This content originally appeared on HackerNoon and was authored by Virtual Machine Tech
:::info Authors:
(1) Diwen Xue, University of Michigan;
(2) Reethika Ramesh, University of Michigan;
(3) Arham Jain, University of Michigan;
(4) Arham Jain, Merit Network, Inc.;
(5) J. Alex Halderman, University of Michigan;
(6) Jedidiah R. Crandall, Arizona State University/Breakpointing Bad;
(7) Roya Ensaf, University of Michigan.
:::
Table of Links
3 Challenges in Real-world VPN Detection
4 Adversary Model and Deployment
5 Ethics, Privacy, and Responsible Disclosure
6 Identifying Fingerprintable Features and 6.1 Opcode-based Fingerprinting
6.3 Active Server Fingerprinting
6.4 Constructing Filters and Probers
7 Fine-tuning for Deployment and 7.1 ACK Fingerprint Thresholds
7.2 Choice of Observation Window N
7.4 Server Churn for Asynchronous Probing
7.5 Probe UDP and Obfuscated OpenVPN Servers
9 Evaluation & Findings and 9.1 Results for control VPN flows
12 Acknowledgement and References
A Appendix
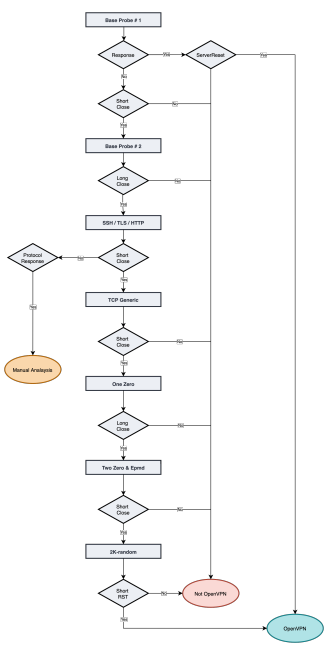
\
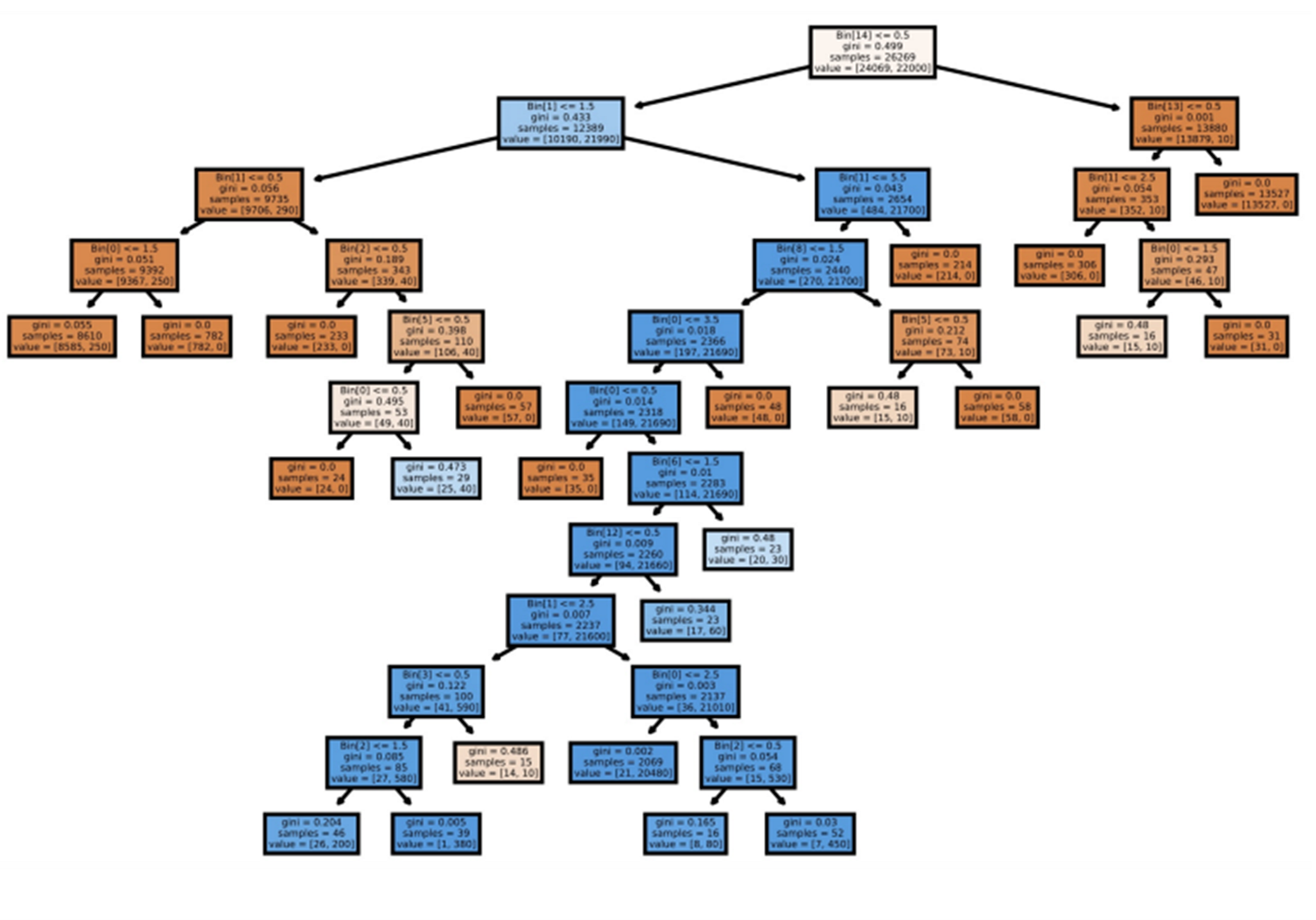
\

\
![Table 5: Evaluation results on Merit, breakdown by configuration. Highlighted rows are “obfuscated” configurations. Variants marked with stars mean that the VPN provider does not disclose which obfuscation technique is used and we can only infer the variant type based on packet captures. Note Hide.me claims the tls-crypt option alone is enough to “obfuscate entire traffic” [18]. However, this option only encrypts control channel payloads but not the OpenVPN packer headers.](https://cdn.hackernoon.com/images/fWZa4tUiBGemnqQfBGgCPf9594N2-11b3v26.png)
\
:::info This paper is available on arxiv under CC BY 4.0 DEED license.
:::
\
This content originally appeared on HackerNoon and was authored by Virtual Machine Tech
Virtual Machine Tech | Sciencx (2025-01-14T06:54:03+00:00) OpenVPN is Open to VPN Fingerprinting: Appendix. Retrieved from https://www.scien.cx/2025/01/14/openvpn-is-open-to-vpn-fingerprinting-appendix/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
