This content originally appeared on HackerNoon and was authored by Ishan Pandey
My Cloud Security Nightmare (and What I Learned)
Hey everyone, Ishan here. So, funny story - last week I had a minor heart attack. No, not the medical kind (thank god), but the "oh crap, I think we just got hacked" kind. Yeah, not fun.
\ It all started when I noticed some weird activity on our cloud servers. At first, I thought it was just a glitch. You know how it is with tech - sometimes things just go wonky for no reason. But then I saw some files I definitely didn't recognize, and that's when the panic set in.
\ Long story short, we hadn't been hacked (phew!), but it was a close call. Turns out one of our interns had accidentally left a test server wide open. Rookie mistake, right? But here's the thing - it was partly my fault too. I'd been so focused on building our product that I'd kinda neglected our security setup. Classic startup mistake.
\ Anyway, this whole ordeal got me thinking about cloud security. I mean, we're a small startup, not some big tech giant. Do we really need to worry about this stuff? Turns out, hell yeah we do!
\ So I did what any self-respecting techie would do - I went down a Google rabbit hole. And let me tell you, there's a lot of fancy jargon out there. Zero Trust this, CASB that. It's enough to make your head spin.
\ But here's what I figured out:
\
Trust no one (in tech terms): This "Zero Trust" thing isn't about being paranoid. It's just about double-checking everything. Like, imagine if every time someone wanted to get into your house, they had to show ID, use a key, AND know a secret handshake. That's kinda what it's like.
Every device is a potential troublemaker: You know how one bad apple spoils the bunch? Same with devices. One hacked laptop can mess up your whole system. So you gotta protect everything - phones, laptops, even that old tablet you use for testing.
The cloud isn't magic: Just because your stuff is "in the cloud" doesn't mean it's automatically safe. It's more like renting a super secure storage unit. The building's safe, but you still gotta lock your own unit and not leave the key under the mat.
People are the weakest link (sorry, team): All the fancy tech in the world won't help if someone clicks on a phishing email. We gotta train our people. And not with those boring slideshows - maybe like a "spot the fake email" game or something.
It's always changing: The security stuff that worked yesterday might not cut it tomorrow. It's like a never-ending game of whack-a-mole with hackers.
\
Look, I'm just a guy trying to keep his startup alive and not end up as another "small company gets hacked" headline. But after my little scare, I realized we can't afford to ignore this stuff. So yeah, we're making changes. Implementing some of that Zero Trust stuff, beefing up our training, the whole nine yards. Is it a pain sometimes? Sure. But you know what's a bigger pain? Explaining to your customers why their data is now on some shady forum.
\ Organizations are moving more and more of their operations to the cloud. This change has resulted in unprecedented efficiency, scalability, and flexibility. But this also presents fresh security issues and that conventional network security solutions might not be able to sufficiently handle. Let me introduce you to cloud network security, which is essential to protecting your company's digital assets in the cloud era.
\ The transition to cloud-based infrastructure and remote work has dramatically expanded the attack surface for cybercriminals. Traditional security models, designed for on-premises setups, are no longer sufficient in this new landscape. Imagine your startup as a fortress - in the past, you could build high walls and control who enters through the gates. Now, in the cloud era, your fortress is spread across multiple locations, with team members accessing sensitive information from coffee shops, home offices, and co-working spaces around the world. Each of these access points represents a potential vulnerability.
\
\
\ \ \
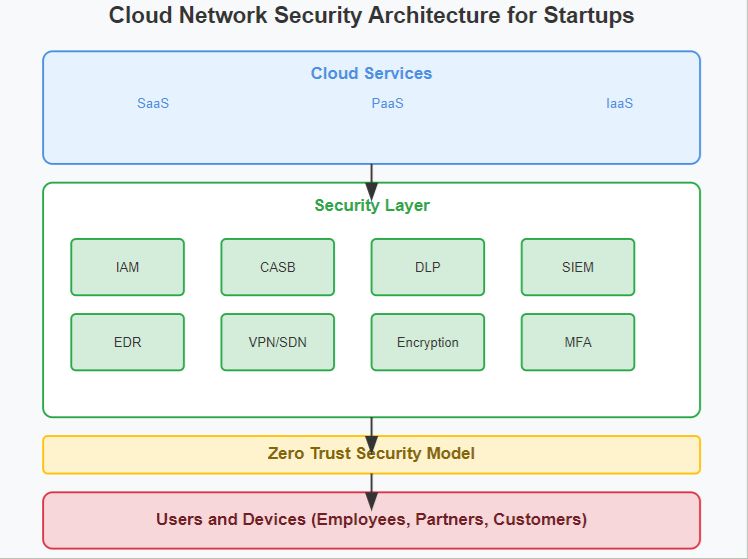
So how do you secure this distributed fortress? The answer lies in adopting a comprehensive cloud network security strategy that combines cutting-edge technology, smart policies, and a security-first culture.
\ At the heart of this strategy is the concept of Zero Trust. This isn't just another tech buzzword - it's a fundamental shift in how we approach security. In a Zero Trust model, no user or device is trusted by default, even if they're connected to a managed corporate network. This approach is particularly well-suited for cloud-native, remote-first startups where the traditional network perimeter is essentially non-existent.
\ Implementing Zero Trust starts with robust identity and access management (IAM). Tools like Okta or Azure AD can help you set up strong authentication mechanisms, including multi-factor authentication, without breaking the bank. The goal is to continuously verify every access request, regardless of where it originates.
\ But Zero Trust goes beyond just authentication. It also involves implementing least privilege access controls - ensuring that users only have access to the resources they absolutely need for their roles. This minimizes the potential damage if an account is compromised. Additionally, consider using micro-segmentation to isolate different parts of your network, containing potential breaches.
\ Secure remote access is another critical piece of the puzzle. Virtual Private Networks (VPNs) and remote desktop protocols are the lifelines of remote work, but they need to be properly secured to prevent them from becoming easy entry points for attackers. These tools can provide secure remote access without the complexity of traditional VPNs - a boon for startups looking to move fast without compromising on security.
\ In a remote work environment, every device is a potential entry point for threats. This makes robust endpoint security crucial, especially for startups handling sensitive data. A single compromised laptop or smartphone can lead to a full-scale data breach. To mitigate this risk, consider deploying Endpoint Detection and Response (EDR) solutions. These tools use advanced techniques, often powered by AI, to detect and respond to threats in real-time. For startups, next-gen antivirus solutions like CrowdStrike or SentinelOne can provide enterprise-grade protection without the need for a large IT security team.
\ As your startup increasingly relies on cloud services, it's essential to leverage cloud-native security measures. Many startups overlook this crucial aspect, assuming that their cloud provider takes care of all security concerns. While cloud providers do offer robust security features, the shared responsibility model means that you're still responsible for securing your data and applications.
\ Start by exploring the native security features offered by your cloud provider. Tools like AWS Security Hub or Google Cloud Security Command Center can provide a solid foundation for your cloud security efforts. As you grow, consider implementing Cloud Access Security Brokers (CASBs) to monitor and secure cloud app usage, and Data Loss Prevention (DLP) tools to prevent sensitive data from leaving your organization.
\ While all these technological solutions are crucial, it's important to remember that human error remains one of the biggest security risks. This makes comprehensive security training an essential part of your strategy. A security-aware workforce can be your first line of defense against many common threats, particularly social engineering attacks like phishing.
\ Make security training engaging and relevant. Use real-world examples and scenarios that your team might encounter. Consider using gamification to make the training more interactive and memorable. Tools like KnowBe4 offer engaging training modules that can help build a security-first culture from the ground up.
\ As you build and scale your startup, it's crucial to stay ahead of emerging security trends. Artificial Intelligence and Machine Learning are increasingly being integrated into security tools, enabling faster threat detection and response. The Secure Access Service Edge (SASE) model, which combines network security functions with WAN capabilities delivered as a cloud service, is gaining traction and could simplify security architecture for distributed teams.
\ Looking further ahead, the advent of quantum computing poses both opportunities and challenges for cybersecurity. While still in its early stages, quantum computing has the potential to break many of the encryption methods we rely on today. Forward-thinking startups should start considering quantum-safe cryptography and building crypto-agility into their systems to easily swap out encryption methods when needed.
\ In the fast-paced world of startups, it's easy to deprioritize security in the rush to innovate and grow. But in today's cloud-centric, remote-first business landscape, robust security isn't just about protection - it's a competitive advantage. It builds trust with customers, partners, and investors. It enables you to move fast and scale with confidence.
\ Remember, cloud network security is not a one-time setup but an ongoing process that requires continuous attention and adaptation. Start by implementing the fundamentals - Zero Trust architecture, secure remote access, strong endpoint security, and comprehensive employee training. Leverage cloud-native security tools and stay informed about emerging threats and technologies.
\ By building a strong security foundation from the start, you're not just protecting your startup from threats - you're setting it up for long-term success in the digital frontier. In the end, the most successful startups will be those that can innovate rapidly while keeping their digital assets secure. With the right approach to cloud network security, your startup can be among them.
\ Don’t forget to like and share the story!
\
:::tip Vested Interest Disclosure: This author is an independent contributor publishing via our business blogging program. HackerNoon has reviewed the report for quality, but the claims herein belong to the author. #DYOR.
:::
\
This content originally appeared on HackerNoon and was authored by Ishan Pandey
Ishan Pandey | Sciencx (2024-07-17T14:47:26+00:00) How Startups Can Bolster Defenses as Cyber Threats Loom in Cloud Era. Retrieved from https://www.scien.cx/2024/07/17/how-startups-can-bolster-defenses-as-cyber-threats-loom-in-cloud-era/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
