This content originally appeared on HackerNoon and was authored by Drosera Network
\ In this article I'm going to touch on a crucial new innovation that formed from months of research, experimentation, and orb pondering. The concept is a completely new form of security infrastructure for protocols that we are aptly naming - Traps.
\ After developing this concept internally and discussing it with groups from all over the ecosystem, we felt it was about time to walk through it in depth. It's one of those unique ideas that you don't see very often in this space and makes for a great conversation piece. While discussing Traps with others, we noticed that there was always a “light-bulb” moment where they understood the gravity of what we were building.
\ Seeing that spark of excitement followed up with a few ideas of their own reminded me of the early days in crypto where we were all learning about AMMs, FlashLoans, MEV, and ZK Proofs. Traps are a unique intersection of many of these crazy concepts in crypto, so depending on your background it can be a little complex but our goal is to guide you from Drosera novice to certified Trapper.
\

Background
Some context on how Drosera came about and where the idea of Traps came from. It would be pretty cool if it came to us in a dream or a fortune cookie but the reality is it came from the challenges of developing and maintaining internal monitoring systems.
Challenges
- No standardized approach
- No open-source framework
- Time consuming
\ The team was already very familiar with creating monitoring systems that detect specific events, transactions, and state changes in blockchains. We had to go through the process of building custom monitoring systems that required multiple services and unique implementation details. We wondered how possible it would be to decentralize these monitoring systems using smart contracts. Creating a base security layer was exactly what we wanted to build.
Philosophy of a Trap
The name Drosera comes from a genera of carnivorous plants and we liked the idea that a little liquidity could be used to help protocols catch bugs. It made us think about how protocols can be symbiotic and how catching a bug quickly should be incentivized. Most people are familiar with the toothed snap traps of the Venus Flytrap, this is what led us to the name “Traps” for our new security primitive.
\
\ Attributes of decentralized EVM security:
\
- A system where anyone, anywhere, can become a participant in the security landscape - regardless of skill.
- No hardware, no centralization, just an open network for security driven by application specific terms.
- EVM native security infrastructure built with smart contract code
- An open-source framework that fosters collaboration between solidity developers and security professionals.
Understanding a Trap
A Trap is a standard for security automation on the Ethereum blockchain. It's a smart contract that allows for complex time series analysis of any EVM state data. Anyone can create a trap by defining data to collect and the conditions that trigger an emergency response. The key takeaway here is that Traps are just developed in solidity, which allows developers to create security infra using the same tools they already use.
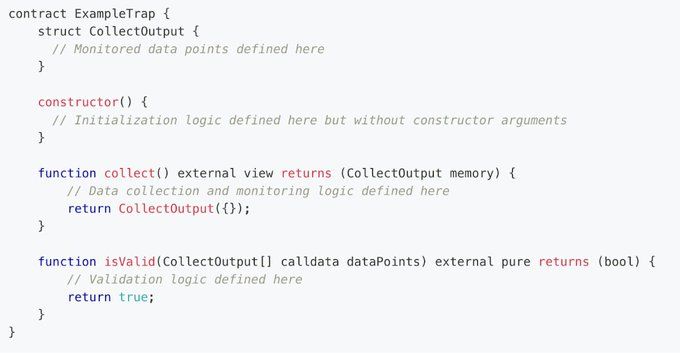
\ Traps are fully customizable due to the programmatic nature of smart contract code. This means that Trap development is as simple as adhering to a standard interface and writing a bit of solidity. Below is an example of the Trap interface.
\
\ \ The core components of a Trap are the collect function and isValid function.
\
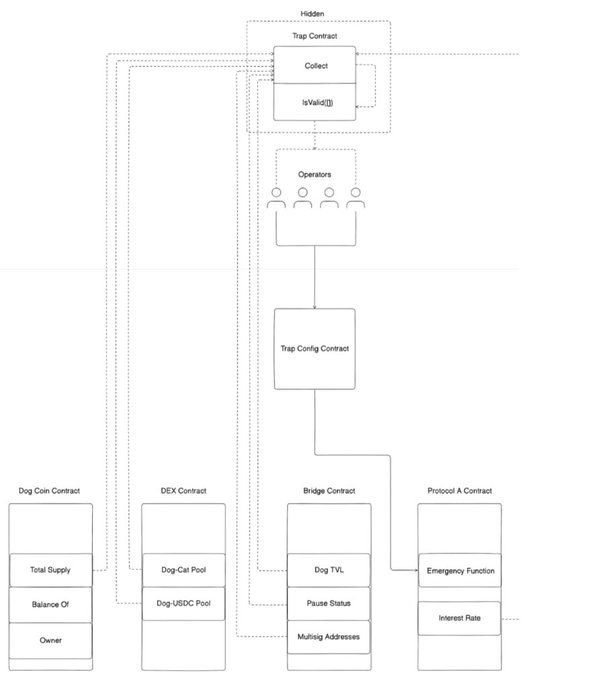
Collect allows a developer to fetch any state data that exists in the EVM. If a protocol developer wants to grab data from multiple DEXs, oracles, bridges, interop layers, lending protocols or anything then they can.
\
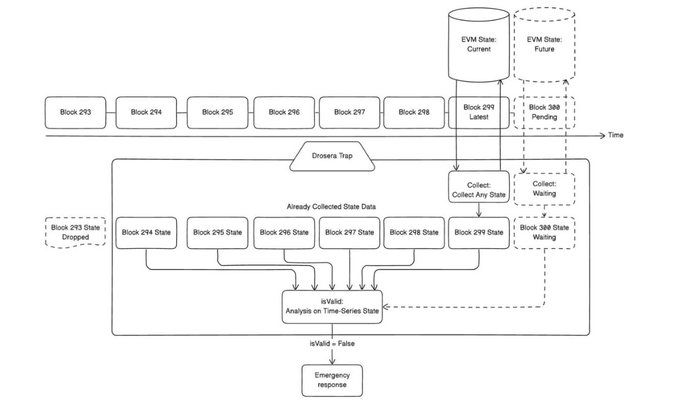
isValid allows a developer to do analysis on an array of the latest collected data. This array of data is a time-series list of the previous collect function calls.
\ Being able to perform this type of historical data analysis is unheard of in smart contracts, but Drosera has a unique approach that makes this all possible. In order to describe this in detail, we will probably need to have a separate article on the Drosera Node. It simply leverages the EVM as a data availability layer and ZK for objective historical analysis, like proof-of-execution between the collect function and the isValid function.
\
\
\
Incident Response
“Ok, so the trap can detect things but how is this useful for protocols?” - You, maybe.
\ Detecting that an incident has occurred is a prerequisite for security. The saying, knowing is half the battle, is certainly true but what matters most is the actions that take place in response to an incident. There are plenty of analogies to be drawn around emergency systems detecting something and an action plan taking place.
\
- If a fire alarm goes off in a building, then everyone evacuates.
- If a sprinkler system detects heat, then make it rain.
- If a car detects massive impact, then deploy airbags.
\
\ The current emergency systems in crypto follow a similar recipe but are horribly inefficient as a first responder action plan. If an exploit of our protocol is being discussed on X then try to wake everyone up to get in a war room. This situation is what Drosera is trying to improve, by allowing protocol developers to specify the incident conditions for automatic response. Drosera Node Operators run a protocol’s Trap and when conditions arise, the network works together to execute a predefined incident response with at least ⅔ consensus.
\
\ \
“Who defines the incident response and how?”
The creator of the Trap just needs to specify the path to the emergency button and the name of the emergency button. This is an address of any smart contract and any function on that smart contract. A response action could be swapping assets, pausing functionality, circuit breaking, performing disputes, liquidations, updating protocol configurations, or anything that a protocol developer can dream up. This is the power of fully leveraging smart contract code.
\ As for how the incident response gets triggered, this is done when the isValid function returns false. Indicating that the validity of the trap conditions have been broken and an action must take place. The Drosera network is constantly attesting to the results calculated from performing the isValid execution on their machine.
Benefits of EVM-Native Security
Now that we have covered Traps at a high level, it's important to understand the benefits of solidity security infrastructure:
\
Composability
It shouldn't be a surprise that one of the most powerful concepts in Ethereum is smart contracts. The ability for contracts to be built on top of contracts with any custom implementation is why crypto stands as a multi-billion dollar hub for innovation and technological advancement. Traps are smart contracts, which means they can be composed in any shape that a protocol developer sees fit without needing to compromise. When new contracts are deployed to the EVM, their data and functionality is automatically made available for Traps to leverage. This leaves the door open for creativity, experimentation, and network effects.
Extensibility
The concept of a Trap is actually quite simple. Our current implementation of its interface is pretty straightforward as far as smart contract definitions go. This means that there is plenty of room for new unique functionality that can be developed for smart contract security infrastructure. Drosera’s proof-of-execution primitives will allow us to innovate on new permutations as this new research area begins to gain traction.
Community
This aspect of Traps is actually huge. By creating an open framework for developers to come together through shared knowledge of smart contract code and the EVM, we are enabling a new community to form. We believe that this alone has been a huge blocker for security related projects to take form. Developers are curious and want to experiment with their tools. Frontends can be nice but developer communities do not form around how great a toggle button is, they form around tools that give them the ability to develop and talk with fellow developers.
\
Testability
While the concept of testing may seem a bit boring, it's actually an incredible pain when integrating with a monitoring system. To be completely honest, there really isn't any good way to test your security infrastructure against your protocol unless you are building monitoring in-house. I’ve built these frankenstein integration tests that connect in-house monitoring to a protocol and it's never pretty. Insanely time consuming and detracts from the development of the actual product. Fortunately with Traps, a developer can test their security infrastructure in the same dev environment as their protocol with Foundry. This allows for developers to verify their security infra is set up properly and they don't even need to leave their repo.
How Traps Fit Into Drosera
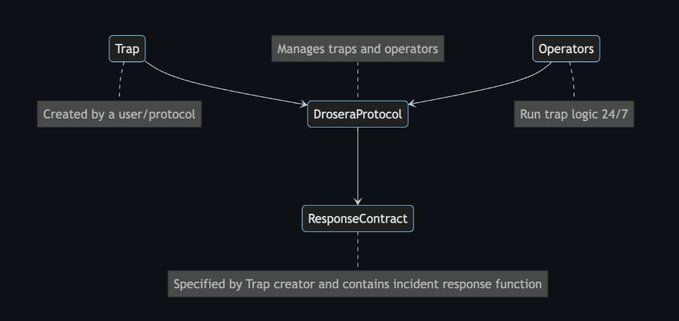
\ The drosera protocol at a high level:
\
A Trap is security infrastructure as solidity code.
Drosera is the protocol you deploy your security infrastructure to
Operators run the security infrastructure on Drosera
\
Traps run on Drosera, Operators run Traps, this means Drosera brings operators together with security for those asking for it.
\
\ In conclusion, Traps are dope, i mean it’s a completely new way to do application security and acts as a fundamental base layer of security for the ecosystem. We are excited to give additional insights on this new vertical and are planning on creating follow-on articles to discuss other critical components of the Drosera protocol.
\
Become a Trapper
We’re looking for Solidity Developers for a private testnet coming this month. We’re offering significant grants to those selected. Currently, we have a Hackaton running with a top prize of $2500 but the grants available would be even more substantial.
 What's in it for you?
What's in it for you?
- Significant rewards through grants.
- Exclusive access to work closely with our core team.
- Influence the development and direction of the Drosera protocol.
 Why join us?
Why join us?
- Exclusive Opportunity: Only 20 top-tier Solidity developers will be selected.
- Significant Rewards: Receive substantial grants for your contributions.
- Work with Industry Giants: Our operator program was already oversubscribed and protocols such as Swell, Yieldnest, and EtherFi have each pledged $300M in ETH delegations to Drosera.
- Direct Access to the Team: Collaborate closely with Drosera experts.
- Cutting-edge Technology: Work with "Traps" to build robust security infrastructure using Solidity code**.**
Ongoing Events:
The DoraHacks Hackathon is live now! Check out the exciting bounties available here.
 Ready to dive in?
Ready to dive in?
- Sign up on our Discord.
- Select the Trapper role.
- Say hello and introduce yourself!
\
This content originally appeared on HackerNoon and was authored by Drosera Network
Drosera Network | Sciencx (2024-07-17T15:55:30+00:00) WTF IS A TRAP?. Retrieved from https://www.scien.cx/2024/07/17/wtf-is-a-trap/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.