This content originally appeared on DEV Community 👩💻👨💻 and was authored by merlos
Intro
Metasploitable is a virtual machine image that includes lots of vulnerabilities (on purpose) and that can be used to learn how to hack into a machine.
There are virtual machines
1) Ubuntu 14.04
2) Windows 2008 server
Whereas I was able to setup the Ubuntu virtual machine, I could not find the way to run the Windows one and I could not find any reference of someone that made it work.
Pre-requisites
You need to have installed two tools:
- UTM, that is a Virtual Machine engine that runs in M1 chips
- Homebrew, which is basically a package manager that allows you to install many open source tools easily
Below you have the steps to install them, but if you already have them, you can skip the steps.
Install UTM
- Go to https://docs.getutm.app/installation/macos/
- Click on the button Download from GitHub
- Install the package.
Install HomeBrew
You just need to run this in a console:
/bin/bash -c "$(curl -fsSL https://raw.githubusercontent.com/Homebrew/install/HEAD/install.sh)"
Note: You may need to install Xcode’s Command Line Tools if you don't have them. Just run:
xcode-select --install
At the end of the installation check out that there are some instructions to add to your .zshrc file.
After the installation you should be able to run the brew command. If you run brew doctor you should get Your system is ready to brew.
brew doctor
Your system is ready to brew.
Download the Metaexploit 3 image
Thankfully, the guys of Rapid7, the company behind meta exploit, have already created a two images that can be used in Virtual Box, an open source Virtual Machine Engine. However, VirtualBox is not compatible with M1 chips at the time of writing this article, that's why we are using UTM.
So, now, let's see how to download the images and what we need in order to run Metaexploit 3 in UTM.
- Go to https://app.vagrantup.com/rapid7
- Select the VM you want to download. In this case, the Ubuntu one.
- Download the file
The name of the downloaded file has a weird name (some kind of unique id) and does not have extension, but behind the scenes it is a .zip file. So, you need to rename it.
cd Downloads
mv e41199c7-4afd-42b0-80fd-61ee0126e19d metasploitable3-ub1404.zip
Then unzip the file and enter the folder:
cd metasploitable3-ub1404
ls -la
total 4407704
drwx------@ 6 user staff 192 Nov 30 08:50 .
drwx------@ 588 user staff 18816 Nov 30 09:18 ..
-rw-r--r--@ 1 user staff 258 Oct 29 2020 Vagrantfile
-rw-r--r--@ 1 user staff 6367 Oct 29 2020 box.ovf
-rw-r--r--@ 1 user staff 26 Oct 29 2020 metadata.json
-rw-r--r--@ 1 user staff 2256726016 Oct 29 2020 metasploitable3-ub1404-disk001.vmdk
Next step is to convert the VirtualBox image format .vmdk, into a format that UTM understands. For that we need to install qemu (used by UTM behind the scenes) using brew
brew install qemu
Now, to convert the file just use the following command:
qemu-img convert -O qcow2 -c ./metasploitable3-ub1404-disk001.vmdk ./metasploitable3-ub1404-disk001.qcow2
where -c indicates the source file and -O is for the output format, in this case qcow2
Create the UTM VM
The last step is to setup and run the virtual machine in UTM
Open UTM
Create a new VM (button with symbol
+) and select "Emulate".
3 Click on other and "Other,"
- Click on "Skip ISO boot."
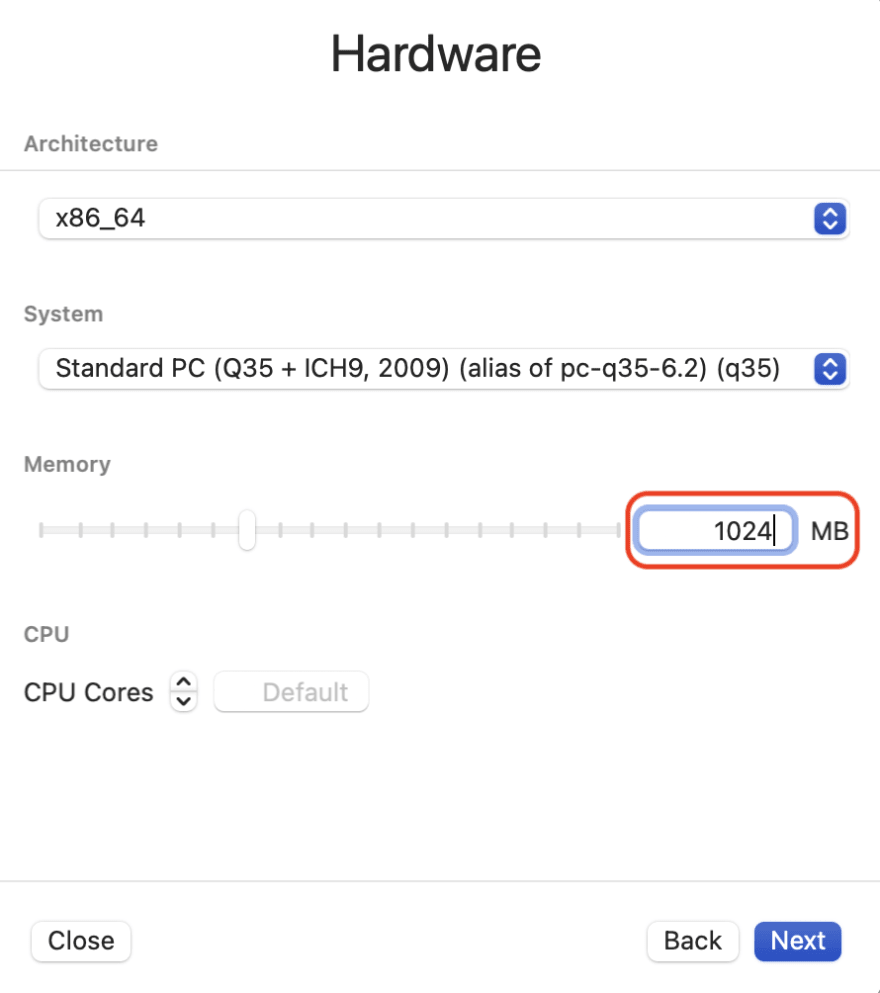
- For hardware, leave it as is. but lower the RAM if you want, it only needs like 1024 MB (maybe less).
For the rest of the options just next, next, next... until you get to the "Summary" page.
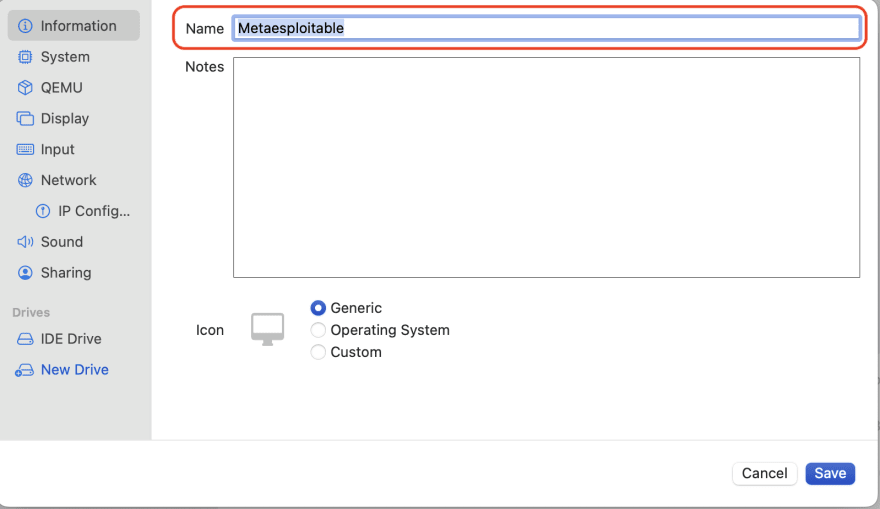
On the summary page, select "Open vm settings" then "Save".
- A new dialog box with the settings of the VM will appear. You can change the name of the VM.
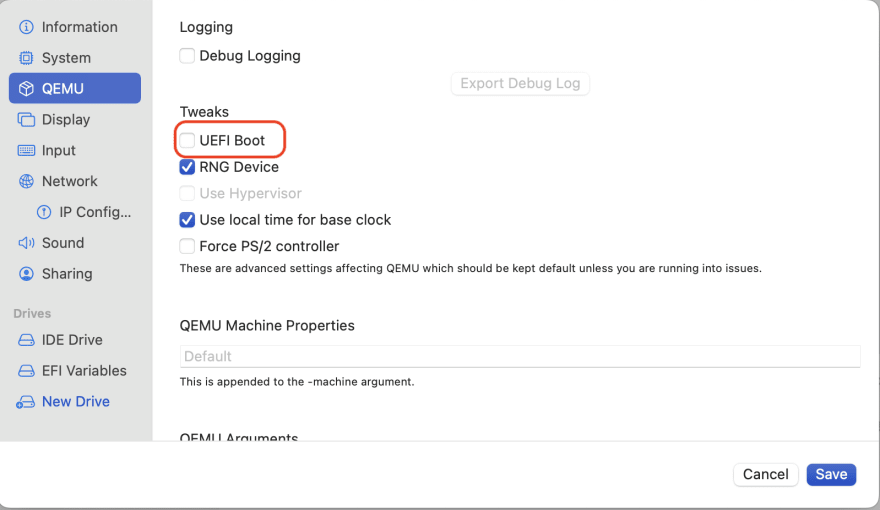
- Click on the "QEMU" in the sidebar and uncheck "UEFI Boot".
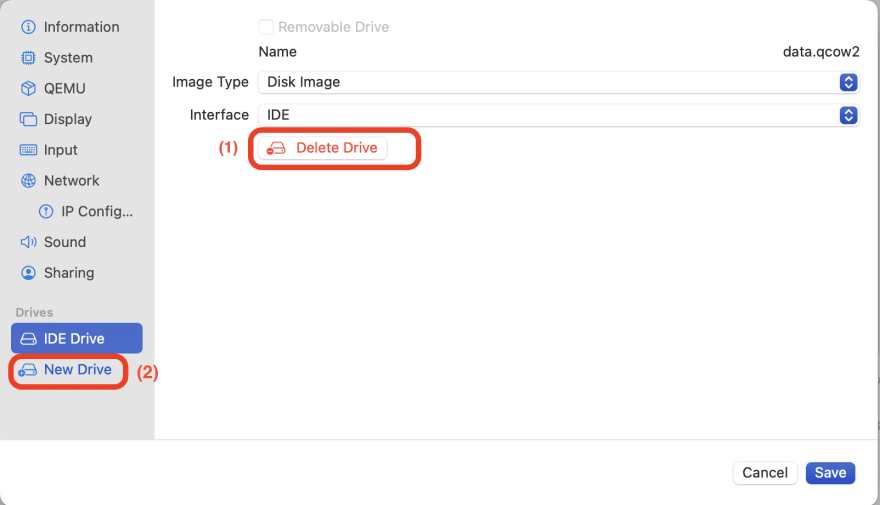
- Under "Drives" section of the sidebar menu, select "IDE Drive" and delete it.
- Now in the Drive section, click on "New Drive", and then in "Import".
Select the
.qcow2file you created earlier with theqemu-imgcommandClick Save and start the VM.
If you need to login you can use username vagrant and vagrant also as password.
Bonus: Metasploitable 2
Now that you have everything in place installing metasploitable2, another Linux machine, is very simple
- Go to https://sourceforge.net/projects/metasploitable/
- And download the
.zipfile - Unzip.
-
Use
qemu-imgconvert
cd Metasploitable2-Linux qemu-img convert -O qcow2 Metasploitable.vmdk Metasploitable.qcow2 Repeat the same steps in UTM as for installing the Metasploitable 3 but now, when you create the new drive, use the
Metasploitable.qcow2file.
To login you can use msfadmin for both username and password.
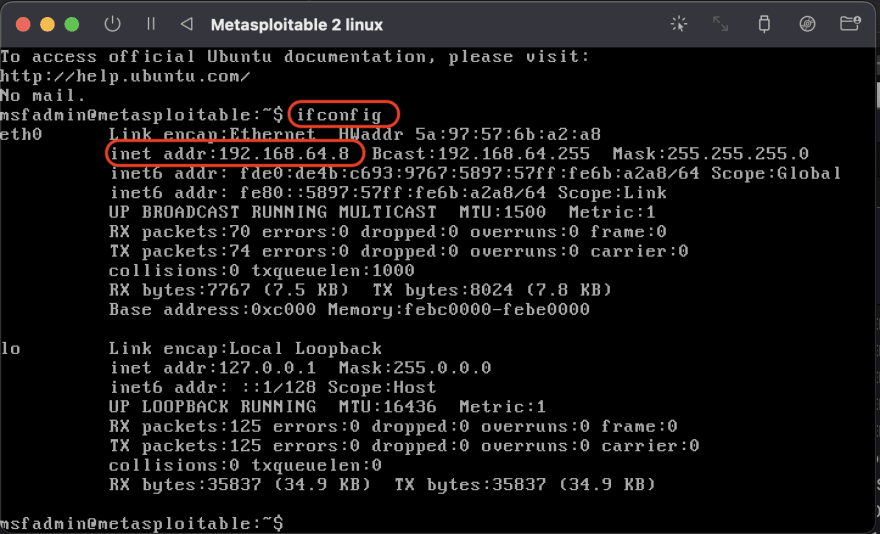
In both machines to get the IP addresses, just run the command
ifconfig
Now you can play around with the VM.
If you found this article interesting and you would like me to write some more articles exploiting the vulnerabilities, just drop a comment below.
EOF
This content originally appeared on DEV Community 👩💻👨💻 and was authored by merlos
merlos | Sciencx (2022-11-30T20:30:44+00:00) How to setup Metasploitable in a Mac with M1 chip. Retrieved from https://www.scien.cx/2022/11/30/how-to-setup-metasploitable-in-a-mac-with-m1-chip/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.