This content originally appeared on DEV Community and was authored by Andree Toonk
This article was originally published on the Border0.com blog.
Amazon Relational Database Service (RDS) is a popular, fully managed database that's become the database of choice for many. These databases typically contain sensitive data, so isolating the database in private VPCs is a pretty typical and wise architecture. But this setup comes at a cost, since it’s isolated, it also makes life harder for human database administrators and engineers who need access. That's where Border0 comes in, offering the perfect combo—an isolated AWS RDS database in a private VPC for that peace-of-mind security while also providing easy access to only those who need it, as if the database was right under their desk. And the best part? No security compromises! It's a win-win!
In this blog, we'll delve into the challenges of accessing RDS databases in a private VPC and demonstrate how to solve this and easily access your private database using Border0, a zero-trust access solution for accessing RDS. Using Border0, you can ditch those clunky traditional methods like VPNs, shared database credentials and make it super easy for your team to access databases anytime, anywhere.
The Challenge: Accessing RDS Databases and shared credentials.
Making an AWS RDS database accessible to engineers and administrators to access the database for routine tasks or troubleshooting typically comes with two challenges. First, network access, and second, database credentials. Let's take a look at each of these.
Keeping RDS databases in private VPCs is a smart move for security. But the obvious downside is that engineers and admins have a tough time getting into the database for everyday tasks, troubleshooting, or maintenance. The usual solutions - setting up VPNs, bastion hosts, or jump boxes - are far from ideal. They're time-consuming, clunky, create friction, and are not providing the security efficacy needed. For example, it's hard to determine who accessed the database at any given time.
The second challenge is the challenge of shared database credentials. It's still common practice to access databases using shared credentials, typically because most databases don't support SSO. This common practice complicates the process of periodically rotating credentials and makes it difficult to determine who has access to them. Furthermore, shared database credentials hinder auditability and accountability. When multiple individuals connect to the database using the same shared user, attributing specific queries to specific individuals becomes a daunting task.
Using Border0, we can solve both of these challenges. We'll make it super easy for engineers to access the RDS database, even if they're in a private VPC, without the need for a VPN. We also eliminate the need for shared credentials, and users can use their existing Single Sign-On credentials to log in to the RDS database. Finally, using Border0, you'll know exactly who accessed your database, from where and when, and what queries were executed.
A Step-by-Step Guide to Accessing RDS Databases with Border0
Alright enough talk, let’s get our hands dirty and walk through the process of using Border0 to access an Amazon RDS database.
In this example we'll use MySQL, but Postgres is supported as well. We'll assume you already have an RDS (MySQL) database instance, as well as either an EC2 or container that has access to RDS and will act as a connector. We also assume this connector already has the border0 cli tool installed.
The first step is to create a configuration file for the border0 connector, this is an example:
ubuntu@connector01:~$ cat border0.yaml
connector:
name: "my-rds-connector"
credentials:
token: YOURTOKENGOESHERE
sockets:
- rds-us-east-2:
port: 3306
host: my-rds-instance.cluster.us-east-2.rds.amazonaws.com
type: database
policies: [demo-rds-policy]
upstream_type: mysql
upstream_user: border0_user
upstream_password: AVeryLongAndSecurePasswordThingyTokenLikeStuff
In this example, we'll define all the information the connector needs to make the RDS instance available through the Border0 cloud. Also, notice that a policy called demo-rds-policy is referenced. This policy defines who will have access to the database and under what conditions.
Next, let's start the connector.
border0 connector start --config /etc/border0/border0.yaml
That's it! Users should now be able to connect to this private RDS database using their favorite database client. Border0 integrates with various popular database clients making it easy for users to discover and connect to their RDS instances without changing their toolset.
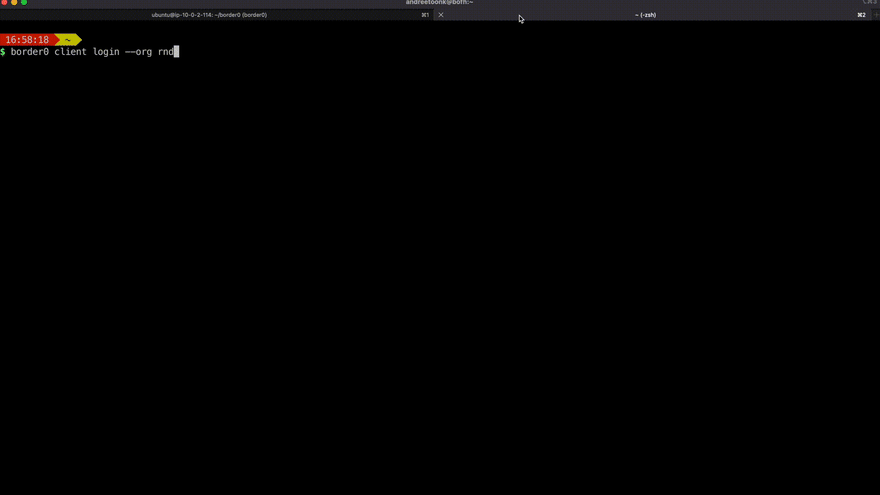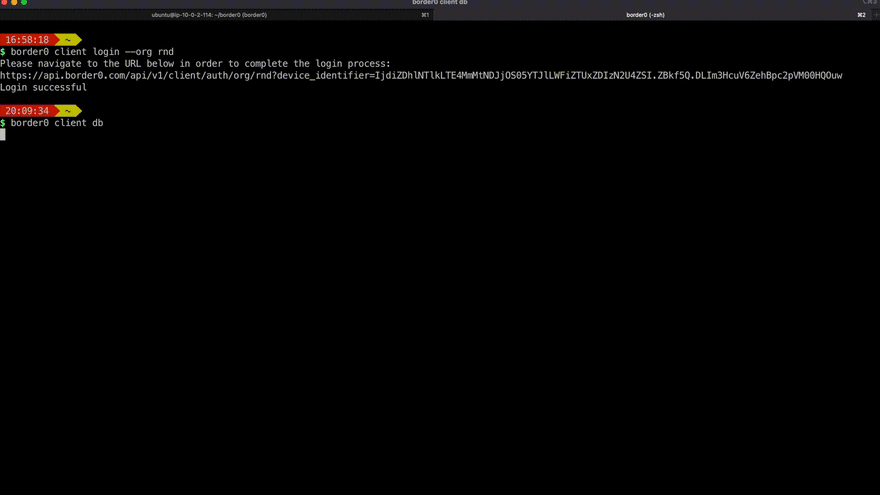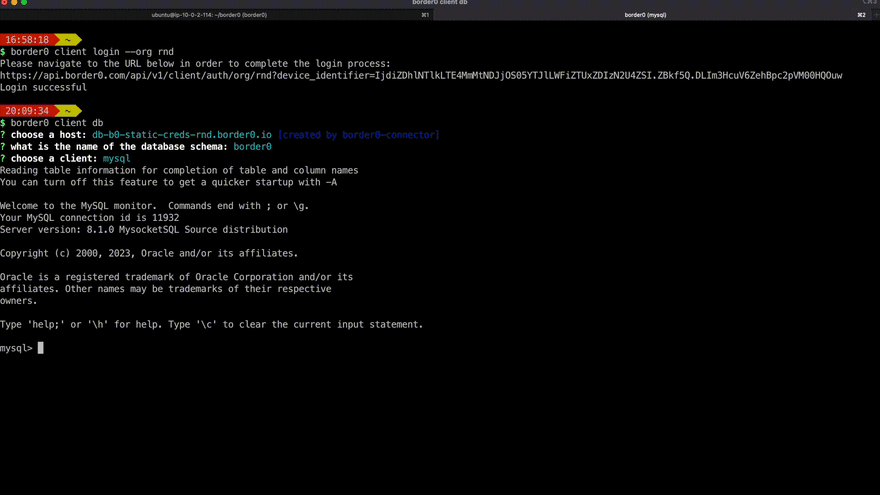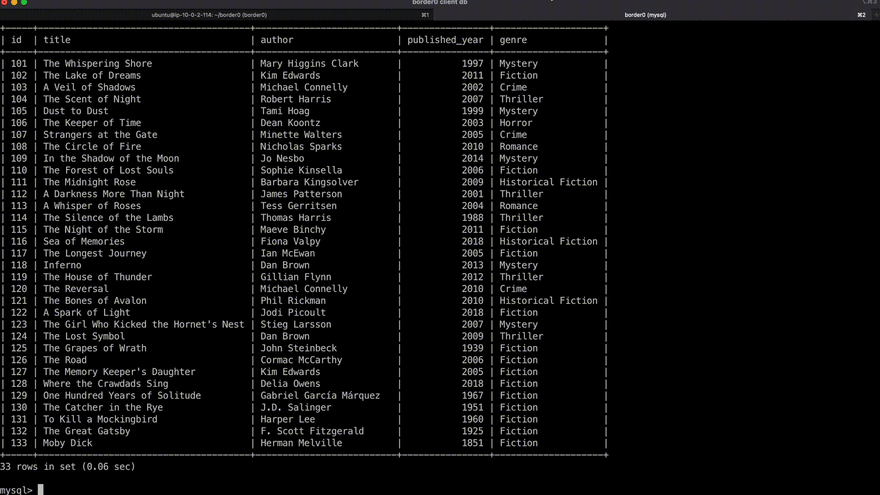 Discovery of databases a user has access to, and quick access using their favorite database client
Discovery of databases a user has access to, and quick access using their favorite database client
Secure secrets storage
We can make two more security improvements. Since we're using AWS, we can use SSM to store and retrieve secrets such as the Border0 token and the database credentials. This way, we don't need to define them in our config file statically. Less plain text secrets are better! In the example below, we've removed all secrets. Instead, we point to the SSM location that holds these secrets. All you need to do is ensure the connector host has the right role.
ubuntu@connector01:~$ cat border0.yaml
connector:
name: "my-rds-connector"
ssm-aws-region: "us-east-2"
credentials:
token: aws:ssm:/path/to/the/connector-token
sockets:
- rds-us-east-2:
port: 3306
host: my-rds-instance.cluster.us-east-2.rds.amazonaws.com
type: database
policies: [demo-rds-policy]
upstream_type: mysql
upstream_user: aws:ssm:/path/to/the/username
upstream_password: aws:ssm:/path/to/the/password
RDS IAM authentication
The last security improvement is for the connector to use AWS IAM authentication to connect to the RDS instance. Border0 supports integration with AWS IAM authentication with RDS. This way, all you need to do is give the EC2 or container host the proper role, and boom, success 🙌 One less secret to manage.
Example of using Border0 with SSM and RDS IAM authentication:
ubuntu@connector01:~$ cat border0.yaml
connector:
name: "my-awesome-connector"
ssm-aws-region: "us-east-2"
credentials:
token: aws:ssm:/path/to/the/connector-token
sockets:
- db-b0-iam-creds:
type: database
port: 3306
policies: [demo-rds-policy]
host: aws:ssm:/border0/demo-rds-address
upstream_type: mysql
upstream_user: Border0ConnectorRDSUser
rds_iam_auth: true
aws_region: us-west-2
For more details on the various configuration options and for how to use Border0 with RDS and configure the correct AWS policies, see docs.border0.com
Wrap up
In this blog, we explored how Border0 revolutionizes the way organizations handle database access, discovery, and auditability, regardless of where your database is hosted. We demonstrated how Border0 enables users to access private AWS RDS databases without the need for a VPN and using just their SSO credentials, making it easy to define access conditions and eliminate shared accounts. This significantly improves the user experience for engineers, boosting their productivity while also improving your security posture, visibility and control.
With Border0's Desktop app or CLI, users can quickly discover accessible database servers and connect to them using their favorite tools and workflow. Furthermore, administrators gain valuable insights into who accessed which databases, from where, and when, as well as the executed queries. This level of detail is a considerable improvement compared to the current status quo, where shared credentials often obscure who executed specific queries.
Border0 provides a secure, streamlined solution for accessing RDS databases in private VPCs, making it the ideal choice for organizations aiming to enhance their security posture without sacrificing convenience. By adopting a zero-trust model and leveraging Border0, you can simplify RDS access for your administrators and engineers while maintaining top-notch security.
We encourage you to experience the benefits of Border0 for yourself by signing up for our free, fully-functional community edition here. Also, make sure to check the RDS-specific documentation on our docs page ; following these steps, you'll have your database accessible in just 2 minutes! So, try Border0 today and transform the way your organization manages database access, security, and auditability.
This content originally appeared on DEV Community and was authored by Andree Toonk
Andree Toonk | Sciencx (2023-03-21T21:03:20+00:00) How to access a private AWS RDS database. Retrieved from https://www.scien.cx/2023/03/21/how-to-access-a-private-aws-rds-database/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
