This content originally appeared on HackerNoon and was authored by Quantum Encryption
:::info Authors:
(1) Kenan Begovic, currently a Ph.D. candidate in Computer Science at Qatar University. He received his MS in Information and Computer Security from University of Liverpool;
(2) Abdulaziz Al-Ali ,received the Ph.D. degree in machine learning from the University of Miami, FL, USA, in 2016 and he is currently an Assistant Professor in the Computer Science and Engineering Department, and director of the KINDI Center for Computing Research at Qatar University;
(3) Qutaibah Malluhi, a Professor at the Department of Computer Science and Engineering at Qatar University (QU).
:::
Table of Links
- Abstract and 1 Introduction
- 2. On crypto-ransomware behavior and methodology
- 3. Detection of encryption
- 4. Conclusion
- Declaration of Competing Interest, CRediT authorship contribution statement, Data availability, and References
4. Conclusion
In closing, our journey through the myriad proposals relating to the detection of pre-encryption and encryption activities by cryptographic ransomware has surfaced some findings and lessons learned. The dynamic nature of ransomware necessitates constant vigilance, innovation, and adaptation. Each of the surveyed methodologies has its own advantages and disadvantages. This all is the reason we present section 4.1, Lessons learned. Our findings in section 4.2 underscore the importance of multi-layered, robust detection mechanisms and the need for more research focusing on encryption as the major motivation for the attack. We hope this analysis serves as a catalyst for further advancements and a guidepost for future endeavors in combating cryptographic ransomware.
\ 4.1. Lessons learned
\ In this paper, we reviewed cryptographic ransomware from the perspective of what we believe is its differentiating factor from other families of cyberattacks, namely encryption. Here we summarize the lessons learned in this survey. Foremost, cryptoransomware is an increasing threat that cripples critical capabilities for both public and commercial services for an extended period of time. When we add the amounts of paid ransoms, losses are in the tens of millions of dollars. They could result in loss of human life, taking into consideration ransomware groups’ “taste” for medical facilities during the time of the COVID-19 pandemic, or even involve themselves in cyber warfare. Secondly, researchers have seen a discrepancy in describing and categorizing ransomware ranging from plain malware to sophisticated cyber kill chains representing the activity of sophisticated APT-like threat actors. We observed ransomware through our cyber kill chain. Thirdly, from a research perspective, we have seen many proposals dealing with different aspects of crypto-ransomware, and most of them take a hybrid approach to deliver the solution. Fourthly, we have seen that despite the academic community’s mature and focused research, commercial solutions mainly apply machine learning and anomaly detection solutions. Finally, we have seen that specialized research around the problem of encryption detection and general control of encryption operations is in the apparent minority among the research topics into crypto-ransomware.
\
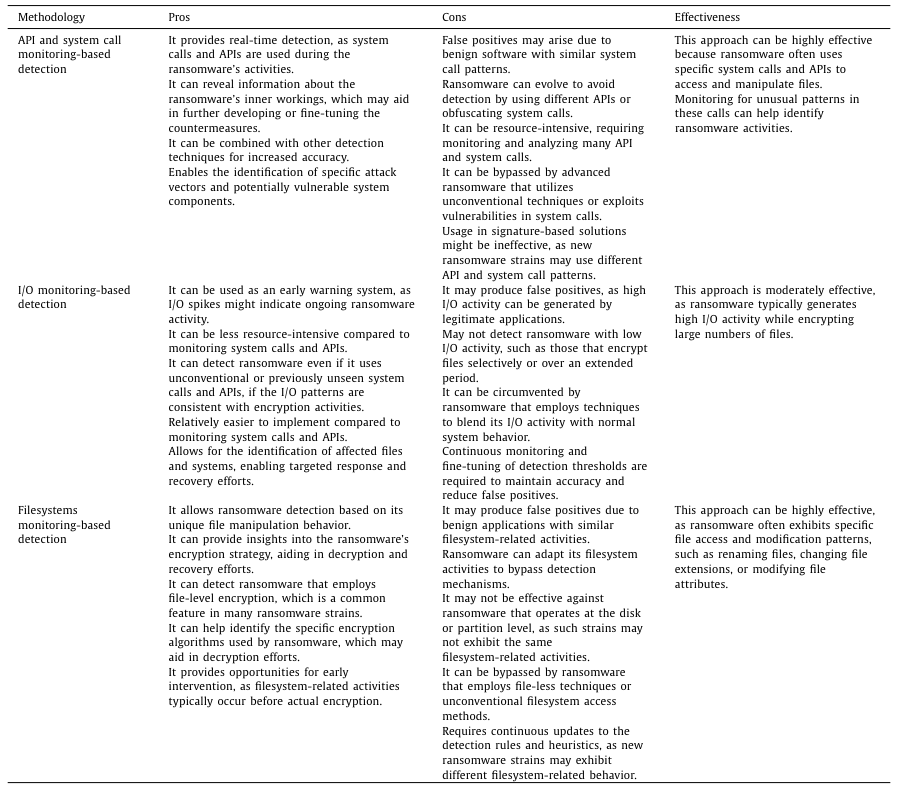
\ Overall, there is no one-size-fits-all answer to the most effective approach. The effectiveness of each method depends on the specific ransomware and its behavior. Combining all approaches and machine learning may offer the best defense against ransomware attacks. Adding to that behavioral analysis and user awareness, effectiveness increases significantly. The information in Table 3 summarizes the pros and cons of each methodology, providing the argument for the hybrid approach advantage. These conclusions result from a review and study of different proposals presented in this survey and our research into commercial solutions that offer capabilities that could be used to detect pre-encryption and encryption activities by ransomware attacks.
\ 4.2. Main findings
\ We focused on the Encryption phase described in our cyber kill chain and divided various methodologies into three major groups:
\ - API and system call monitoring-based detection
\ - I/O monitoring-based detection
\ - file system monitoring-based detection
\ Reviewing the work of researchers through the prism of those three detection methodologies, it was not surprising that, in the case of complete proposals for detection, researchers preferred a hybrid approach utilizing primarily combinations of the three or fewer methodologies, with machine learning being the preferred tool in many proposals.
\ Most of the research was focused on Windows operating systems, but Android mobile operating systems and a variety of Internet of Things applications were also present in the reviewed work.
\ The overall conclusion of this survey is that more methods and techniques described in the surveyed research efforts should be utilized in real-life products by trying to remove some of the common obstacles already described. Detecting pre-encryption and encryption activities provides a high level of confidence that ransomware can be intercepted before doing severe damage. Introducing some benchmark methods in the detection of encryption along with appropriate datasets is a desperate need in this area of research.
\
:::info This paper is available on arxiv under CC BY 4.0 DEED license.
:::
\
This content originally appeared on HackerNoon and was authored by Quantum Encryption
Quantum Encryption | Sciencx (2024-06-15T14:00:28+00:00) Cryptographic Ransomware Encryption Detection: Survey: Conclusion. Retrieved from https://www.scien.cx/2024/06/15/cryptographic-ransomware-encryption-detection-survey-conclusion/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
