This content originally appeared on HackerNoon and was authored by Satyam Pathania
Ever wonder why people say Google is a hacker's best friend? Well, I’m about to show you why.
\ Before we get into the dorky stuff (pun intended), let me introduce myself. I’m Satyam Pathania, a cybersecurity enthusiast who loves exploring new ways to gather information and make hacking a bit easier. I've spent time learning and working with some awesome tools, and today I want to share one of the most underrated tools out there: Google Dorking. Sounds funny, right? But once you see how powerful it is, you’ll be hooked!
My Handwritten Notes 📝
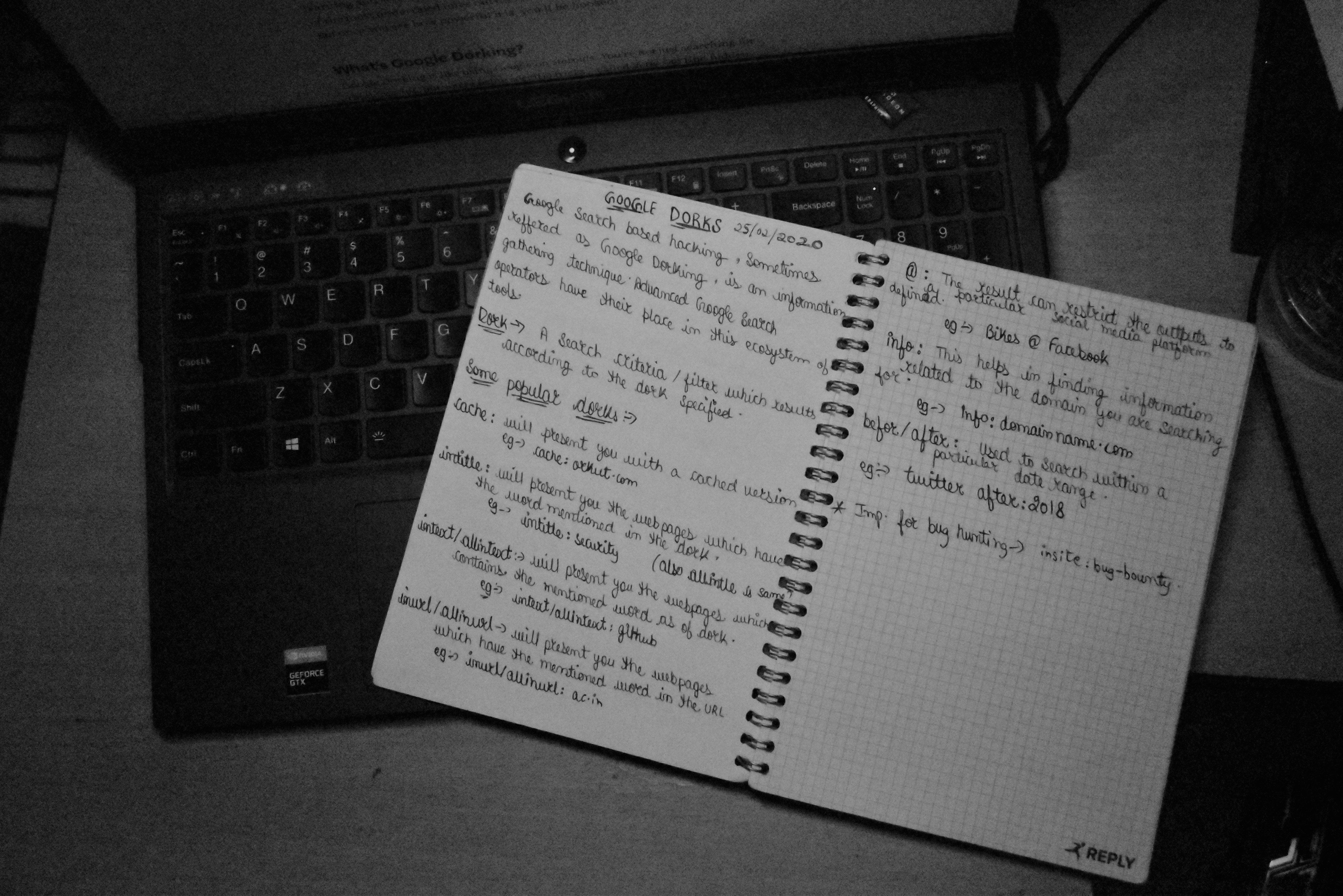
Do you see this notes page of mine? Well, it’s from a special day—my birthday, 25th February 2020. That was the day I first started digging into Google Dorking. With no party to attend and my day wide open after my parents wished me a happy birthday, I started exploring cybersecurity. And boom, I stumbled upon Google Dorks! I wrote down my first Dorking commands in that very notebook. From that day forward, I got hooked on finding all kinds of hidden info using Google searches!
So, What's Google Dorking?
Google Dorking is like using Google on steroids. Normally, we just search for websites or answers. But with Dorking, we use special tricks (aka dorks) to find hidden files, admin pages, passwords, and more. It lets you dig deeper and discover things not easily visible to everyone.
For example, instead of searching "admin login," you can use this: \n inurl:admin
Why Use Google?
You might ask, “Why not use fancy tools for recon?” Well, Google is free, super powerful, and used by everyone with a phone or computer. It lets you use dorks to find things that are otherwise hard to access. And when you’re gathering info before an attack (for legal reasons of course), this can give you a huge head start.
Dorks You Should Know About
Here are some useful Google dorks to level up your search skills:
- site.com – Get results only from specific sites.
- inurl– Find URLs containing the word "admin."
- intitleof – Search for pages with "index of" in their title.
- filetype– Search for specific file types (e.g., PDFs).
- | (OR) – Combine results, like searching two sites at once.
- - (Minus) – Exclude certain results.
- link.com – Find pages linked to a specific site.
Example Combos to Try
- Finding subdomains: \n
site:*.example.com - Finding vulnerable pages: \n
site:example.com inurl:/app/kibana - Finding sensitive data: \n
site:example.com "password, admin, keys, tokens"
These examples are just the tip of the iceberg. You can combine dorks in creative ways to gather more info about a target!
Further Resources to Check Out
You can find more useful dorks on the Google Hacking Database.
Last Words
I hope this article gave you some insight into the power of Google Dorking. Got any questions? The comment box is always open! Don’t forget to share this with your friends to spread the knowledge in the infosec community. Stay tuned for more informative content! 🔥
:::tip Enjoyed this article?
If you found this helpful and want to support my work, feel free to buy me a coffee! Your support will help me get hardware devices, which I’ll use to create more hands-on cybersecurity content and share my experiences with you all.
:::
Got questions or need help? Just give me a shout. Happy hacking!
\
Hacking skills are like virginity — once you lose them, you can never get them back! ~ Satyam Pathania
\
This content originally appeared on HackerNoon and was authored by Satyam Pathania
Satyam Pathania | Sciencx (2024-10-21T00:23:40+00:00) Google Dorking: A Hacker’s Best Friend. Retrieved from https://www.scien.cx/2024/10/21/google-dorking-a-hackers-best-friend/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
