This content originally appeared on Level Up Coding - Medium and was authored by Hayk Simonyan
How Signed URLs and Cookies Protect Your Cloud Data
If you use services such as Amazon S3, Google Cloud Storage, Azure BLOB storage, or hosting images and videos on a CDN like on CloudFront, you need to be familiar with signed URLs and signed cookies.

The Problem: Unchanging URLs
Let’s say you upload a picture to a cloud storage service. You get back a URL — a web address that points directly to your image.
This URL always stays the same for this image. And that can be a problem in some applications.
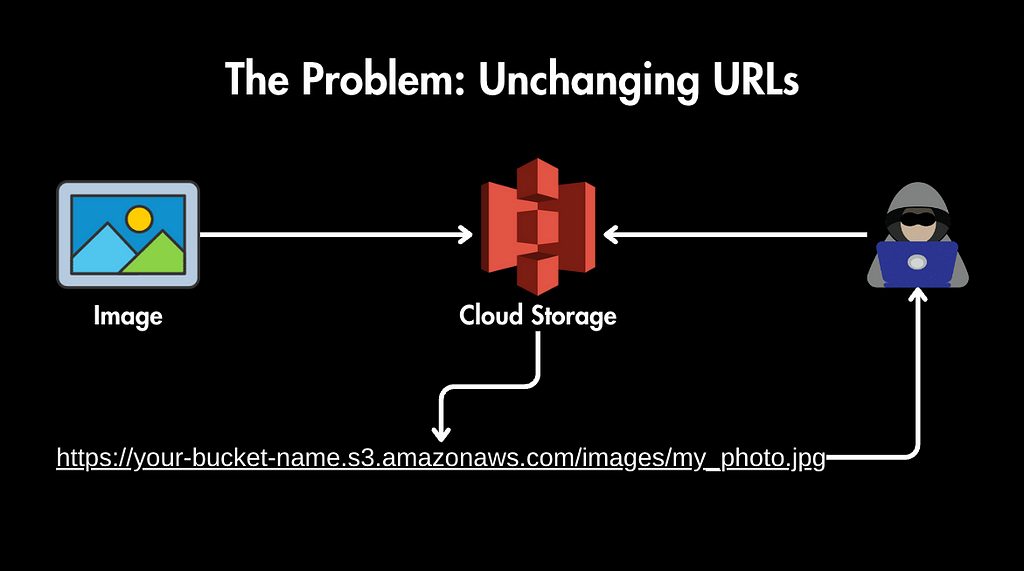
Anyone with that link could keep accessing the image, even if it’s not supposed to be there anymore.
This is where you can use signed URLs.
What are Signed URLs

A signed URL is a specially crafted URL that gives someone access to a specific object in your storage, but only for a limited time. Here’s an example of a signed URL:
https://your-bucket-name.s3.amazonaws.com/images/my__photo.jpg?
X-Amz-Algorithm=AWS4-HMAC-SHA256
&X-Amz-Credential=AKIAIOSFODNN7EXAMPLE%2F20240613...
&X-Amz-Date=20240613T121207Z
&X-Amz-Expires=3600
&X-Amz-SignedHeaders=host
&X-Amz-Signature=549b82e38a2e3c401e6f6650516d...
For example, Instagram uses signed URLs for images and videos. You can see that by inspecting one of the images on their website and looking at the image URL.
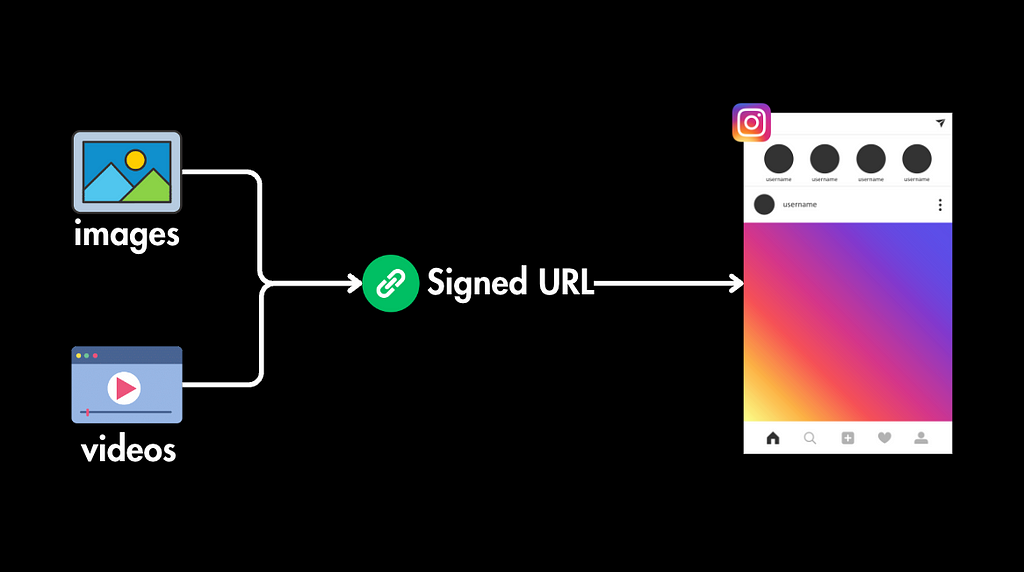
That means that the URL for a certain image will change depending on who requests it. It will also expire after some time.
This helps them prevent bots from scraping their images or another person from scraping Instagram and creating a database of their images using URLs because they will be constantly changing.
So, how does this magic happen?
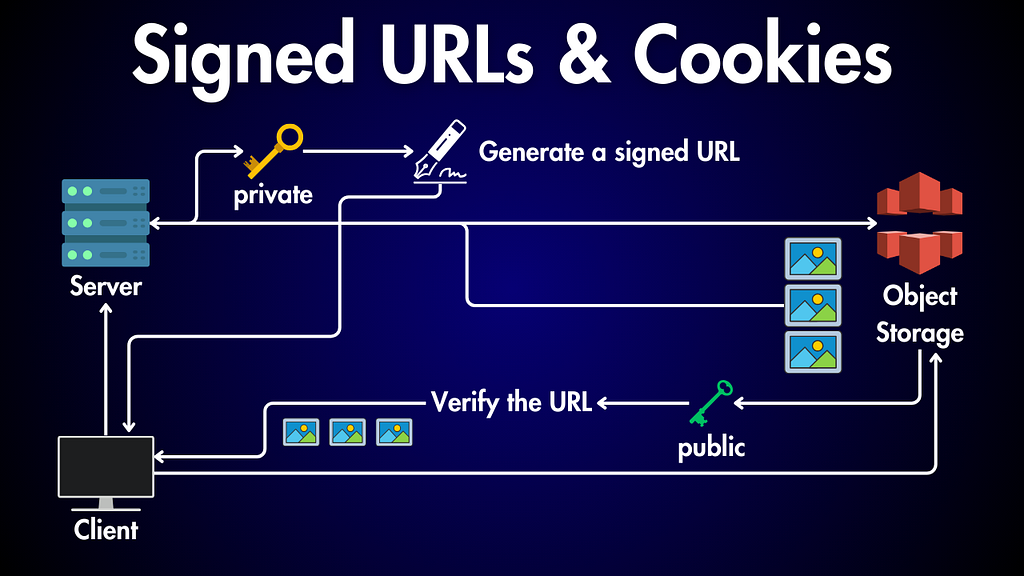
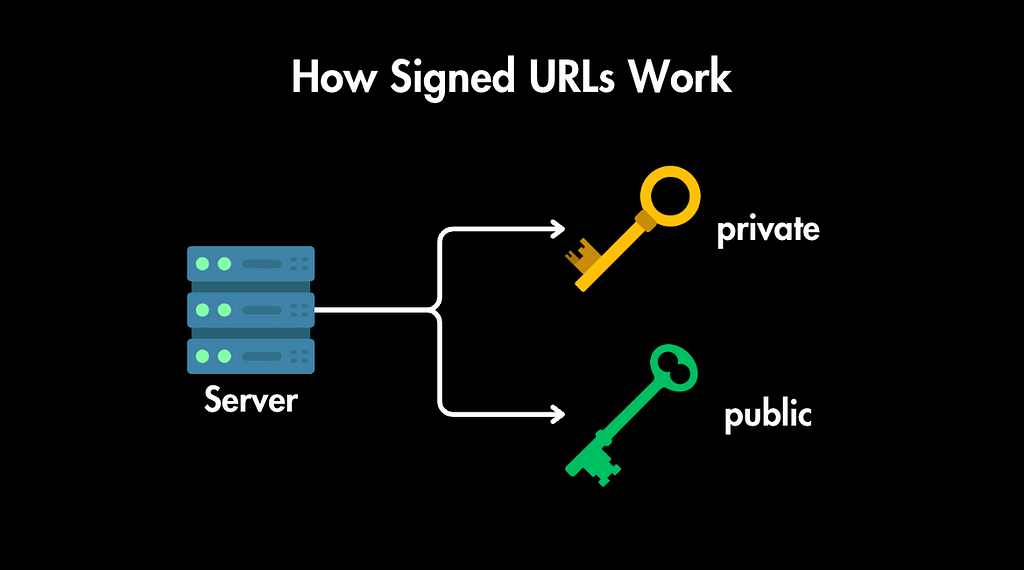
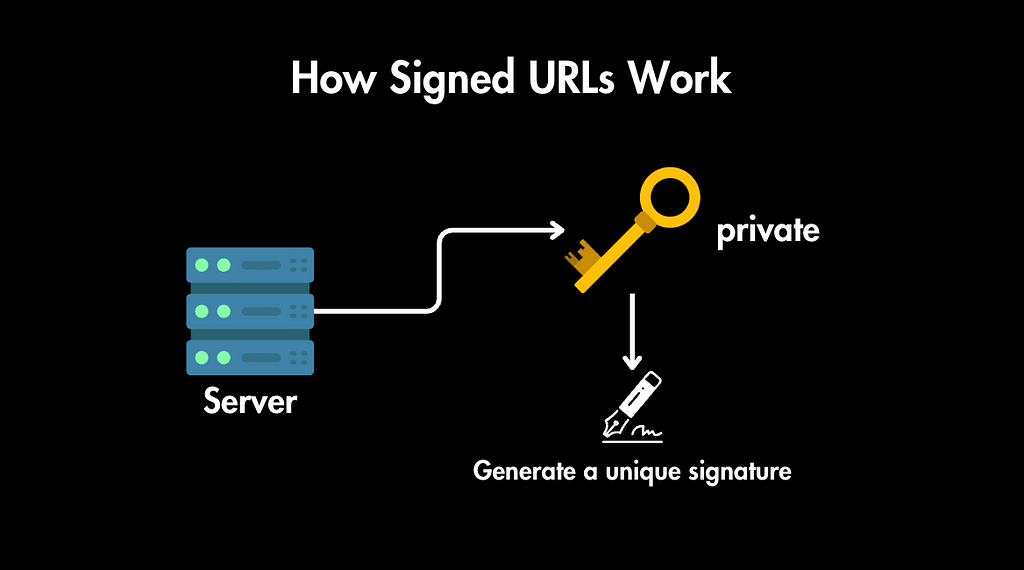
- Key Pairs: To create a signed URL, your server generates a pair of cryptographic keys: a private key that you keep secret on your server and a public key that you share with the object storage service.
- Signing: The server uses its private key to generate a unique signature based on the image identifier, expiration time, and any access restrictions. This signature is then appended to the image URL.
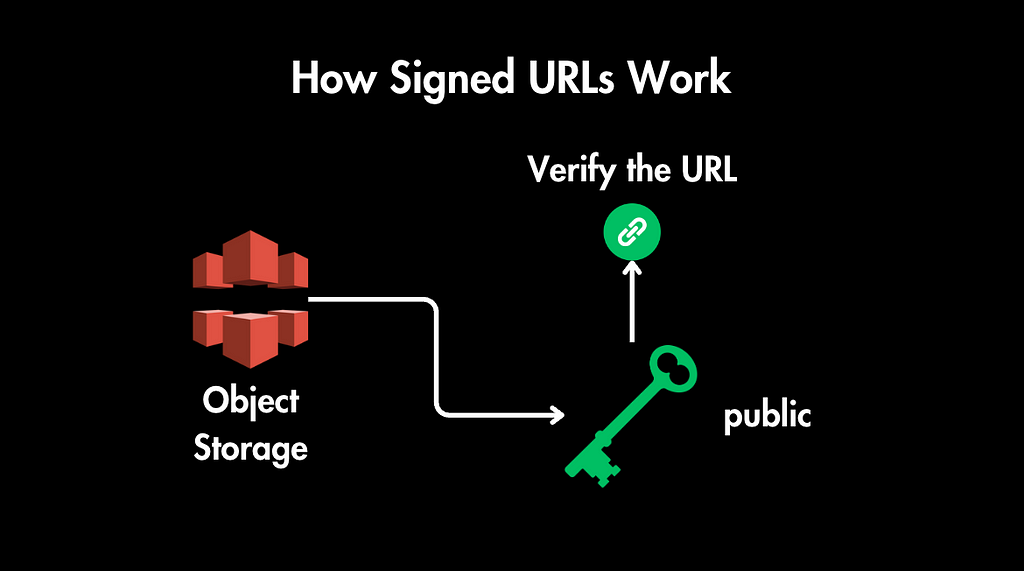
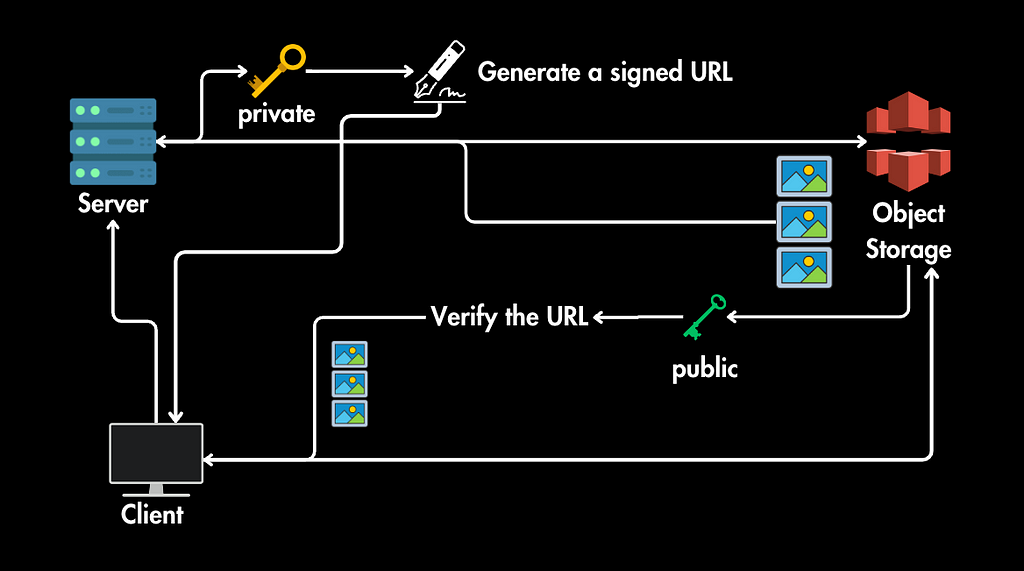
- Verification: When a client requests the signed URL, the object storage service uses the corresponding public key to verify the signature's authenticity. If the signature checks out and the conditions (expiration, permissions) are met, the request is granted.
How Signed URLs Work
Here’s a breakdown of how it works:
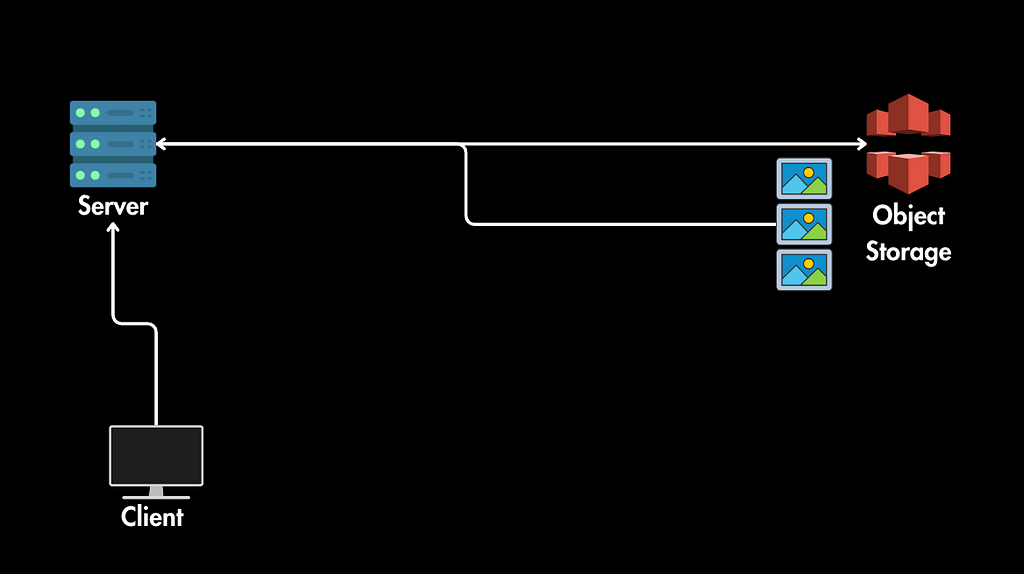
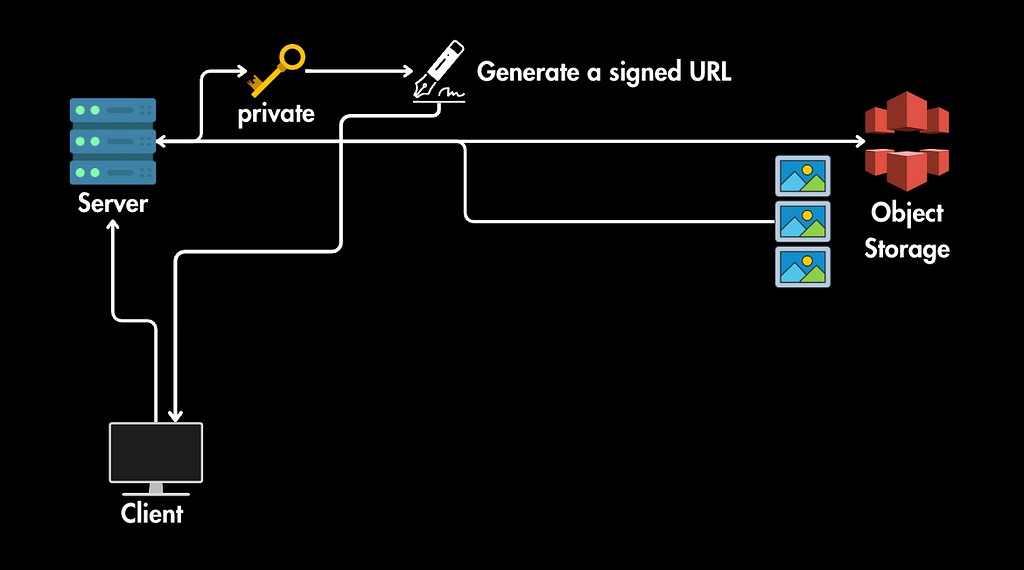
1. Initial Request to Server: The client first sends a request to the server (e.g., by clicking a link on a webpage). This request might be for a specific image or a page containing multiple images.

2. Server Generates Signed URLs:
- The server processes the request and identifies the images needed.
- For each image, the server generates a signed URL using its private key.
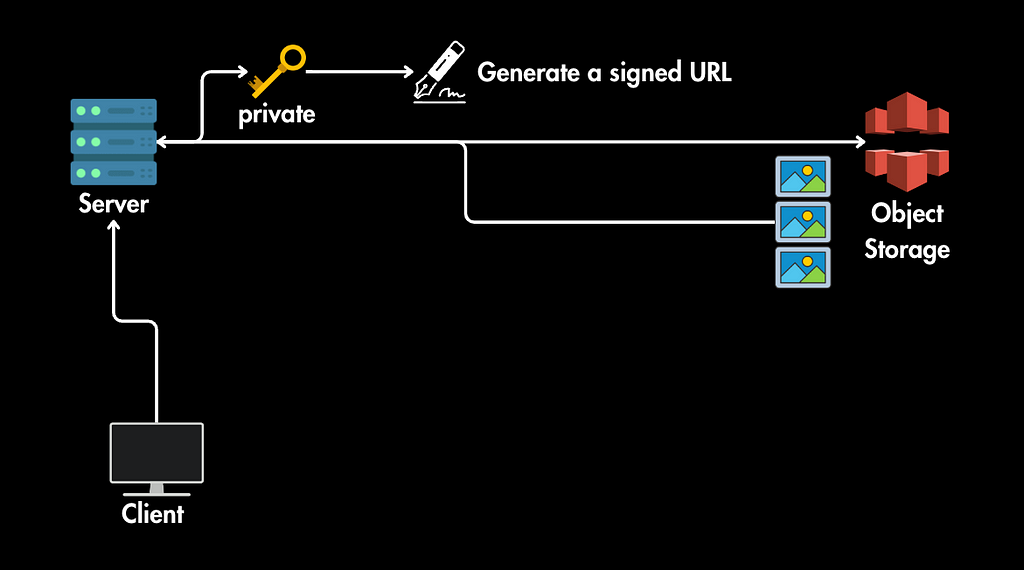
- The server sends these signed URLs back to the client.
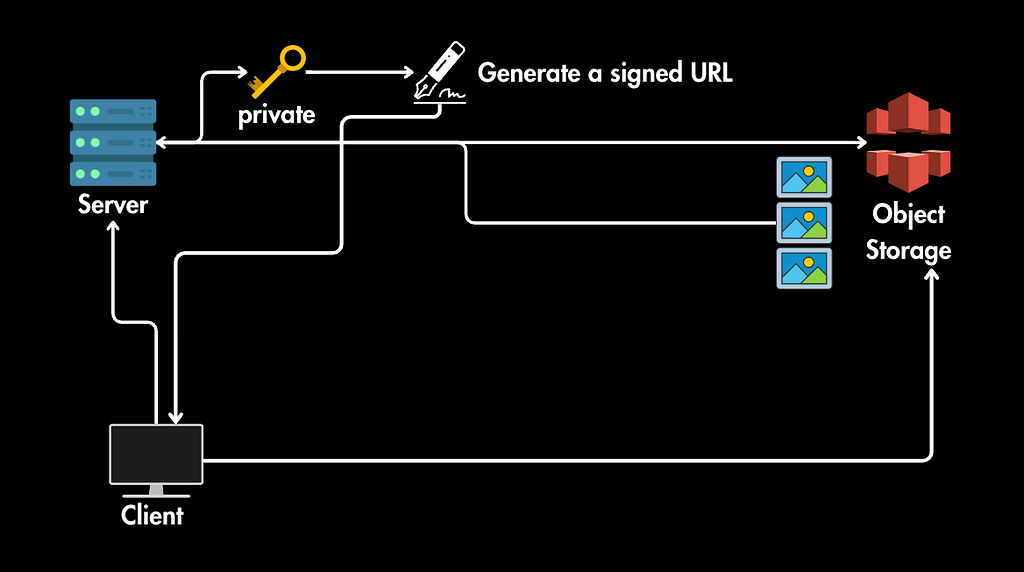
3. Client Requests Images from Object Storage:
- The client’s browser (not the server itself) uses each signed URL to make separate requests directly to the object storage service (e.g., Amazon S3).
- The object storage service uses the corresponding public key to verify the signature’s authenticity.
What are Signed Cookies

Signed cookies are similar to signed URLs, but instead of protecting just one object, they can protect a whole bunch of them — like an entire directory or a website. Here’s an example of a signed cookie:
Set-Cookie: CloudFront-Policy=eyJTdGF0ZW1lbnQiOl7IkRhdGVMZXNzVGhhb...;
Set-Cookie: CloudFront-Signature=YrL809G3oZ043432402394830298~jWHzL2JM...
Set-Cookie: CloudFront-Key-Pair-Id=K3ADVBZEXAMPLE
How Signed Cookies Work
They work in a similar way to signed URLs. However, instead of adding the signature to the URL, it’s included in a cookie that gets sent along with the HTTP request.
1. Cookie Generation: Your server generates the signature based on the resource requested, the access policy, and other parameters. This signature, along with the policy, is included in a cookie.
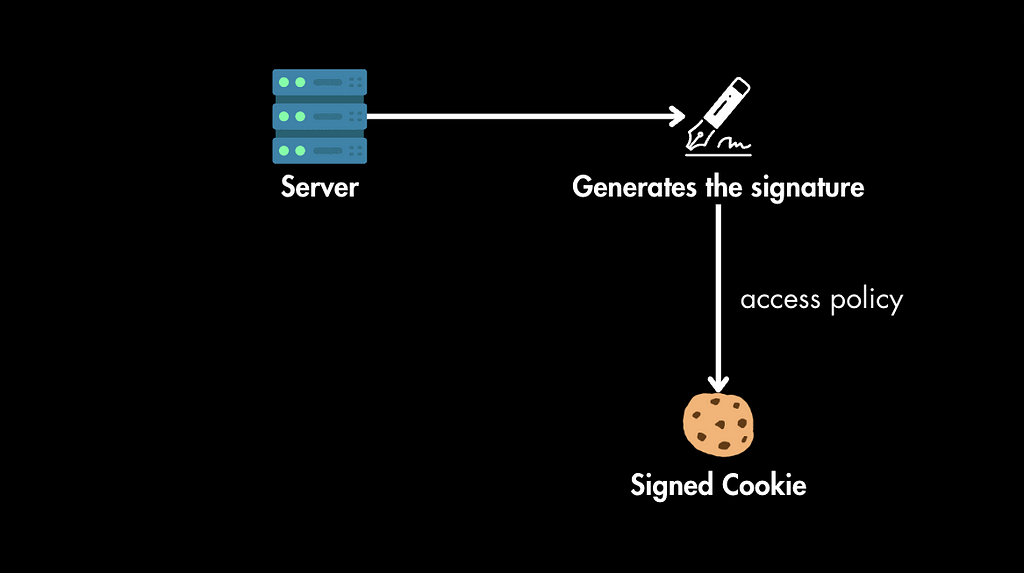
2. Cookie Storage: The cookie is sent to the user’s browser and stored there.
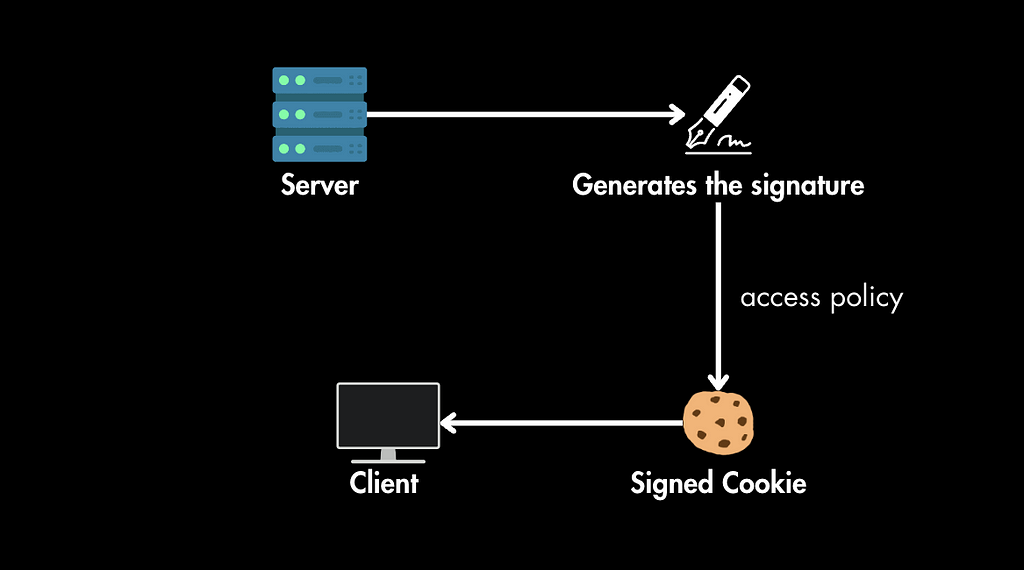
3. Request Verification: When the user requests a protected resource, the browser automatically sends the cookie along with the request. The server verifies the cookie’s signature and policy to determine whether to allow access or not.
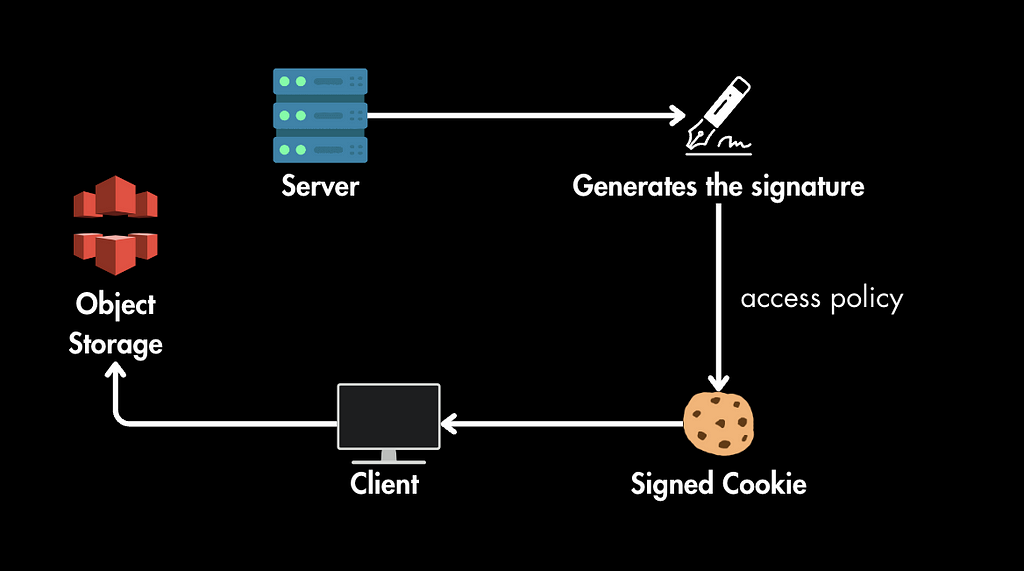
When to Choose One Over the Other?
- Signed URLs are great for individual files or when you want really tight control over who can access what.
- Signed Cookies are awesome for protecting a large number of files or offering temporary access to a specific area of your website (like a premium member section).
And that’s the lowdown on signed URLs and cookies! They might seem a bit complex initially, but they’re an absolute must-have for some scenarios to keep your object storage secure.
How Signed URLs & Cookies Protect Your Cloud Data was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Hayk Simonyan
Hayk Simonyan | Sciencx (2024-07-16T16:31:54+00:00) How Signed URLs & Cookies Protect Your Cloud Data. Retrieved from https://www.scien.cx/2024/07/16/how-signed-urls-cookies-protect-your-cloud-data/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
