This content originally appeared on DEV Community and was authored by Marcel.L
What is an Azure Logic app?
Azure Logic Apps is a cloud-based platform for creating and running automated workflows that integrate your apps, data, services, and systems. With this platform, you can quickly develop highly scalable integration solutions for your enterprise and business-to-business (B2B) scenarios. As a member of Azure Integration Services, Logic Apps simplifies the way that you connect legacy, modern, and cutting-edge systems across cloud, on premises, and hybrid environments.
What is Azure Private Link (Private Endpoint)?
Azure Private Link (Private Endpoint) allows you to access Azure PaaS services over a Private IP address within the VNet. The PaaS resource gets a new private IP via a virtual network interface (NIC) on your Virtual Network (VNET) attached to the PaaS resource or service, making the resource truly an internal private resource to your virtual network. When you send traffic to the resource that has been private endpointed, it will always ensure traffic stays within your VNet boundary.
What's new in Azure Logic apps?
There has been some major architectural changes and improvements made in recent days to Azure Logic apps (multi-tenant implementation), especially the new logic apps runtime which is a re-hostable containerised, single-tenant runtime, which is built on top of the Azure Functions runtime, adding some excellent new features that we can now utilise in our logic apps. Such as enabling managed service identity (MSI), cross-platform support, local development and testing using VSCode, enabling new advanced networking features such as private endpoints which we will focus on in todays tutorial or even running our logic apps in a dedicated compute resource in Azure, Docker or Kubernetes environments.
What do we need?
- Azure Virtual Network: We will need either a new or an existing VNET in which we can attach our logic app private endpoint interface.
- Azure Private DNS Zone: For this tutorial we will also create a Private DNS zone to host our private endpoint DNS Configuration.
- Azure Logic App: We will need to create the new single-tenant logic app as described above.
- Private Endpoint: We will use a private endpoint to connect our logic app to our VNET.
Creating an Azure Virtual Network (VNET)?
For this section I will be using Azure CLI in a powershell console. First we will log into Azure by running:
az login
Next we will create a resource group, and a VNET by running:
# variables.
$resourceGroupName = "MyLogicAppRG"
$vnetName = "LogicAppNet"
$subnetName = "LogicAppSub"
$region = "uksouth"
# Create a resource resourceGroupName
az group create --name "$resourceGroupName" --location "$region"
# Create a new Vnet
az network vnet create `
--name "$vnetName" `
--resource-group "$resourceGroupName" `
--address-prefixes 10.2.0.0/16 `
--subnet-name "$subnetName" `
--subnet-prefixes 10.2.0.0/24
Creating an Azure Private DNS Zone?
We will need to register our private endpoint in DNS so for this step we will create a Private DNS Zone and link the Azure services DNS Zone configuration for azurewebsites.net because our new logic app runtime is within an App Service Plan (ASP) we will configure the zone as privatelink.azurewebsites.net.
To see more detailed information on DNS configurations for private endpoints please see DNS Integration Scenarios for additional information, as well as Private link DNS Zone configuration
Next we will run:
# Create Private DNS Zone
az network private-dns zone create `
--resource-group "$resourceGroupName" `
--name "privatelink.azurewebsites.net"
# Link Private DNS Zone with VNET
az network private-dns link vnet create `
--resource-group "$resourceGroupName" `
--name "$vnetName-DNS-Link" `
--zone-name "privatelink.azurewebsites.net" `
--virtual-network "$vnetName" `
--registration-enabled "true"
Creating an Azure Logic app (Single-tenant)?
Now that we have everything in place we will create our logic app. Navigate to the Azure portal and go to the resource group we created and create a new Logic app (Standard) resource.
Under the Basics blade, add the following Instance Details:
| Name | Value |
|---|---|
| Type | Standard (Preview) |
| Logic App name | {Name} |
| Publish | Workflow |
| Region | {Region} |
Under the Hosting blade, add the following Plan:
| Name | Value |
|---|---|
| Plan type | Workflow Standard |
| Windows Plan | {ASP - App Service Plan} |
| Sku and size | {SKU} |
Move to the next blade Monitoring and enable/disable Application Insights and then add any Tags. Click on Review + create and create the new logic app.
Creating the Private Endpoint?
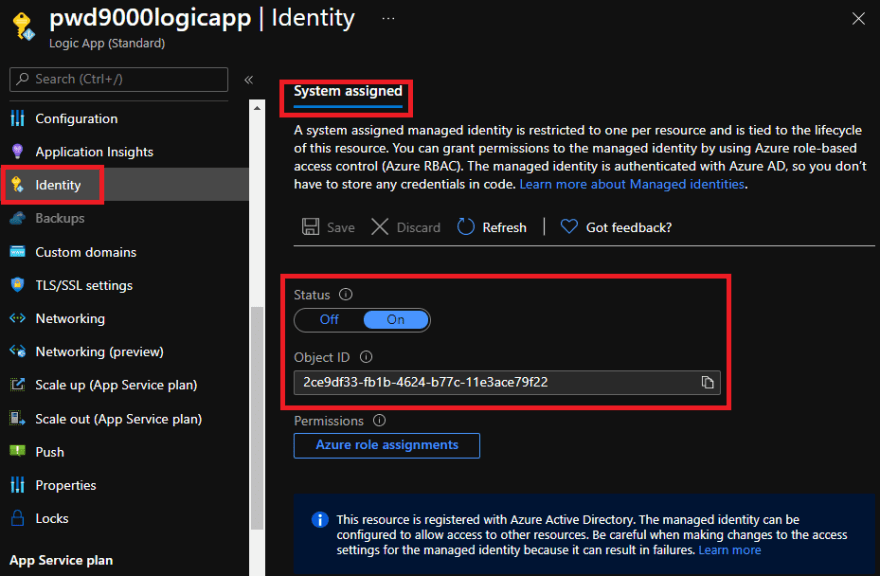
Before we continue to our last step, also note that our newly created Logic App has already been enabled with a system assigned managed identity. Pretty neat!
Next we will create our private endpoint. Select the Networking blade and click on Private endpoints.
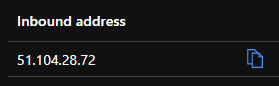
Note: You will see that our inbound address to access our logic app is currently configured using a public endpoint (Public IP address).
Under the Private Endpoint connections blade, click + Add and add the following:
| Name | Value |
|---|---|
| Name | {Name private endpoint} |
| Subscription | {Subscription} |
| Virtual Network | {Virtual Network Name} |
| Subnet | {Subnet Name} |
| Integrate with private DNS Zone | Yes |
Note: You will now see that our inbound address to access our logic app has changed and is configured to use our private endpoint (Private IP address from our VNET).
Make a note of the private IP and navigate to the Azure Private DNS zone we created earlier. Click on + Record set and add the following:
| Name | Value |
|---|---|
| Name | {Name of Logic App} |
| Type | A |
| TTL | 1 Hour |
| IP address | {Private Inbound IP of Logic App} |
That is it! We have now secured our logic app to be a completely internal resource keeping it within our network boundaries as if it was an internally hosted resource inside of our Virtual Network.
Testing our Logic App?
Let's test out our Logic App and see what happens if we try to access it from an external source vs. a source from our VNET such as a Virtual machine running inside of our VNET.
HTTP POST Url from an external source:
HTTP POST Url from an internal Virtual Machine running inside of our VNET:
I hope you have enjoyed this post and have learned something new. You can also find the code samples used in this blog post on my Github. ❤️
Author
Marcel.L - pwd9000@hotmail.co.uk
This content originally appeared on DEV Community and was authored by Marcel.L
Marcel.L | Sciencx (2021-06-19T15:11:43+00:00) Securing Azure Logic apps with Private Endpoints. Retrieved from https://www.scien.cx/2021/06/19/securing-azure-logic-apps-with-private-endpoints/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.