This content originally appeared on DEV Community and was authored by Swapnil Pawar
Amazon EC2 Systems Manager (SSM) lets you configure, manage and automate your AWS and on-premises resources at scale. You can perform safe and secure operations without SSH access or bastion hosts using Systems Manager Run Command, mitigate configuration drift using Systems Manager State Manager, and create an access-controlled environment with full auditing.
With SSM Documents, you can author your configurations as code and enable centralized management across accounts, enforcing best practices. Systems Manager provides a number of public documents for common management scenarios, or you can create your own document for deployment.
What Is Configuration as Code?
Configuration as code is the practice of managing configuration files in a repository. Config files establish the parameters and settings for applications, operating systems, etc. By managing your config files alongside your code, you can help streamline your release pipeline.
Benefits of Using Configuration as Code?
Scalability
Maintaining configuration changes as code allows to edit, update and create from the central location using a consistent deployment strategy.
Standardization
When you write configuration as code, you can implement other operations like testing, scanning, and linting. Having config files reviewed and tested before they are committed ensures that changes follow your team’s standards. If you have a complex microservices architecture, this can keep your configurations stable and consistent.
Traceability
By storing configuration as code in the repository, we get the benefit of tracking changes in code and config files. If a bug does slip in, you have the ability to trace the source of the problem. You can diff the versioned config files to see what went wrong and fix it quickly.
Configuration As Code acts as a Single Source of Truth for your build pipeline.
Other things you can do :
Execute various types of scripts written in Python, Ruby, or PowerShell. You can also run configurations such as Ansible playbooks. You can pretty much-run anything on your instances as long as the software (e.g., Python 3.8 or Ansible) is installed on your instance and recognized by Shell on Linux and PowerShell on Windows.
Download scripts stored in private or public GitHub repositories, or on Amazon S3 onto your instances for execution.
Run multiple files by downloading a complete GitHub directory or an S3 bucket.
Use Case:
Find the AWS-RunRemoteScript document for execution
On the AWS SSM console, on the navigation pane at the left, under Node Management Services, choose Run Command. Choose Run a Command, and then select the AWS-RunRemoteScript document and the instances you want to execute this document on (whether a list of instances or tag-queries).
Reference the python playbook located on GitHub
Enter the parameters for the AWS-RunRemoteScript Document to reference the Ansible playbook.
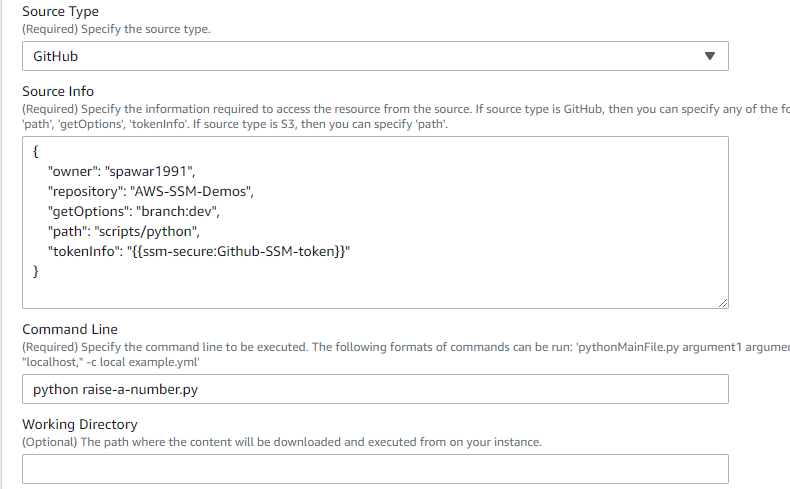
Source Type: Location of the script – GitHub, S3. In this case, choose GitHub.
Source Info: Provides location information for accessing the content. In this example, since the repository is private, you need to provide an access token from GitHub, the owner, repository, and the path to the python script. So we’ll download the script, which includes an example.py script file.
Run Python Script from private GitHub repository
Now, I’ll show you how to execute scripts from private GitHub repositories. Let’s assume that the custom python script in this example is stored in a private GitHub repository. To access this script, you need to create a private access token on GitHub and store it in Amazon EC2 Systems Manager Parameter Store.
Step 1: Create your GitHub personal access token
Create a personal access token for your private GitHub repo to give the Systems Manager access to the playbook. Personal API tokens are a way to provide access to systems to access information from your private GitHub repository. These tokens provide limited access to a subset of repository data as well as the ability to revoke access when needed. You can create a personal access token from the information provided here and then save the token value.
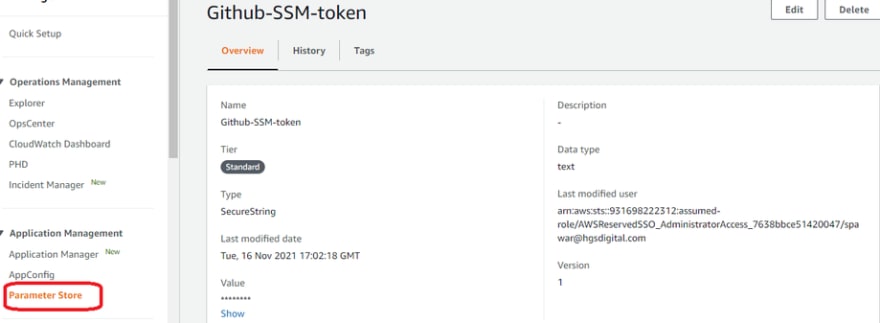
Step 2: Store the tokens in Parameter Store
After creating the personal access token, go to Parameter Store on the SSM console. On the Parameter Store page (Under Application Management), create a parameter and add the token you created on GitHub here, in the Value text box.
Step 3: Reference the Python script located on GitHub
Along with owner, repository, and path, we will add “tokenInfo” which refers to the example-token secure string parameter that we just created. The reference is made using the ssm-secure prefix.
{
"owner": "spawar1991",
"repository": "AWS-SSM-Demos",
"getOptions": "branch:dev",
"path": "scripts/python",
"tokenInfo": "{{ssm-secure:<Parameter-Store-Parameter-Name>}}"
}
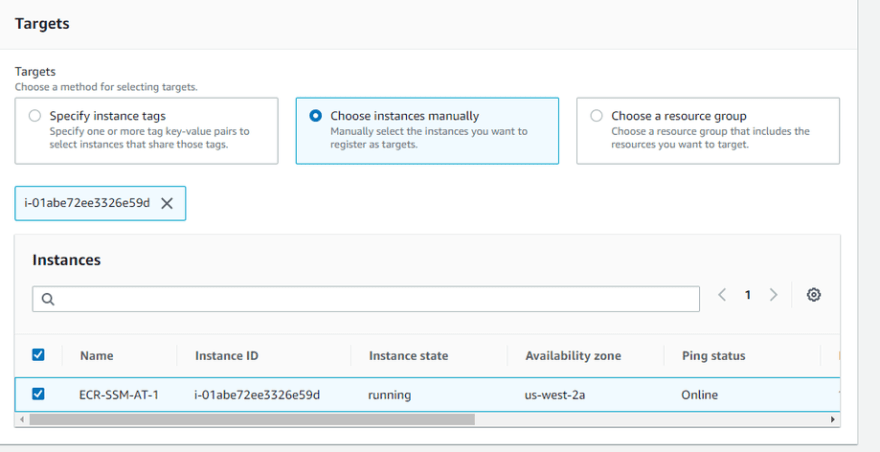
Select the targets where you want to execute the script and click on the run command.
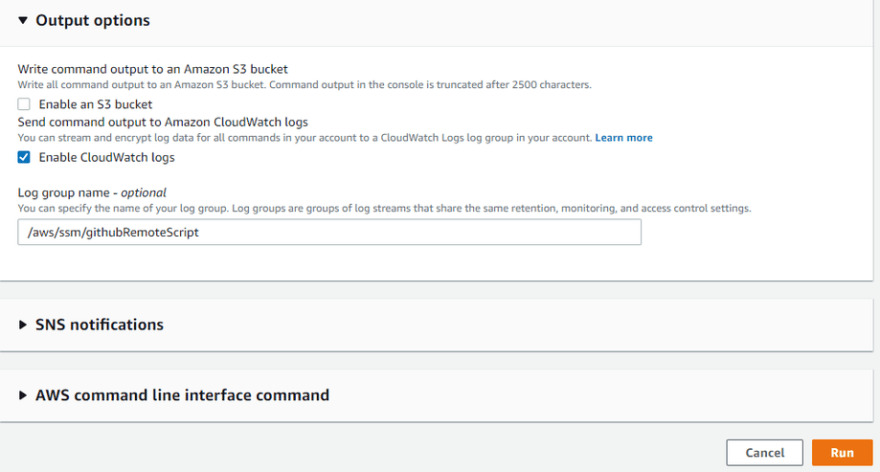
If you want to write command output to the S3 bucket or Cloudwatch Logs, under the Output options section, you can mention the log group.
You can also view the Run command output in the SSM console. Go to Systems Manager → NOde Management → Run Command
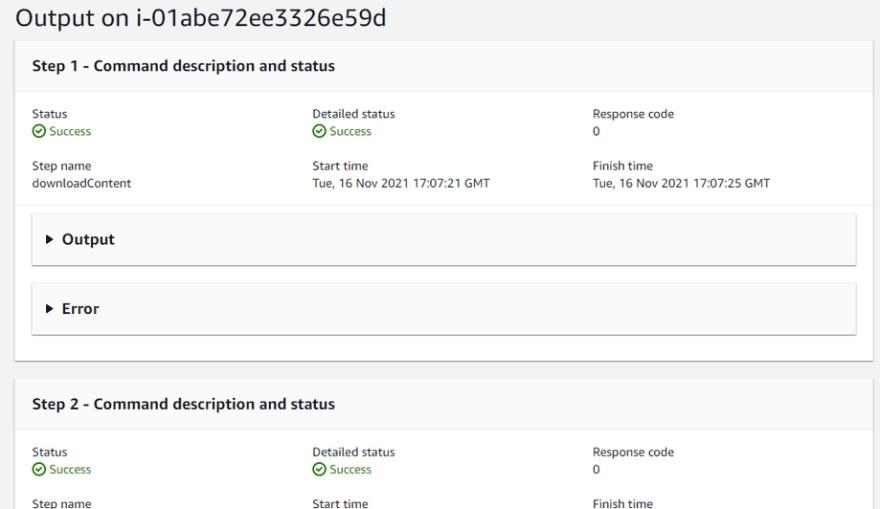
Click on the “Command history” Tab. Open the last run command → check Targets & output section
Now, Click on Instance Id column and you’ll be able to see the execution steps with output and error section. You can expand each section to see the output.
Conclusion
In this, I showed you how AWS Systems Manager is a management platform that lets you use your existing tools to manage your AWS resources and environments. I showed you how to use Systems Manager to run a Python Script on your EC2 instances from a public and private GitHub repository. Using the AWS-RunRemoteScript public document and aws:runShellScript plugins, you can run any script such as Python, Ruby, or even PowerShell scripts or modules.
This content originally appeared on DEV Community and was authored by Swapnil Pawar
Swapnil Pawar | Sciencx (2021-12-24T15:19:15+00:00) Configuration As Code Using Amazon EC2 Systems Manager. Retrieved from https://www.scien.cx/2021/12/24/configuration-as-code-using-amazon-ec2-systems-manager/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.