This content originally appeared on DEV Community 👩💻👨💻 and was authored by Denis Sinyukov
If we want to encrypt data, in particular passwords, we have a lot of tools to choose from that allow us to encrypt data. There are a large number of opensource and closed source solutions, both paid and not.
If we want to store or encrypt some information safely, it has to be an opensource solution. They allow us a minimum hope that our data will belong only to us.
Why trust opensource solutions:
- There is a guarantee that there is no special hacker code in it. Because we can see for ourselves what it consists of.
- Mass testing and fixing the source code.
A large number of people use the same password for different accounts and services. That is the reason why so much stolen information is sold on the Internet in the form of databases.
That's why passwords should always be different for all services. They must be complex, of such length that it is hard to remember. Passwords should be changed at least once every six months, and it's hard to do without a password manager.
All this leads us to the idea of using special tools to store passwords.
Today we will talk about password management and data encryption. This will be a popular opensource solution,that you can trust.
Encrypting
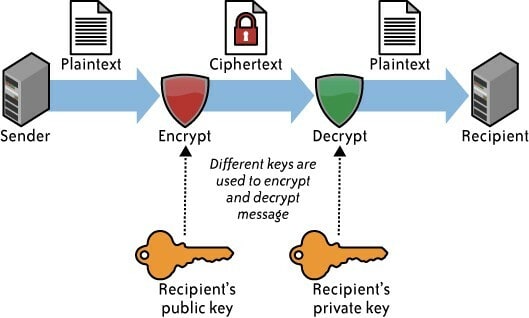
We will encrypt the data using GnuPG, a program for encrypting information. GnuPG can encrypt information and create electronic digital signatures.
The program is released under the GNU General Public License which gives us the ability to freely use and securely encrypt our data.
Installing GPG
sudo apt install -y gpg
Create encryption keys with which we will encrypt everything.
gpg --full-generate-key
- The encryption algorithms are RSI (1).
- The default
keysizeis 3072 bits. We recommend setting the maximum key length to 4096 bits. The longer the key length, the more secure it is. - The lifetime of the key we will make the key - indefinite.
-
Passphrasedoes not replace keys. It is an additional mechanism for additional protection of our data.
As a result, we have a couple of keys generated and can start working with them. Let's add a few add-ons beforehand to make gpg work.
Configuration file
Create a gpg.conf configuration file and edit it. gpg.conf is the standard configuration file read by gpg on startup.
touch ~/.gnupg/gpg.conf
# Prohibit the inclusion of the version string in the ASCII armored output
no-emit-version
# disallow including a comment line in plain text signatures and ASCII armored messages
no-comments
# Display long keyid-formats
keyid-format 0xlong
# Do not include key id's in encrypted packets
throw-keyids
View public keys. pub and sub primary and sub key.
gpg -kView private keys. sec and ssb master and sub key
gpg -K
Exporting and importing GPG keys
We have successfully generated two keys and can use them to encrypt our data. Keeping a bunch of keys only on the computer is not safe, because it can break, get lost, etc. We need to define a place to back up the keys.
GPG allows us to export the public and private keys just to a file which we can take anywhere and then import it back into gpg.
Exporting a GPG keyring
The command exports the public key for the specified keyring (example@email.com).
gpg --export -a example@email.com > public.gpg
The command exports the private key for the specified keyring (example@email.com).
gpg --export-secret-key -a example@email.com > secret.gpg
Now we can save the keys to a flash drive or somewhere else, and then import them back at any time.
Importing a GPG keyring
gpg --import public.gpg
gpg --import secret.gpg
This way we can import and export our keys.
We generate the keys, encrypt the data, export the keys and import them to any other computer.
Working with Passwords
GPG does a great job with passwords and for that there is a pass utility that runs on top of gpg. Pass is a password manager which uses gpg to encrypt data.
Installing the pass app
sudo apt install -y pass
To start working with the utility, you need to initialize the password store with the argument - the keychain id.
pass init example@email.com
We have created a directory~/.password-store.
Pass will work so that each password is stored in a separate file. For example, let's save the role for dev.to.
pass insert social/dev.to.
To view the list of created passwords, use the command which shows one created entry:
pass
Let's do the tree ~/.password-store command, which outputs the whole tree. Our password is in the file ~/.password-store/Social/dev.to.gpg which stores the binary data.
To view the password, use the command: pass social/dev.to. After entering the password, we will get a plain-text password.
Pass also knows how to generate passwords with the command:
pass generate 16
Given that all of our data is just stored in a directory, we can make that directory a git repository and simply push our changes there. All the passwords we create will be stored in the repository, in encrypted form.
Conclusion
I hope you now know about pass and will use it to store your passwords. The utility solves the problem of password management and works safely and securely from the console.
This content originally appeared on DEV Community 👩💻👨💻 and was authored by Denis Sinyukov
Denis Sinyukov | Sciencx (2022-12-15T22:50:46+00:00) How to Securely Store Passwords with GPG & PASS. Retrieved from https://www.scien.cx/2022/12/15/how-to-securely-store-passwords-with-gpg-pass/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.