This content originally appeared on HackerNoon and was authored by Noonification
How are you, hacker?
🪐What's happening in tech this week:
The Noonification by HackerNoon has got you covered with fresh content from our top 5 stories of the day, every day at noon your local time! Set email preference here.
## Dependency Injection With Dagger 2: What Is It, Key Concepts, and More 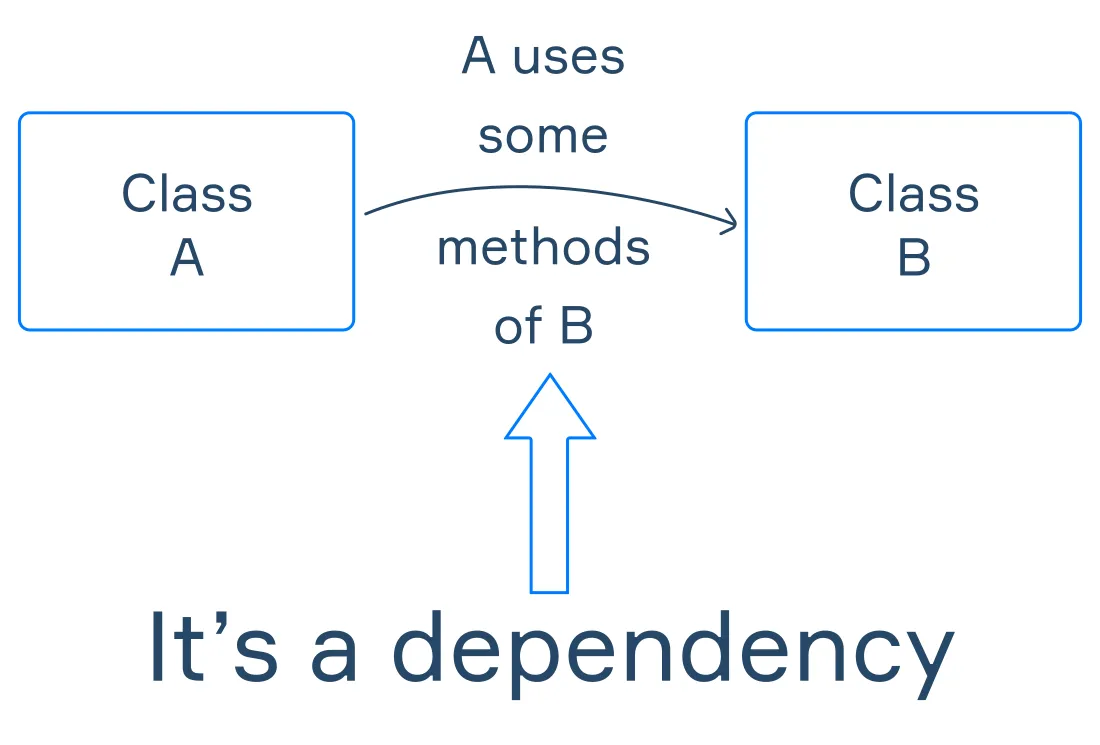 By @dilip2882 [ 21 Min read ]
Dependency Injection (DI) is a technique where the responsibility of creating objects is transferred to other parts of the code. Read More.
By @dilip2882 [ 21 Min read ]
Dependency Injection (DI) is a technique where the responsibility of creating objects is transferred to other parts of the code. Read More.
Architectural Foundations for Startups: Translating Business Into Tech 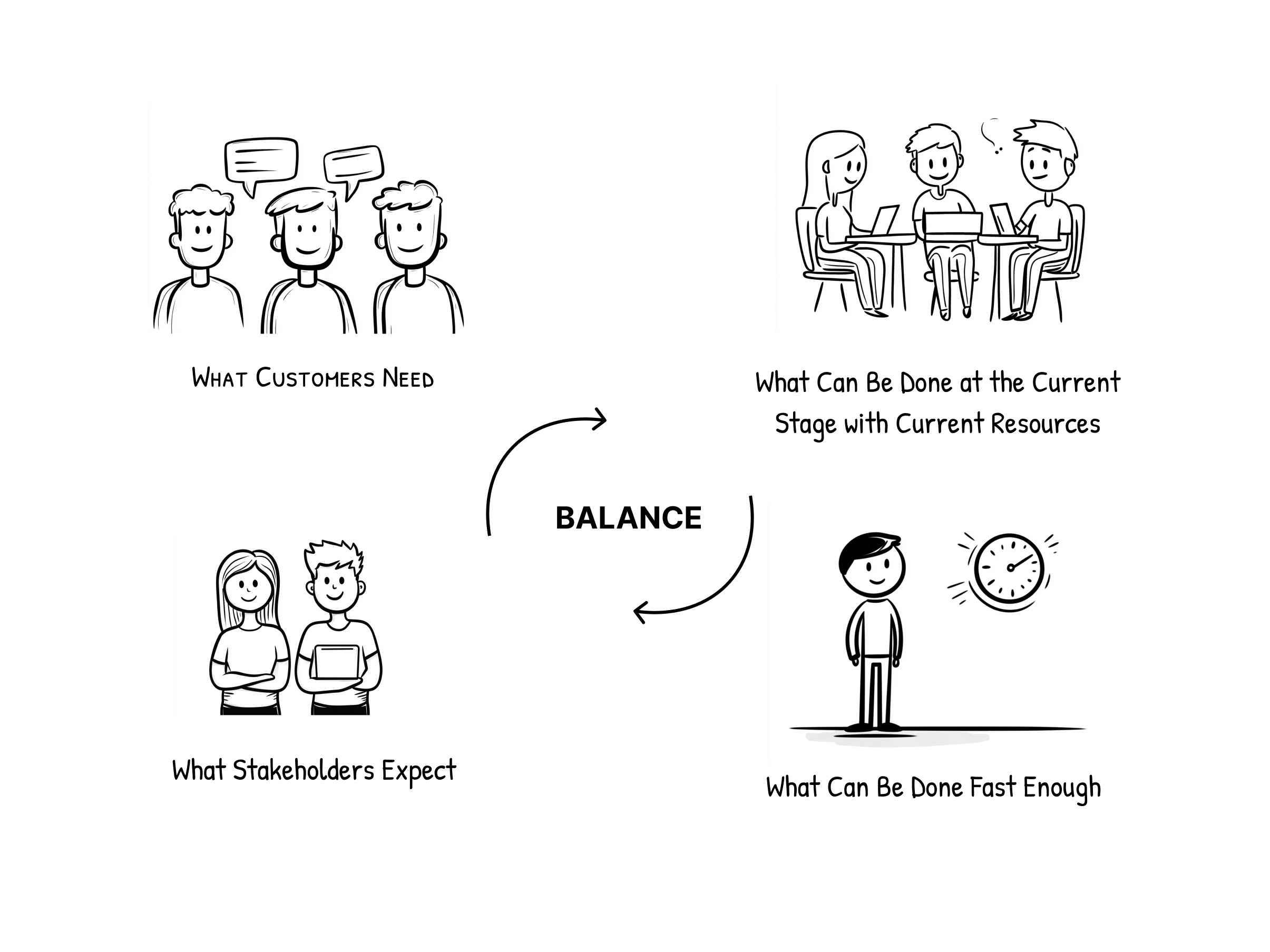
By @pavelgrishin [ 12 Min read ] Planning too far ahead can backfire. It can slow your time to market, reduce flexibility, and increase burn rate. Read More.
Four Things I Did Differently When Writing a Frontend Framework 
By @fpereiro [ 17 Min read ] Four ideas that you perhaps never heard about, in the context of frontend frameworks. Read More.
Pavel Durov Arrest: Is This a Fight Against Crime or an Attempt to Censor Telegram? 
By @ilinskii [ 6 Min read ] Why Pavel Durov was arrested in France? A description of legal conflict between Telegram and EU authorities. Read More.
Why Software Updates Can Lead to Cyberattacks — and What to Do 
By @zacamos [ 6 Min read ]
Every cybersecurity expert recommends keeping software updated — but what if that leads to further risks? Heres how to stay safe. Read More.
🧑💻 What happened in your world this week?It's been said that writing can help consolidate technical knowledge, establish credibility, and contribute to emerging community standards. Feeling stuck? We got you covered ⬇️⬇️⬇️
ANSWER THESE GREATEST INTERVIEW QUESTIONS OF ALL TIME
We hope you enjoy this worth of free reading material. Feel free to forward this email to a nerdy friend who'll love you for it.See you on Planet Internet! With love,
The HackerNoon Team ✌️ 
This content originally appeared on HackerNoon and was authored by Noonification
Noonification | Sciencx (2024-08-28T16:04:20+00:00) The Noonification: Why Software Updates Can Lead to Cyberattacks — and What to Do (8/28/2024). Retrieved from https://www.scien.cx/2024/08/28/the-noonification-why-software-updates-can-lead-to-cyberattacks-and-what-to-do-8-28-2024/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
