This content originally appeared on DEV Community and was authored by Sato Kenta
Tokens are essential in the realm of digital security, functioning to authenticate and authorize users for access to specific resources. Think of tokens as digital equivalents of keys or tickets required to access protected online services, much like needing a ticket to enter a concert venue. This system safeguards against unauthorized access, ensuring stringent security.
Various Kinds of Tokens
There are several types of tokens, with JSON Web Tokens (JWT) and Bearer tokens being the most widely used. The choice of token type depends on the security requirements and architecture of the application in question.
In-Depth Look at JSON Web Tokens (JWT)
Understanding JWT
JWT, an acronym for JSON Web Token, is a compact, URL-safe means for securely transferring information between two entities. This capability is particularly beneficial for API communications, ensuring that data exchanges between a client and server remain secure.
How JWT Works
A JWT comprises three main parts:
- Header: Contains metadata about the token's type and the algorithm used for signing.
- Payload: Includes the claims or assertions about a particular entity, typically a user, along with any additional data.
- Signature: Validates the token’s origin and ensures the payload has not been tampered with.
During each API request, the client includes the JWT in the HTTP header. The server then verifies the token's authenticity, and if valid, allows the request; if not, it denies access.
Pros and Cons of JWT
Advantages:
- Compact Form: Its small size is suitable for HTTP headers and URL parameters.
- Self-contained: JWT carries all the necessary information for authentication, reducing the need for database calls.
- Scalability: Its compact nature makes it ideal for distributed applications.
Disadvantages:
- Irreversible: Once issued, a JWT cannot be easily revoked before its expiration.
- Size Issues: Larger payloads increase token size, which may impact performance.
Insights on Bearer Tokens
What are Bearer Tokens?
A Bearer token serves as a security credential that grants the bearer access to specific resources. The principle is straightforward: possessing the token grants access permissions.
Bearer Tokens in Action
Bearer tokens are generated by an authentication server and provided to the client, which then uses them to access secure services. The token is included in the HTTP Authorization header of the client’s requests.
Pros and Cons of Bearer Tokens
Advantages:
- User-Friendly: Simple to implement and use.
- Adaptable: Easily integrates with various authentication methods.
- Opaque: Enhances security by preventing clients from viewing or modifying the token’s content.
Disadvantages:
- Revocation Challenges: Lacks built-in mechanisms for immediate invalidation.
- Non-standard Formats: Varied structures can lead to inconsistencies.
JWT vs. Bearer Tokens: A Comparative Analysis
Structure and Content:
- JWT: Structured format that encloses user data or claims.
- Bearer Token: Opaque with no embedded information.
Use Cases:
- JWT: Suitable for both authentication and data transfer; ideal for stateless environments.
- Bearer Token: Primarily used for authentication; preferred in less complex scenarios.
Deciding Between JWT and Bearer Tokens
Your choice between JWT and Bearer tokens should be guided by the specific needs of your project. Opt for JWT if you require detailed, transportable tokens; choose Bearer tokens for straightforward, secure authentication in simpler or more dynamic setups.
Best Practices for Token Management
To enhance security when using tokens, follow these best practices:
- Secure Transmission: Always send tokens over HTTPS to protect them from interception.
- Token Expiry: Implement and enforce token expiration policies to reduce the risk of misuse.
- Revocation Methods: Establish processes for invalidating tokens when necessary.
- Safe Storage: Store tokens securely, preferring HTTP-only cookies over local storage.
Practical Use of JWT and Bearer Tokens with Apidog
Apidog offers robust features that streamline working with JWT and Bearer tokens.
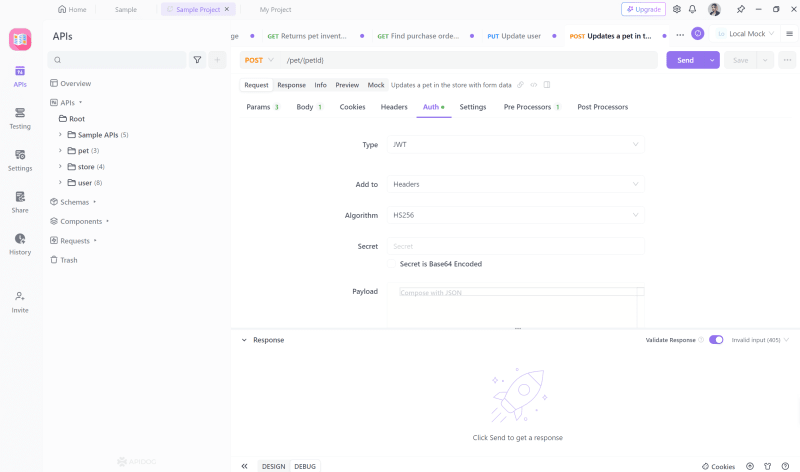
Managing JWT in Apidog
Apidog excels in handling JSON Web Tokens, offering an intuitive interface for token generation, dynamic management, and seamless integration into API requests, simplifying the entire JWT workflow.
Authenticating with Bearer Tokens in Apidog
Authenticating APIs using Bearer tokens in Apidog is straightforward. Open the desired API in Apidog, switch to "Debug" mode, go to "Request" > "Auth", select "Bearer Token" as the type, and enter the token in the provided input box.
It’s crucial to keep Bearer tokens confidential and periodically update or revoke them to maintain security.
Conclusion
Grasping the differences between JWT and Bearer tokens is crucial for securing API interactions effectively. By incorporating best practices and leveraging tools like Apidog, you can ensure robust and scalable API security. Equip yourself with the knowledge and confidence to navigate the landscape of digital authentication securely.
This content originally appeared on DEV Community and was authored by Sato Kenta
Sato Kenta | Sciencx (2024-06-27T10:36:40+00:00) Understanding JWT and Bearer Tokens: What Every Developer Should Know. Retrieved from https://www.scien.cx/2024/06/27/understanding-jwt-and-bearer-tokens-what-every-developer-should-know/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.