This content originally appeared on HackerNoon and was authored by Lior Barak
In the high-stakes world of data management, a single crack in the foundation can bring down an entire empire. The recent Snowflake hack has proven to be just such a catastrophic event, with its aftershocks toppling data fortresses across industries. The latest casualty? Telecommunications titan AT&T, whose massive data breach has sent shockwaves through the business world.
\ On July 12, 2024, AT&T revealed that data from "nearly all" of its wireless customers was compromised in a breach connected to the Snowflake hack. This disclosure, coming seven weeks after Snowflake's initial announcement of unauthorized access to certain customer accounts, has deepened the crisis and highlighted the interconnected vulnerabilities in our digital ecosystem.
\
:::info Read more about the Snowflake hack: Hackers steal “significant volume” of data from hundreds of Snowflake customers
Read more about the AT&T hack: AT&T’s massive data breach deepens crisis for Snowflake seven weeks after hack was disclosed
:::
\ This cascade of data breaches serves as a stark wake-up call: in today's interconnected digital landscape, your data security is only as strong as your weakest link - or in this case, your third-party providers. It's a bitter pill to swallow for the 165 companies affected by the Snowflake breach and an alarming reminder that even tech giants can fall prey to cybercriminals.
\ One thing becomes crystal clear, the days of carelessly tossing our data around like a cheap salad are over. It's time to start treating our data for what it truly is - the secret sauce of our digital age. And like any prized recipe, it needs to be guarded with the utmost care and precision.
The Risks of Lazy Data Management
For years, I've been the Jamie Oliver (Screaming about kids and veggies) of data architecture, shouting from the rooftops about the need for separate environments in data processing and storage. Yet, I've watched in horror as companies serve up their data to third-party services on a silver platter, choosing the drive-thru convenience of direct connections over the gourmet security of proper data management.

Organizations using third-party services to process or operate their data must create robust mechanisms to control data exposure. This isn't merely about security; it's about maximizing data value while minimizing risks and costs.
\ Imagine running a bustling restaurant. Your secret sauce - the data that gives you a competitive edge - is carefully guarded. You wouldn't hand over your recipe book to every vendor who walks through the door. Similarly, in the data world, careful control over information access is crucial.
\ I once had a heated discussion with an ads service account manager who couldn't understand why we refused to share our e-commerce site's full conversion data. Our stand was clear: user data is our secret sauce and should be kept as close as possible.
The Four Data Zones: A Balanced Approach
To turn this fast-food nightmare into a Michelin-star data strategy, I propose a four-course approach to data management:
\
- Appetizer: The Ingestion Zone - Where raw data is carefully selected and prepped.
- First Course: The Raw Data Zone - A secure pantry where only the head chef has access.
- Main Course: The Analysis Zone - Where data is expertly prepared for consumption.
- Dessert: The Decision-Making Zone - Where insights are plated and served to decision-makers.
\
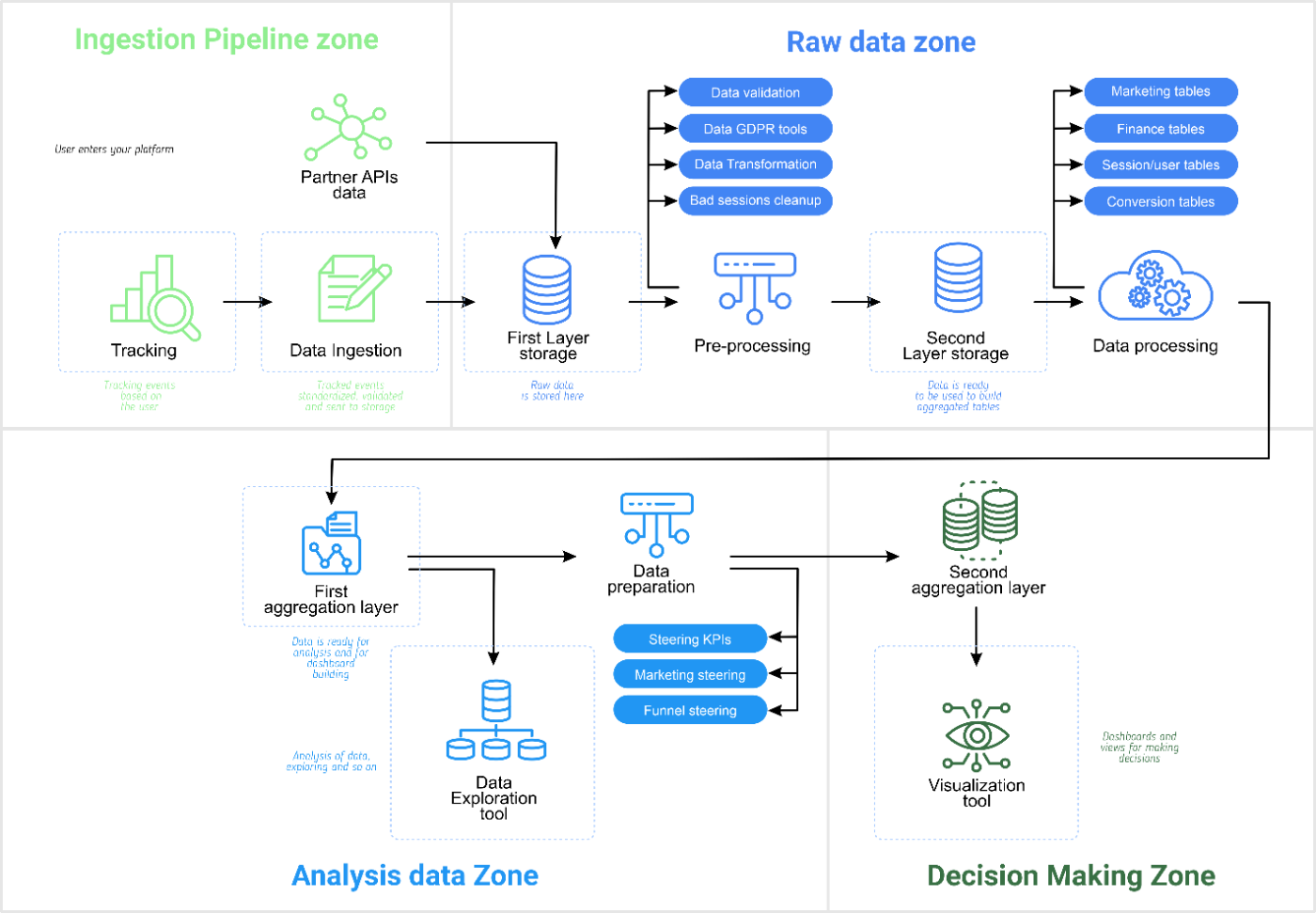
Implementing the Four Zones
Ingestion Zone
This is your most vulnerable area. While using third-party tracking solutions is common, build a container to obtain this data, map it, flag sensitive information, and prepare it for secure storage, try to set a more often pull of information from the tracking solution and remove it after validating all data has arrived safely into your owned container.
Raw Data Zone
Split this into two operations:
- Pre-processing: Clean or hash sensitive data, remove bad sessions, and combine data sources without human intervention.
- Data Products: Transform cleaned data into larger tables for analysis, still without human touch.
\ Recommendation: Implement strict access rules and data retention policies (45 days for pre-processing, 180 days for data products).
Analysis Zone
Make data available to those who know how to work with it. Ensure user-level data is hashed and secured. Implement logging for all data access and manipulation.
Decision-Making Zone
Upload aggregated, non-individual data to third-party visualization tools. Focus on persona-level or channel-level data to minimize risks.
\
\

Fortifying Your Data Fortress: Advanced Security Measures
Even the four-zone architecture needs additional reinforcement. Here are ten critical measures to strengthen your data fortress:
- Multi-Factor Authentication (MFA) Everywhere: The Snowflake breach exploited accounts without MFA. Make it mandatory across all zones, with no exceptions.
- Rigorous Credential Management: Rotate credentials regularly and monitor for compromises. Remember, some breached Snowflake credentials were years old.
- Network Access Controls: Implement network allow lists in your Raw Data and Analysis Zones. Only trusted locations should have access to your data pantry.
- Infostealer Malware Protection: Given the role of infostealer malware in recent breaches, beef up your defenses, especially on devices used for both work and personal purposes.
- Third-Party Risk Management: Don't let your data security chain be broken by its weakest link. Thoroughly vet, continuously monitor, and actively manage your third-party providers.
- Cross-Zone Incident Response Plan: Have a well-rehearsed plan ready. When a data breach occurs, every second counts.
- Data Minimization: In your Raw Data and Analysis Zones, adopt a 'less is more' approach. Only store what's necessary, for as long as it's necessary.
- Strong Encryption: Use robust encryption for data at rest in your Raw Data Zone and in transit between all zones. Think of it as your data's armor.
- Continuous Monitoring: Implement 24/7 monitoring and anomaly detection across all zones. It's like having a vigilant guard always on duty.
- Compliance Considerations: Ensure your data architecture meets relevant data protection regulations. It's not just about security; it's about legal protection too.
\ By incorporating these measures into our four-zone architecture, we create a data management system that's not just functional but fortress-like in its security. Remember, in the world of data, as in cooking, it's not just about having the right ingredients – it's about how you combine and protects them that makes the difference between a data disaster and a digital delicacy.
A Final Note from the Chef
I'm a data chef, not a legal sommelier. While I can advise you on how to prepare and serve your data, for the perfect wine pairing of legal compliance, please consult with a qualified legal advisor. They can guide you on the intricate bouquet of privacy laws and regulations that accompany our data cuisine.
\ By following these principles, you can transform your data from a potential food poisoning outbreak into your restaurant's signature dish. In the world of business, as in cooking, it's not about having the most exotic ingredients – it's about combining them with skill and care to create something truly remarkable.
The Perfect Data Dish: A Lasting Impression
As we clear the table on our data management feast, let's recap the key ingredients of our recipe for success:
\
- Implement the four-zone data architecture to organize your data kitchen.
- Fortify your data fortress with advanced security measures.
- Cultivate a culture where everyone understands the value of data security.
- Regularly audit and taste-test your data management practices.
- Don't forget the secret ingredient: adaptability. The data landscape is always changing, and so should your approach.
\ Remember, in the world of data, as in haute cuisine, excellence isn't achieved overnight. It's the result of careful planning, meticulous execution, and continuous refinement. By following these principles, you're not just avoiding a data disaster - you're creating a data management masterpiece that will keep your business thriving in the digital age.
\ So, chef, are you ready to turn your data into your company's signature dish? The kitchen is yours!
\ Now, let's get cooking with data!

\
This content originally appeared on HackerNoon and was authored by Lior Barak
Lior Barak | Sciencx (2024-07-15T15:38:50+00:00) The Snowflake Hack and Its Domino Effect. Retrieved from https://www.scien.cx/2024/07/15/the-snowflake-hack-and-its-domino-effect/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
