This content originally appeared on DEV Community and was authored by Manoj Gohel
This article delves into a comprehensive comparison of Paseto and JWT, dissecting their core functionalities, security features, and potential drawbacks.
APIs and modern web applications have brought token-based authentication to the forefront of secure authorization methods.
Offering advantages like scalability, statelessness, and enhanced security compared to traditional session-based authentication, tokens have become the preferred choice for developers worldwide.
Among various token-based approaches, JSON Web Token (JWT) has gained widespread popularity because of its simplicity and ease of implementation.
However, concerns surrounding potential vulnerabilities and the need for meticulous implementation have led to the exploration of more robust alternatives.
Paseto (Platform-Agnostic Security Tokens) has emerged as a better solution, directly addressing the shortcomings of JWT.
Designed with a focus on security, Paseto provides a more secure foundation for token-based authentication by mitigating vulnerabilities and enforcing secure defaults.
This article delves into a comprehensive comparison of Paseto and JWT, dissecting their core functionalities, security features, and potential drawbacks.
By analyzing their respective strengths and weaknesses, aiming to equip you with the knowledge to make informed decisions regarding token-based authentication in their projects
How Does Token-Based Authentication Work?
Token-based authentication provides a secure and efficient way to manage user access in modern applications. Unlike traditional session-based methods that rely on server-side storage, token-based systems issue tokens to clients upon successful authentication.
Let’s break down the typical flow:
- User Login: The user initiates the process by providing their credentials (username and password) to the application.
- Authentication: The application validates these credentials against a database or other authentication mechanism, verifying the user’s identity.
- Token Generation: Upon successful authentication, the application generates a unique, digitally signed token containing relevant user information and permissions. This token acts as a secure representation of the user’s identity and access rights.
- Token Delivery: The application sends the generated token to the client, usually included in the HTTP response header or body.
- Client-Side Storage: Here the client securely stores the received token, often in local storage, session storage, or cookies, for use in subsequent requests.
- Resource Requests: When the client needs to access a protected resource, it includes the token in the authorization header of the HTTP request. This signals to the server that the client is attempting to access a restricted area.
- Token Verification: When a request with a token is received, the server confirms its validity and integrity by utilizing the corresponding secret key or public key for the token’s signing algorithm.
- Access Control: Based on the validated token and its embedded permissions, the server determines whether the client has the necessary authorization to access the requested resource. If authorized, the server grants access and fulfills the request. Else, access is denied.
Let’s visualize the flow:
A flowchart illustrating the token-based authentication process
What is JWT?
============
JWT stands for JSON Web Token. It’s an open standard (RFC 7519) defining a compact and self-contained method for securely transmitting information between parties as JSON objects.
JWTs are commonly used to verify user identities and granting access to private resources. Also with JWT you can securely share information between applications.
A JWT comprises three parts:
Header: This defines the token type (JWT) and the signing algorithm used. Example,
{
"alg": "HS256",
"typ": "JWT"
}
Payload: It contains statements about an entity (typically, the user), and additional data. Example,
{
"sub": "1234567890",
"name": "John Doe",
"iat": 1516239022
}
Signature: This verifies the token’s authenticity and integrity. Its created by combining the encoded header, encoded payload, a secret, and the specified signing algorithm. Example (using HMAC SHA256):
HMACSHA256(
base64UrlEncode(header) + "." +
base64UrlEncode(payload),
secret)
How JWT Works?
==============
The process involves:
- Token Generation: Upon successful user authentication, the server generates a JWT containing user information and permissions. This token is signed using a secret key.
- Token Sent to Client: The server sends the JWT to the client, usually within the HTTP response header.
- Client Stores Token: The client securely stores the JWT, often in local storage or cookies.
- Client Requests Resource: The client includes the JWT in the authorization header for subsequent requests to private resources.
- Server Validates Token: The server validates the JWT’s signature and expiration time by using the secret key.
- Access Granted/Denied: Based on the token validation, the server grants or denies access to the requested resource.
Pitfalls Of JWT
While JWT offers many advantages, it’s essential to be aware of potential pitfalls and security concerns that can arise if not implemented properly.
Here are some key issues associated with JWT tokens:
Algorithm Confusion
JWT allows for flexibility in choosing signing algorithms, including the option of “none”.
If developers mistakenly set up their applications to accept unsigned tokens, it can make them ineffective and vulnerable. Attackers could exploit this by forging tokens with arbitrary claims.
Key Management Issues
It’s security system heavily relies on proper key management. Weak keys or improper storage can compromise the entire system.
A leaked or compromised keys allow attackers to forge tokens or decrypt sensitive information.
Lack of Built-in Revocation
JWTs are stateless, meaning the server doesn’t maintain a record of issued tokens.
Revoking tokens before they expire can be a challenge, especially in cases of compromised keys or user logout.
Bypassing Signature Verification
Vulnerabilities in certain JWT libraries and implementations allow for signature verification to be bypassed.
These vulnerabilities could enable attackers to create forged tokens that appear legitimate to the application.
What is PASETO (Platform Agnostic Security Token)?
Paseto, which stands for Platform-Agnostic Security Tokens, is a specification for secure stateless tokens.
It provides a modern and better alternative to JWT, addressing some of its inherent vulnerabilities and emphasizing secure defaults and ease of implementation.
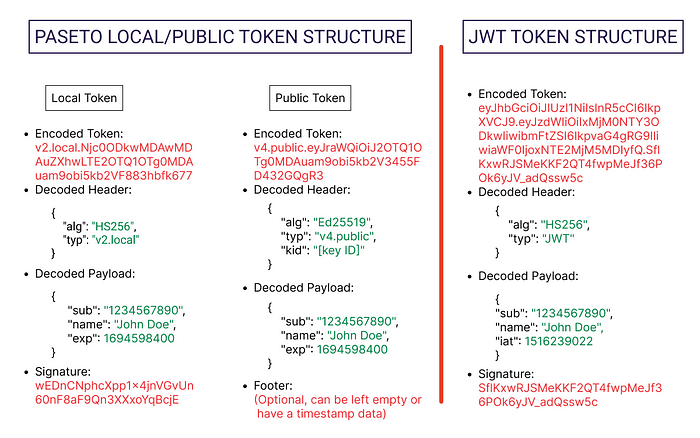
Paseto Structure
Unlike JWT’s single, generic structure, Paseto employs a versioned approach with two distinct token purposes:
- Local tokens: This is designed for stateful, server-side sessions where the tokens are securely stored on the server-side and associated with a user’s session.
- Public tokens: This is intended for stateless applications and use cases involving public-key cryptography. These tokens can be securely transmitted and verified without needing server-side storage.
Both local and public tokens share a similar structure, consisting of three parts:
- Header: This section identifies the Paseto version and purpose (local or public) along with the specific cryptographic algorithm used.
- Payload: Similar to JWT, the payload contains claims representing information about an entity (usually the user) and any additional data relevant to the application.
- Footer (optional): The footer can include additional authenticated data, providing extra security and context to the token.
How PASETO Works?
Paseto’s core strength lies in its focus on secure defaults and well-defined implementations.
It eliminates the risk of algorithm confusion, a known vulnerability in JWT, by explicitly specifying which cryptographic algorithms should be used for each version and purpose. This approach ensures that developers don’t inadvertently choose insecure options.
- Local tokens: Typically use symmetric-key cryptography, where the same secret key is used for both encryption and decryption. This makes them suitable for server-side session management, where the server maintains control over the key.
- Public tokens: Employ public-key cryptography, involving a public key for encryption and a private key for decryption. This enables secure communication and verification without sharing the secret key.
How to Implement JWT or Paseto in Your Project?
Here’s a basic guideline for implementing either JWT or Paseto in your project:
- Choose a Library: Select a library for your project. There are several options available for popular languages like Python, Node.js, Java, and Ruby.
- Generate a Secret Key: Create a strong and secure secret key to sign and verify tokens. Store it securely. For local tokens, generate a secure secret key. For public tokens, generate a public-private key pair.
- Implement Token Generation: Develop a mechanism to generate the token upon successful user authentication, including relevant claims in the payload.
- Implement Token Validation: Implement logic on the server-side to validate the token received in requests, verifying the signature and expiration time.
- Secure Token Storage: On the client-side, securely store the JWT (e.g., HttpOnly cookies with the Secure flag).
- Handle Token Expiration: Implement a strategy to handle expired tokens, such as refresh tokens or requiring re-authentication.
- Payload extraction and verification: This steps works only for Paseto, where the payload and verified the to ensure the authenticity and integrity of the information.
Key Differences Between Paseto vs JWT
Structure
AspectPasetoJWTApproachVersioned approach with specific purposes (local/public)Single, generic structureComponentsHeader, payload, optional footerHeader, payload, signatureFormatting RulesStricter formatting and implementation rulesMore flexible, allowing for various algorithms and claims
Security Features
AspectPasetoJWTAlgorithm ConfusionEliminated by specifying algorithms per version/purposePotential vulnerability if “none” algorithm is allowedKey ManagementPromotes better practices by designRequires careful implementation to avoid vulnerabilitiesRevocationEasier due to versioning and purpose-specific designStateless nature makes it challenging; requires additional mechanismsConfiguration DefaultsEnforces secure algorithms and configurationsAllows for potential misconfigurations and vulnerabilities if not implemented carefully
Use Case Scenarios
TokenPasetoJWTLocal TokensStateful server-side sessions (e.g., traditional web apps)Can be used for various use cases, including both stateful and stateless applicationsPublic TokensStateless authentication with public-key cryptographySuitable for various scenarios but requires careful consideration of security implications
token structures
An image showing the structural difference of Paseto and JWT
Choosing Between Paseto and JWT
Both Paseto and JWT offer distinct advantages and disadvantages, making the choice dependent on your specific needs and priorities.
Here are some factors that can influence your decision:
Security Needs
- Paseto: If your application demands robust security and protection against common vulnerabilities, then Paseto is probably the best fit for you. Because it is designed to mitigate issues like algorithm confusion and promote better key management practices, ensuring a higher level of security.
- JWT: While JWT can be secure when implemented correctly, it necessitates meticulous attention to detail and a thorough understanding of potential pitfalls. Developers must be vigilant in avoiding common misconfiguration and vulnerabilities.
Application Architecture
- Paseto: Paseto offers a clear distinction between local and public tokens, catering to different architectural requirements. Local tokens, designed for stateful server-side sessions, are ideal for traditional web applications with session management. Public tokens, geared towards stateless applications and public-key cryptography, align well with microservices and API-driven architectures.
- JWT: It’s flexible structure accommodates both stateful and stateless applications. However, this flexibility can also lead to ambiguity and potential misuse, if not handled carefully.
Developer Familiarity
- Paseto: While Paseto’s ecosystem is steadily growing, it might not yet match the breadth and depth of JWT’s support. Developers might need to invest additional effort in finding appropriate libraries and understanding Paseto’s specific implementations.
- JWT: Due to its earlier adoption and widespread usage, JWT benefits from a larger community and readily available libraries, frameworks, and documentation across various programming languages. This makes it easier for developers to find resources and implement JWT within their projects.
Ecosystem Support
- Paseto: It’s ecosystem is expanding, with libraries and tools becoming increasingly available for popular programming languages. However, it may not yet match the comprehensive support of JWT, particularly for less common languages or frameworks.
- JWT: JWT enjoys extensive support across numerous programming languages, frameworks, and libraries. This widespread adoption ensures readily available resources and simplifies integration with existing tools and infrastructure.
The Future of Web Tokens
The web tokens landscape is constantly evolving, driven by advancements in cryptography, changing security threats, and the ever-growing need for secure and efficient authentication mechanisms.
Here are some emerging ideas that may shape the future of web tokens:
Enhanced Security and Cryptography
- Quantum-resistant cryptography: With the looming possibility of quantum computers breaking existing cryptographic algorithms, the development and adoption of quantum-resistant algorithms will be crucial for future-proofing web tokens.
- Post-quantum cryptography: Research and standardization efforts are underway to develop and integrate post-quantum cryptography algorithms into token-based systems, ensuring long-term security and resilience against quantum threats.
Decentralized Identity and Self-Sovereign Identity (SSI)
- Verifiable credentials: With the rise of verifiable credentials, this allows individuals to control and manage their digital identities, which may influence how tokens are used for authentication and authorization.
- Decentralized Identifiers (DIDs): This enables decentralized and self-owned identifiers, and could be integrated with token-based systems to enhance privacy and user control over personal data.
Improved Usability and Standardization
- Simplified token management: Efforts to streamline token generation, revocation, and renewal processes will improve user experience and developer efficiency.
- Standardization of token formats and protocols: Further standardization of token formats and communication protocols will promote interoperability and simplify integration across different platforms and services.
Emerging Token Mechanisms
- Macaroons: This offer a more flexible and granular approach to authorization, allowing for delegation and attenuation of access rights.
- Token binding: This mechanisms can mitigate token theft and replay attacks, enhancing the security of token-based systems.
Influence on Paseto and JWT
Paseto’s focus on security and well-defined use cases positions it well for adoption in environments with high-security requirements and where standardization is valued.
Its versioned approach allows for adaptation and integration of future cryptographic advancements.
JWT’s flexibility and widespread adoption may lead to its continued use in various applications. However, its security shortcomings might necessitate additional safeguards and careful implementation practices to mitigate risks.
The future of web tokens will probably involve a combination of existing and emerging mechanisms, each catering to specific needs and security considerations.
References
JWT Resources:
Paseto Resources:
Further Reading:
- Understanding JWTs and Their Use in APIs
- Why Paseto is Better Than JWT for Token-Based Authentication
This content originally appeared on DEV Community and was authored by Manoj Gohel
Manoj Gohel | Sciencx (2024-06-21T05:33:01+00:00) JWT vs PASETO: New Era of Token-Based Authentication. Retrieved from https://www.scien.cx/2024/06/21/jwt-vs-paseto-new-era-of-token-based-authentication/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.