance, it can detect standard and advanced bots based on their signature and heuristics. In addition, you can define rules to enforce various handling methods for bots, including rate limiting, CAPTCHA, and challenge actions.
Moreover, bot visibility is clear on the intuitive Bot Control dashboard, where you can easily block scrapers, crawlers, and other invasive bots. However, you'll need to pay additional fees for using the AWS WAF Bot Control managed rule group.
Fraud Control Prevention
AWS WAF Fraud Control can protect your app's login page from unauthorized sign-in attempts. It secures data and credentials using the managed AWS WAF rule group but also comes at an additional cost.
open-appsec WAF Features
open-appsec is a fully automated WAF solution for securing modern web services and APIs. It uses contextual ML to identify and detect malicious web requests preemptively. This means there's no need for manual rule enforcement or maintenance. Instead, the ML engine of open-appsec learns the behavior patterns of your users through continuous monitoring and uses this information to block anomalies.
Because open-appsec is ML-based, it doesn't need tuning or exception creation like AWS WAF. You can tune some parameters to speed up the learning phase of the contextual ML engine. But this isn't required for blocking common attacks.
Advanced Threat Detection
The default open-appsec installation can stop regular web attacks without additional configurations. In addition, unlike AWS WAF, open-appsec doesn't suffer from attacks that contain payloads after 8 KB of the request body.
Since open-appsec is preemptive by design, you can use it to protect your apps from a wide range of attacks, including OWASP Top Ten, zero-day, and bot attacks. The robust intrusion prevention system also readily protects against over 2,800 Common Vulnerabilities and Exposures (CVEs) without new updates, including severe threats like Log4Shell and Spring4Shell.
open-appsec also identifies and blocks automated bot attacks before intrusion or data theft can occur. In addition, its intuitive software-as-a-service (SaaS) WebUI makes threat visualization clear so you can mitigate problems more effectively.
Cloud-Native
The cloud-native design of open-appsec offers seamless integration with modern continuous integration, continuous delivery (CI/CD) tools.
You can automate everything from installation and upgrades to configuration management using simple APIs or declarative infrastructure as code (IaC). For deployment, you can choose from Helm charts, Kubernetes annotations, or Terraform.
Free and Open Source
Another key feature of open-appsec is that it's open source. Anyone can use this ML-based threat detection engine to protect their web apps and APIs for free.
Installation Experience and Documentation
While features can be beneficial, choosing the right WAF solution for you is more complex. You also need to take into account how the tool is installed, as well as what documentation is available.
To use AWS WAF, you need to set it up and create a web access control list (web ACL) using the AWS console. Then you need to choose the AWS resources that you want to protect and add rules and rule groups that you'll use for filtering traffic.
You can't associate your AWS WAF directly with Amazon EC2 or S3 instances. Instead, you need to associate your AWS WAF with an Application Load Balancer (ALB), which will forward the traffic to your web app.
AWS is a leader in the cloud industry and generally offers good documentation for its services. The AWS WAF documentation covers a broad range of topics, from initial setup to custom rule enforcement. Moreover, AWS also offers whitepapers to support its WAF users.
However, new AWS users may find the documentation too extensive and hard to follow. Some customers also report that they could use more detailed guides on how to best use the rules, as well as a more dedicated configuration process.
In contrast, you can deploy open-appsec as agents for Kubernetes Ingress, Nginx/Nginx Plus plugin, and Docker. Using the interactive command line tool, you can quickly install this WAF for Kubernetes and Nginx.
Advanced users can also use Kubernetes CustomResourceDefinitions (CRDs) for installation. The SaaS management portal makes connecting with deployed agents and managing assets and policies painless.
The open-appsec documentation contains detailed instructions on how to install and set up the WAF. In addition, you'll find information on everything needed to perform day-to-day operations. The reference materials also cover topics on writing Snort signatures and using an Event Query Language (EQL) for log visualization.
Ease of Use
For users with some cloud experience, AWS WAF is easy to use. All you need to get started is an AWS account. In addition, creating and configuring the ACL is also straightforward, thanks to the intuitive wizards.
However, since AWS WAF requires add-ons for additional features, managing this WAF will require a detailed understanding of the components. You'll also need to manage, update, and audit the rule sets to keep up with emerging threats.
In comparison, open-appsec also offers excellent usability, and getting started with this WAF is fast, thanks to its detailed, step-by-step documentation. The interactive CLI tool, open-appsec-ctl, makes deployment straightforward. Once deployed, you can use the centralized SaaS management UI to connect with the agents and set up assets and policies:
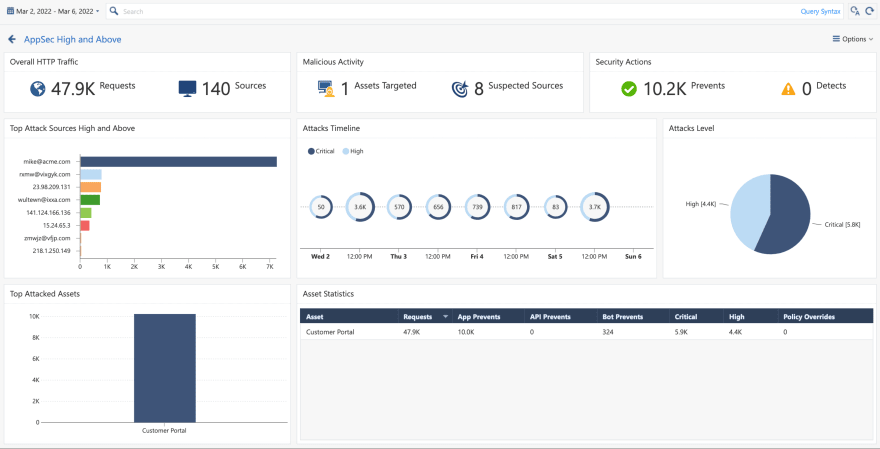
Visualization is available as a single-pane view of important security events. In addition, the monitoring dashboard is intuitive to use and displays valuable statistics about the attacks:
You can click the dashboard controls for in-depth details of events. The Event view gives a tabular view of the events and displays event cards highlighting the incident types, severity, assets under attack, and mitigation steps taken by open-appsec:
You can also filter events based on time ranges. This gives better visibility regarding individual attacks:
Pricing and Support
Cost is an essential factor when choosing a WAF solution. AWS WAF is a relatively cheap option compared to traditional WAF services, like F5 Advanced Web Application Firewall (WAF) and Kona Site Defender from Akamai. Users are charged based on the number of ACLs created, the number of rules in each group, and the volume of requests.
At the time of writing this article, the pricing for AWS WAF starts at $5 USD per ACL, $1 USD per rule, and $0.60 USD per million requests processed. In addition, you'll have to pay additional fees for AWS WAF Bot Control and AWS WAF Fraud Control services and any purchased rules. Moreover, if you want dedicated support, you need to sign up for a support plan with AWS, which will also increase the cost.
This pricing model can be a bit confusing for new AWS users. So you can use the AWS Pricing Calculator to get an idea of how much it would cost to protect your application with AWS WAF.
In contrast, open-appsec is a fully open source solution that offers all the core features, including the ML-based detection engine, for free, and this version is more than enough to get you started.
If you want more advanced protection and dedicated support, consider signing up for CloudGuard AppSec, the enterprise version of open-appsec. You can explore the available plans from their Pricing page.
Conclusion
AWS WAF and open-appsec are both great options for protecting your apps. They can detect and block many common attacks that would otherwise cause service disruption. However, both of these tools perform their tasks differently.
AWS WAF is a rule-based solution that integrates easily with other AWS services and offers managed and custom rules for effective blocking.
In contrast, open-appsec uses a modern, ML-based threat detection engine to detect attacks preemptively. This means that there's no need to write rules or manage them. Moreover, the proactive nature of open-appsec allows engineers to focus more on development than security. open-appsec also blocks many severe threats, like the Log4Shell and Spring4Shell vulnerabilities, in default settings.
This content originally appeared on DEV Community 👩💻👨💻 and was authored by openappsec
openappsec | Sciencx (2022-12-15T18:00:31+00:00) AWS WAF vs. open-appsec ML-Based open source WAF. Retrieved from https://www.scien.cx/2022/12/15/aws-waf-vs-open-appsec-ml-based-open-source-waf/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.