This content originally appeared on Level Up Coding - Medium and was authored by Andree Toonk
Welcome to the world of modern infrastructure, where things are always changing and moving at lightning speed. As engineers, we know that managing access to dynamic and ephemeral services can be a real pain. Whether you’re working with multiple cloud providers, virtual machines that come and go, or using container orchestration systems like Kubernetes, keeping track of all your resources can be a daunting task. But don’t worry, we’ve got you covered with the Border0 connector.
The border0 connector
The Border0 connector is like a superhero for your infrastructure. It can automatically discover your resources such as Web applications, SSH servers, or MySQL and Postgres database services based on tags or labels. And once it discovers these resources, it makes them automatically available through Border0, making it easy to manage and control access to your services. All you need to do is attach the right label or tag, and the Border0 connector will take care of the rest.
In other words, the Border0 connector helps you discover and manage access to your services, all you need to do is attach the right label or tag. No human intervention needed, all fully automated!
A few example use-cases
Let’s say you’re an imaginary company that relies heavily on AWS EC2 instances. You have hundreds of instances that come and go all day long, and keeping track of which ones each engineer should have access to and which ones don’t can be a real headache. With the Border0 connector, you can set up a system where instances are automatically discovered and made available to the right users based on their tags.
This way, you don’t have to worry about manually configuring access for each instance. The Border0 connector takes care of it for you, and you can easily control access to your instances based on their tags.
Connector Plugins
The Border0 connector is not a one-trick pony, it has various plugins that can be used to discover resources and make them available. For example, you can use the Static Sockets plugin, which is the easiest and most straightforward method. Simply define all targets in a YAML config file. Or you can use the AWS EC2 plugin, which will find all EC2 instances and use the AWS tags attached to the instance to determine if any services (HTTP, SSH, etc.) should be made available through Border0.
Another popular plugin is the Docker plugin, which scans your Docker host for all containers. Using the Docker tags attached to the container, the connector will determine if any services should be made available through Border0. Additionally, there is a Kubernetes plugin that uses the same methodology as the EC2 and Docker plugins but for Kubernetes, making it easy to make pods available. And lastly, the Network Discovery plugin periodically scans your network for the ports you define and makes the discovered open ports in your private network available as services through Border0.
Make sure to check out the Connector documentation and examples on our documentation page here to learn more about each plugin. https://docs.border0.com/docs/config-template
A demo: AWS EC2 and The border0 connector
To see the Border0 connector in action, let’s take a look at a real-life example. Imagine we have a private AWS VPC with a handful of EC2 instances. Our engineering team needs to be able to SSH into these instances, and since we’re using Border0, we don’t need to use a VPN. Instead, we can authenticate using just our existing SSO credentials, eliminating the need to ship SSH keys around for each user.
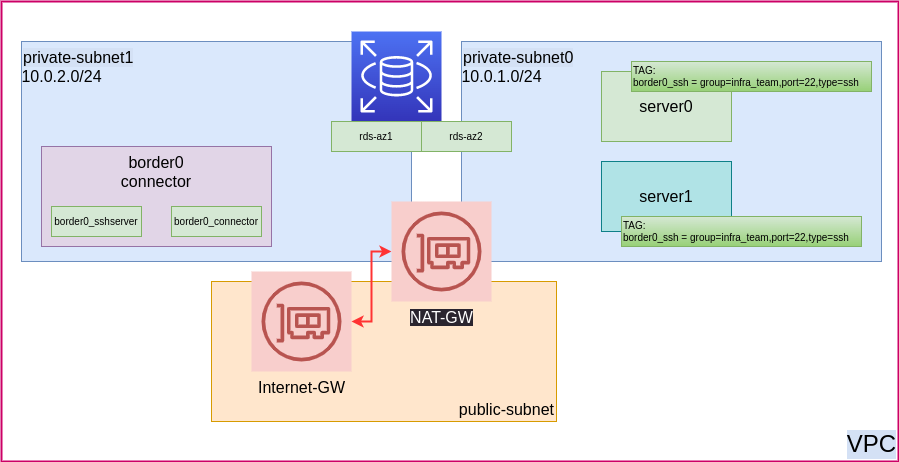
The diagram above shows our simple example. In this example, we have a VPC, with two EC2 instances (server0, server1) in a private subnet. We also have an RDS instance in a private subnet, and finally the Border0 connector, also in a private subnet. So note, these are not directly accessible from the Internet and only have egress network access through the AWS NAT gateway. Our terraform example will make sure this is all provisioned for you.
In this example, we’re using a static socket definition for the RDS instance, while for the EC2 instances, we’ll use the EC2 plugin. This means the EC2 instances will be made available based on the attached labels, in this case:
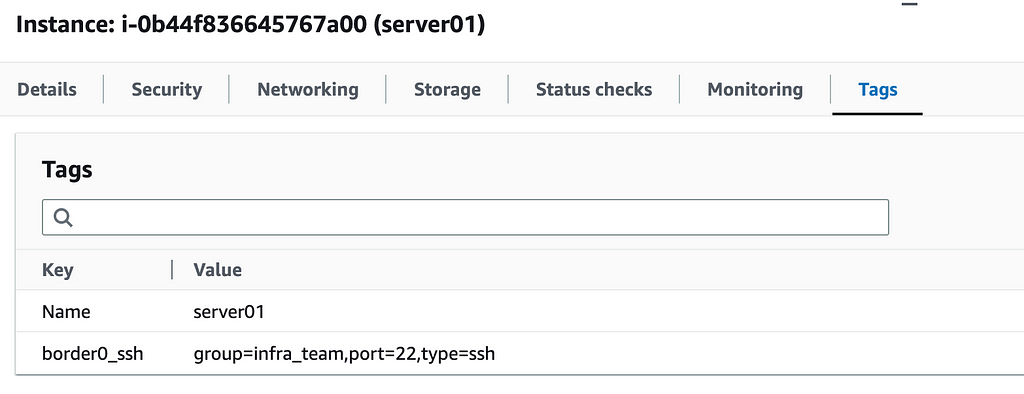
Finally, this is what the connector config file looks like:
connector:
name: border0-connector
aws-region: us-west-2
ssm-aws-region: us-west-2
credentials:
token: yourBorder0Token
sockets:
- border0-rds-via-border0-connector:
database_credentials: aws:ssm:/border0/demo-rds-secret-params
type: database
port: 3306
aws_groups:
- group: infra_team
In this simple example configuration, the connector will scan the EC2 api and find all EC2 instances with the label border0_ssh, where the group is infra_team. In this example we’re using the default organization policy. However, if we wanted to we can attach one or more policies of our choice to the detected resources.
To start this, we’ll start the connector on the connector instance like this:
border0 connector start
And boom, your private RDS instance and the private EC2 instances are available through Border0. No need for a VPN and access is controlled using the users’ SSO credentials and the flexible Border0 policy.
Try it yourself
To make it easy to test this out for yourself, we’ve created a terraform file that will bring up this example in your own AWS account. It includes the creation of a private VPC, NAT GW, subnets, RDS, the EC2 instances and the connector instance (with Border0 cli and yaml), and the correct SSH config. Simply run the following commands and you’ll be able to play with the example yourself. You can find the example code on our GitHub here.
border0 login
terraform init
terraform apply \
-var="aws_region=us-west-2" \
-var="border0_token=$(cat ~/.border0/token)" \
-var="border0_org_cert=$(border0 organization show | grep ecdsa-sha2-nistp256 | awk '{print $5,$6}')"
Heads up, it may take a few minutes for this terraform to complete, this is because it takes a while for RDS to come up.
Wrap up
In this blog post we introduced the Border0 connector. The connector is a powerful tool for managing access to your dynamic, ephemeral services in a secure and simple way. Best of all, it can integrate with your existing automation workflow. With the help of the various plugins available, you can easily discover and make available services running on AWS, Docker, Kubernetes, and more. Easily discover and manage access to your services by simply attaching the right label or tag.
With Border0, you can authenticate using your existing SSO credentials, eliminating the need for VPNs, SSH keys and shared database credentials. So, if you’re looking for a more efficient and secure way to manage access to your services, give the Border0 connector a try. We invite you to give it a spin yourself and sign up for our free, fully-functionalcommunity edition here!
Finally, don’t forget to check our documentation for more examples and information: https://docs.border0.com/docs/config-template
Meet the Border0 Connector: The Superhero for Managing your Dynamic Infrastructure was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Andree Toonk
Andree Toonk | Sciencx (2023-01-26T21:42:07+00:00) Meet the Border0 Connector: The Superhero for Managing your Dynamic Infrastructure. Retrieved from https://www.scien.cx/2023/01/26/meet-the-border0-connector-the-superhero-for-managing-your-dynamic-infrastructure/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
