This content originally appeared on DEV Community 👩💻👨💻 and was authored by Tanmay Shukla
As much as it is so much fun to create resources in cloud like AWS, it is also very important to keep your security checks in place. Because even one security breach is enough to take your cloud infrastructure down in some cases.
So i tell you a little story now, I used to create application on Elastic beanstalk as a developer since its very easy to create and managed which is aws managed service. Then after a while I noticed that elastic beanstalk creates the whole think as a cloudformation stack. One of the drawback of this is, it created the EC2 server with default security group rules (like SSH (port 22) open to anywhere i.e. 0.0.0.0/0 which is BIG NO NO !!)
So everytime EB create, rebuild or update the scurity groups, this SSH rule comes as default. Earlier i used manually delete those ssh rule after warning from Trust Advisor, which is very tedious but most important risky as we never know what could happen if we let SSH port open for even 5 minutes.
Now i found out a way by which you can automatically set the rule in AWS Config (it helps you assess, audit, and evaluate the configurations and relationships of your resources) and delete those rules with AWS SSM(Systems Manager) whenever confid detects that rule in any of your security groups. So lets get started and understand the whole process.
AWS config continuosly monitors the resources and configuration and takes the remediation actions on the basis of config rules.
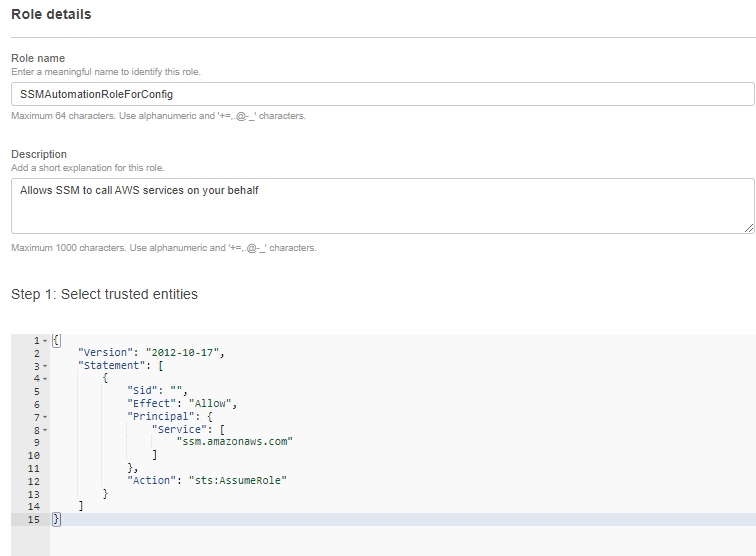
Create the IAM Role for Systems Manager(AWS SSM)
1.) Go to AWS Management Console.
2.) Create a IAM role and give permissions to Allows SSM to call AWS services on your behalf.
Click on create a role, then select AWS services.
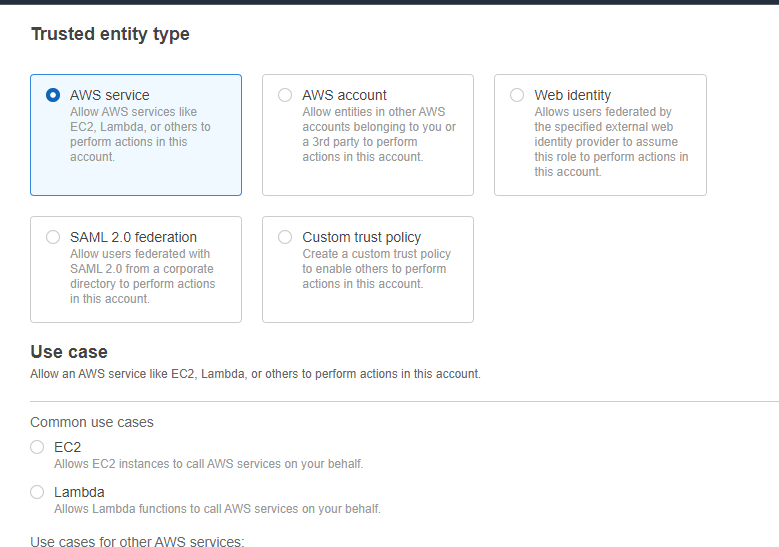
and usecase as Systems Manager.
On Next step choose the AmazonSSMAutomationRole policy from the list.
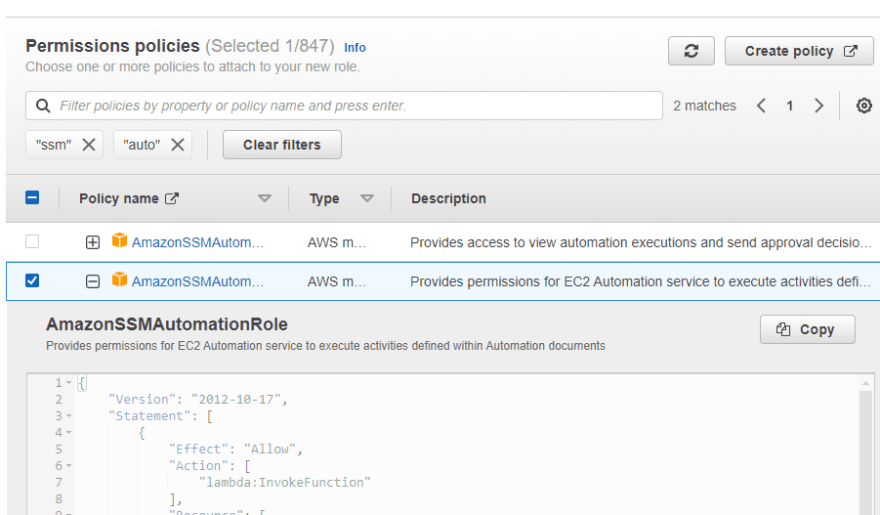
3.) Finally give the name and review the permissions of SSMAutomationRoleForConfig and create the Role
4.) After this attach one inline policy for giving the Role access to delete the Security groups. Below is the IAM policy for that.
{
"Version": "2012-10-17",
"Statement": [
{
"Sid": "VisualEditor0",
"Effect": "Allow",
"Action": [
"ec2:RevokeSecurityGroupIngress",
"ec2:DescribeSecurityGroups"
],
"Resource": "*"
}
]
}
Setup the AWS Config rules for Restricting the SSH access.
5.) Go to AWS Config, click on Add Rule.
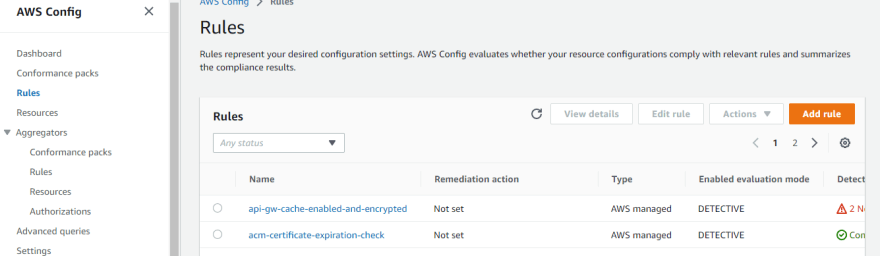
6.) Now select the rule type as AWS Managed rule i.e. restricted-ssh from the Rules list.
7.) Configure the rule and give the intuitive name like restricted-ssh
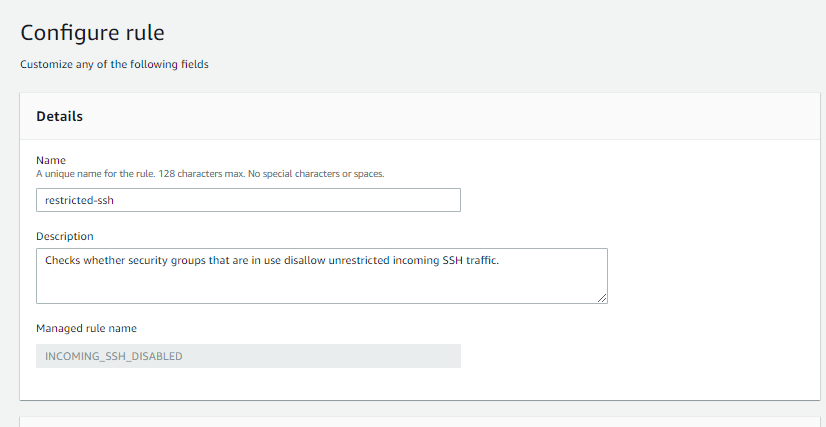
the choose the Resources as security groups in the scope of chnages section in Evaluation mode.
You can leave the other optionals like parameters and tags as default.
Finally review the Config rule and click on Add Rule once done.
Manage the remediation of Config rule.
After creating, select the rule and in the Actions click on Manage Remediation.
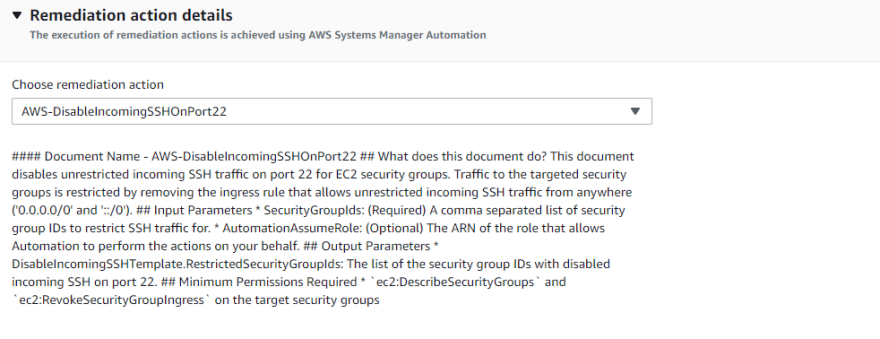
Now select the Remediation action as automatic.

Then choose the remediation action as AWS-DisableincomingSShOnPort22 This will disables unrestricted incoming SSH traffic on port 22 for EC2 security groups.
You can update the Rate limits as per your usecase or leave it default for now. And in the resource Id parameter, select the SecurityGroupIds(or else you can pass the resource ID of noncompliant resources to a remediation action by choosing a parameter that is dependent on the resource type.). But here we want do it for all security groups.
In the next section of parameters, the SecurityGroupIds will be greyed out, so no need to worry about that. And in the AutomationAssumeRole, put the ARN no. of Role that you created in above i.e. SSMAutomationRoleForConfig in our case.
Finally review everything and Save Changes.
Test if it really works 🤔.
- Go that EC2 dashboard, select any instance and edit the inbound rule of that security group as 🚨🚨 SSH (port 22) allow to 0.0.0.0/0 (Warning: Please don't do that with production resources(or serious resources), use only testing servers that doesn't have anything to be compromised in any case.)
- If some body trys to allow ssh (port 22) inbound rule to a critical server so that he can ssh inside it and take away any data or harm the Application in someway.
Even if it is 5 minuted, we won’t even know that someone has taken away the data or has done ssh into the virtual machine. You won’t get any alarm also. But with config we can completely resolve this issue and secure our AWS Cloud infrastructure.
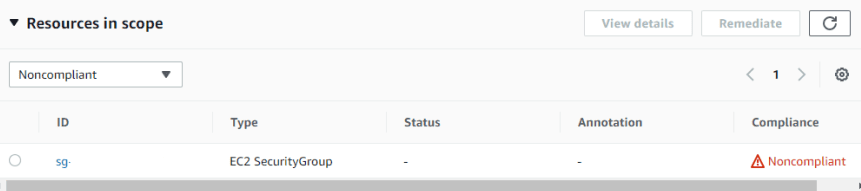
In a while you will see the remediation like below. follow your restricted ssh rule from
And the that ssh rule will be deleted by config rule and AWS SSM Automatic Exection API.
This content originally appeared on DEV Community 👩💻👨💻 and was authored by Tanmay Shukla
Tanmay Shukla | Sciencx (2023-02-13T23:29:36+00:00) Automating the deletion of specifc inbound rules from any security groups in AWS via Config. Retrieved from https://www.scien.cx/2023/02/13/automating-the-deletion-of-specifc-inbound-rules-from-any-security-groups-in-aws-via-config/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.