This content originally appeared on Level Up Coding - Medium and was authored by Haiko van der Schaaf
How to secure your AWS account

I was triggered by a tweet where an AWS account was hacked and the surprise bill was $60.000, yikes.
As I am promoting using and experimenting with AWS technology here, I feel compelled to share with you 5 best practices on securing your AWS account so this hopefully will not happen to you too. Let’s walk through them.
1. AWS root account security
The second thing you need to do when creating an AWS account is to create another IAM user for administrative tasks. Use your root account as less as possible and create a non-root account with administrative permissions to set up cloud resources.
A best practice is to delete any programmatic access keys associated with the root user. If a PEM file or DER certificate exists for the root account, it is best to delete those keys immediately¹.
2. Enable MFA
Enable multiple-factor authentication as extra defense for your root account as well as for other non-root IAM users with extensive privileges.
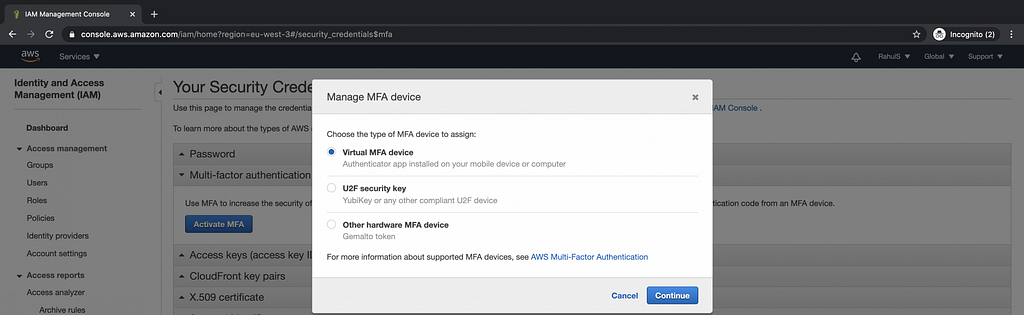
There are several options, but choosing a ‘Virtual MFA device’ is the most simple as you can use your mobile with ‘Google Authenticator’ or ‘Microsoft Authenticator’. More info here.
3. Do not share access keys in code
A common mistake is to use access keys in code. The problem with code is that it gets distributed, forked, and probably tested on a continuous integration tool. It is all over the place.
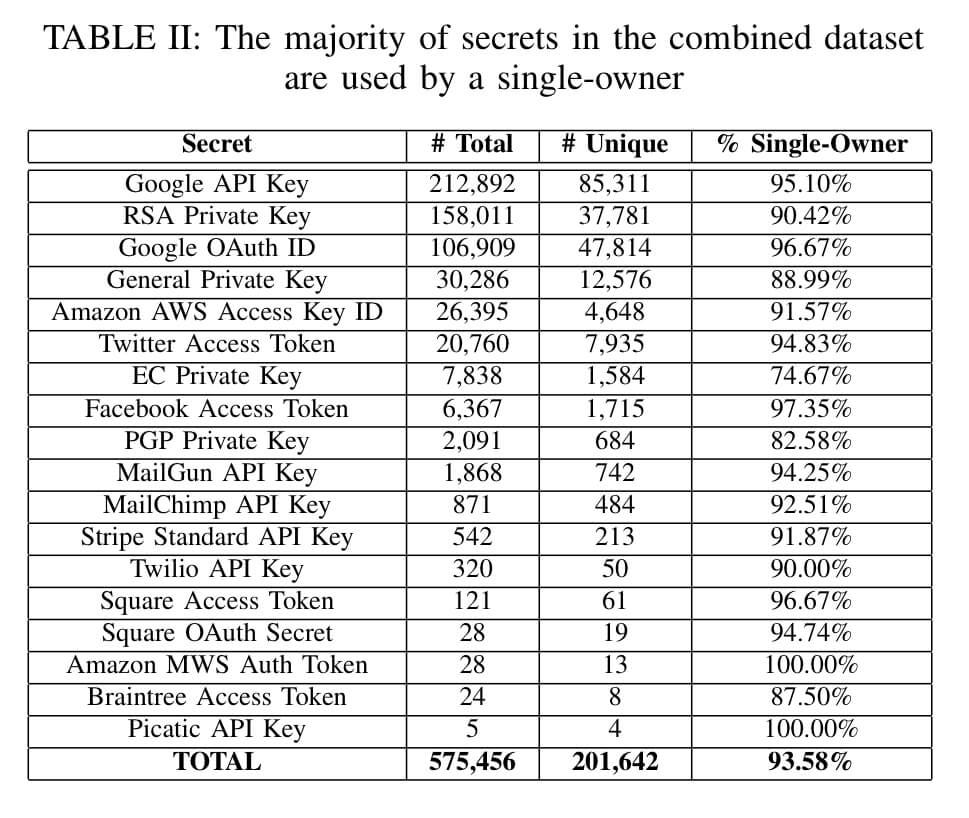
There are tools such as Git-Secrets to scan code repositories on secrets². Use environment variables and tools such as the ‘Parameter Store’ to store your secret keys.
4. Use specific users
When you need to give external services access to your AWS account and you need access keys for this, create a specific user with only the permissions needed to execute the task.
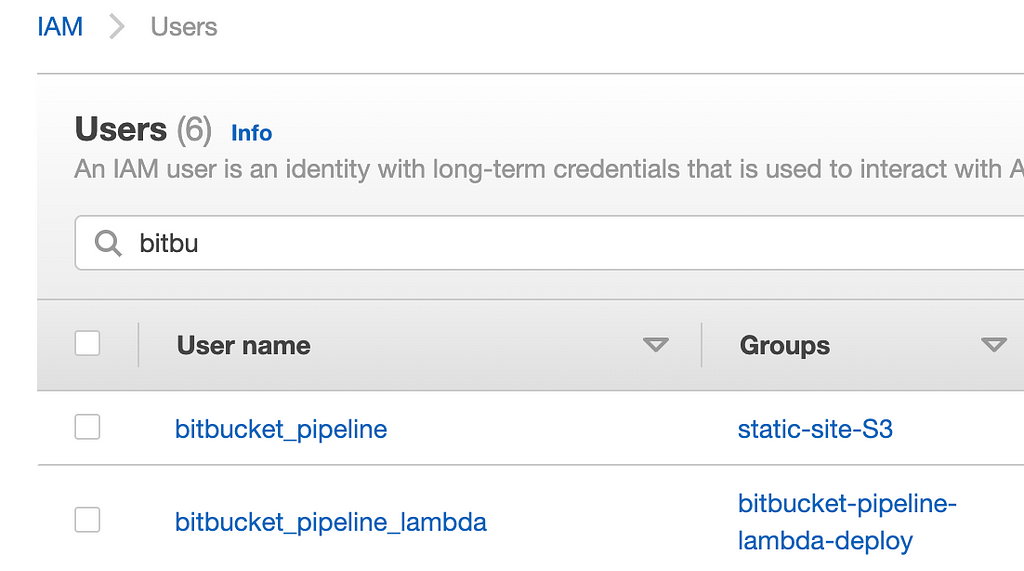
For example, when you deploy your code using a continuous delivery tool such as bitbucket pipeline to S3, only add S3 permissions to that user.
5. Billing alerts
Keep control of your bill by using alerts when your monthly costs. This way you will get notified as soon as costs are going in the wrong direction. Using AWS Budgets you can set multiple thresholds and corresponding alerts giving you notice of exceeding the threshold by email or slack notification.
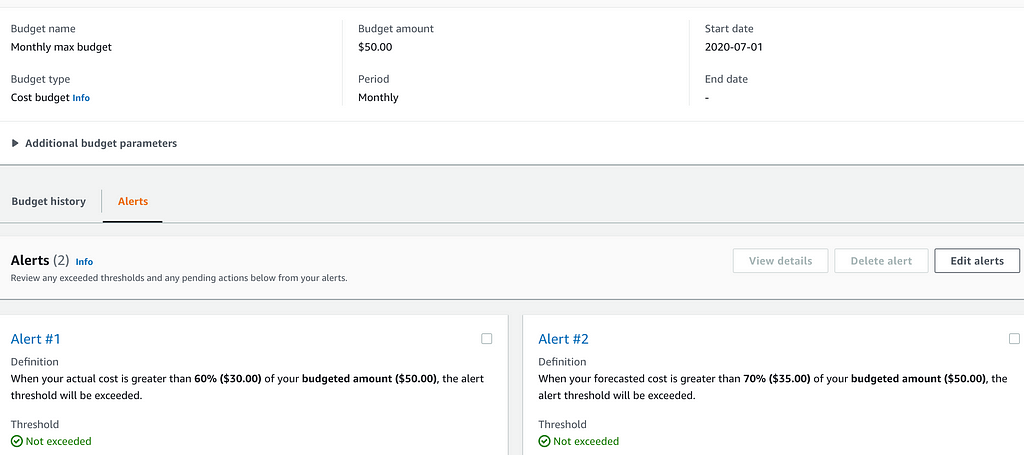
Another way to reduce the risk of billing surprises is ‘’AWS Cost anomaly detection’. Not as simple as AWS Budgets, but it uses machine learning to detect anomalies in your costs.
There you have it, 5 best practices to keep your AWS account safe and reduce the risk of nasty billing surprises. If you know some more, please share it and spread the knowledge so everyone can experiment safely in the cloud.
Have fun playing in the cloud!
References
- https://www.theserverside.com/blog/Coffee-Talk-Java-News-Stories-and-Opinions/AWS-root-account-best-practices
- https://spectralops.io/blog/top-9-git-secret-scanning-tools/
5 best practices for AWS Cloud safety was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Haiko van der Schaaf
Haiko van der Schaaf | Sciencx (2022-06-20T11:50:12+00:00) 5 best practices for AWS Cloud safety. Retrieved from https://www.scien.cx/2022/06/20/5-best-practices-for-aws-cloud-safety/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
