This content originally appeared on text/plain and was authored by ericlaw
While it’s common to think of cyberattacks as being conducted by teams of elite cybercriminals leveraging the freshest 0-day attacks against victims’ PCs, the reality is far more mundane.
Most attacks start as social engineering attacks: abusing a user’s misplaced trust.
Most attackers don’t hack in, they log in. The most common cyberattack is phishing: Stealing the user’s password by asking them for it.
The next most common Initial Access Vector is socially-engineered malware: sending the user a malicious file and asking them to open it. When the malicious file runs, it disables security defenses, downloads more malware, and begins stealing data and performing other malicious activities.
Attackers have many choices for deploying their malware — on Windows, they can write evil executable files (.EXE, .SCR, .COM, etc) or installers (.MSI, .MSIX, etc).
However, for simplicity and compatibility reasons, one of the most common initial access choices for attackers is a file targeting the legacy scripting engines (.JS, .VBS, .HTA, .WSH).
Legacy Script Engines
These scripting file types, created alongside Internet Explorer in the 1990s, have been supported for almost 30 years now, and they still work on the latest versions of Windows. Unlike JavaScript running in your browser, these file types run outside of your browser, with no sandbox constraining their ability to reconfigure your system and steal your files.
- JavaScript running in Chrome or Edge cannot read a file from your desktop without your explicitly selecting that file, whereas JavaScript running inside
wscript.execan read every file from your desktop, download and run any program without any prompts, and so forth. - VBScript no longer runs in browsers, but the Windows Scripting engines (
cscript.exeandwscript.exe) are perfectly happy to run VBS files and provide full access to your system. - You can think of a
HTAfile as a prehistoric Electron app — it’s basically Internet Explorer with no sandbox and all of the security features turned off.
This level of power is, in a word, totally  bananas
bananas .
.
Why does it still exist?
Legacy compatibility.
User Experience
In Edge, the .HTA file type is marked as DANGEROUS and thus HTA downloads are blocked by default:
…but even blocked files can be sent to the user inside an archive (e.g. a ZIP File) and the user need only open the ZIP to be able to get at the HTA within.
In contrast, Chrome treats the HTA type as ALLOW_ON_USER_GESTURE and does not block .HTA downloads:
Reading the source, you can see that Chrome does not treat any of these file types as dangerous:
file_types {
# HTML Application. Executes as a fully trusted application.
extension: "hta"
platform_settings {
platform: PLATFORM_TYPE_WINDOWS
danger_level: ALLOW_ON_USER_GESTURE
}
}
file_types {
# JavaScript file. May open using Windows Script Host with user level privileges.
extension: "js"
platform_settings {
platform: PLATFORM_TYPE_WINDOWS
danger_level: ALLOW_ON_USER_GESTURE
}
}
file_types {
extension: "vbs"
platform_settings {
platform: PLATFORM_TYPE_WINDOWS
danger_level: ALLOW_ON_USER_GESTURE
}
}After you click open, the only thing standing between your PC and the potentially malicious code is a 2003-era security prompt:
After the file starts running, your security software may be able to catch malicious behavior at runtime using a feature called the Antimalware Scan Interface, but I wouldn’t bet my PC on it.
A Smarter and Safer Future?
The new Windows 11 Smart App Control feature dramatically reduces the threat of an attacker sending the victim a simple script or batch file that takes over their PC. A wide swath of file types, including scripts (.js,.vbs,.hta,.ps1), batch commands (.bat,.cmd) and numerous other dangerous types are blocked from running if they came from the web.
Mitigations
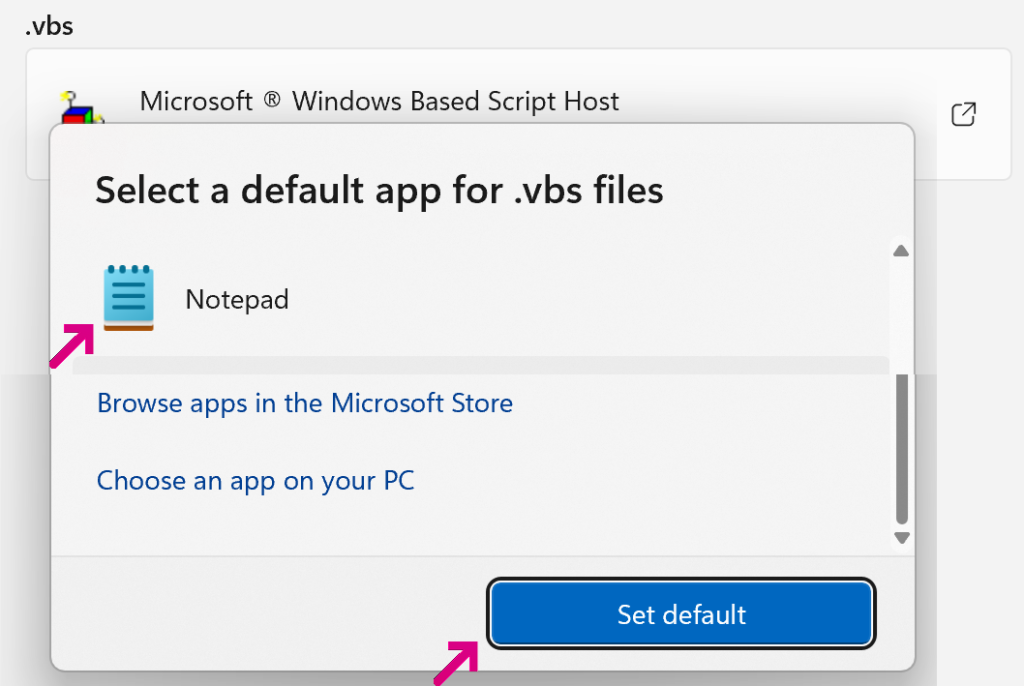
You can easily block attacks against the legacy scripting engines today. There are numerous ways to do so, but perhaps the simplest approach which blocks browser and email attack vectors is to point the file types at a safe application (e.g. Notepad).
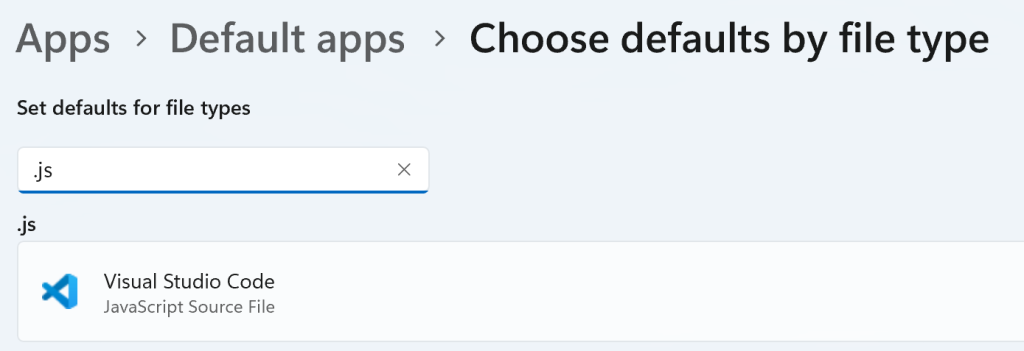
To do so, simply open the Windows Settings’ app and navigate to Choose defaults by file type. Search for a type:

Click the arrow icon, scroll the app list to pick a safe handler, then click Set default:
After fixing VBS, fix the other types:

In the unlikely event that you ever need to run one of these files inside its original handler, you can easily do so from the command line. Just run e.g. mshta.exe theApp.hta or cscript.exe myScript.js to run the file.
Stay safe out there!
-Eric
This content originally appeared on text/plain and was authored by ericlaw
ericlaw | Sciencx (2024-05-20T18:19:15+00:00) Attack Techniques: Full-Trust Script Downloads. Retrieved from https://www.scien.cx/2024/05/20/attack-techniques-full-trust-script-downloads/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.