This content originally appeared on Level Up Coding - Medium and was authored by Josh Thorne
Using AWS CDK and Data Protection Policies to Secure Sensitive Data in CloudWatch Logs

Introduction 👋
If you are building in AWS you will almost always require the use of CloudWatch for logging purposes. When logging to CloudWatch, users should be aware of its data protection features to ensure you are not unnecessarily exposing sensitive data to unintended users.
In this short article we will cover how to mask protected data, such as email addresses, in CloudWatch logs. This guide will walk you through setting up a basic example to demonstrate these capabilities.
⚠️ Note: It is recommended to never log PII or sensitive information to CloudWatch. Please refer to the AWS documentation for best practices on what should not be logged: AWS Logging Best Practices
Working Example 💻
We will utilise AWS CDK to demonstrate the power of CloudWatch data protection policies.
The Code 🧑💻
First, create a new TypeScript CDK app. Follow the instructions in the CDK documentation to get started.
Once your project is set up, we will modify the code to create a data protection policy that masks email addresses, then assign this policy to a Lambda function’s log group:
const dataProtectionPolicy = new logs.DataProtectionPolicy({
name: "EmailDataProtectionPolicy",
identifiers: [
new logs.DataIdentifier(logs.DataIdentifier.EMAILADDRESS.toString()),
],
});
const logGroup = new logs.LogGroup(this, "LambdaLogGroup", {
dataProtectionPolicy,
});
new aws_lambda_nodejs.NodejsFunction(this, "LambdaFunction", {
architecture: aws_lambda.Architecture.ARM_64,
runtime: aws_lambda.Runtime.NODEJS_20_X,
entry: path.join(__dirname, "handler.ts"),
logGroup,
});To test the functionality of the data protection policy, we’ll create a simple Lambda function that logs the event passed into it.
Create a handler.ts file with the following code:
export const handler = async (event: any) => {
console.log("Event: ", JSON.stringify(event));
const response = {
statusCode: 200,
body: JSON.stringify({
message: "Hello from Lambda!",
input: event,
}),
};
return response;
};Deploy the stack using the following command: cdk deploy
This command will deploy the Lambda function along with the associated CloudWatch log group with the data protection policy applied.
Testing the Setup 🧪
Open the AWS console and invoke the Lambda function with a test event containing an email address:
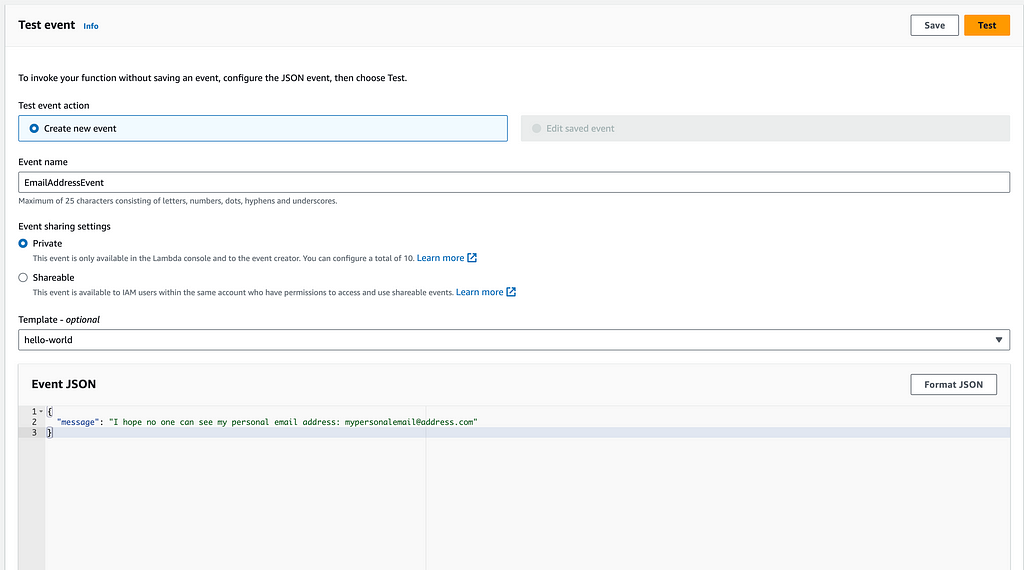
After invoking the function, navigate to the CloudWatch logs for this function. You should see that the email address is masked in the logs:
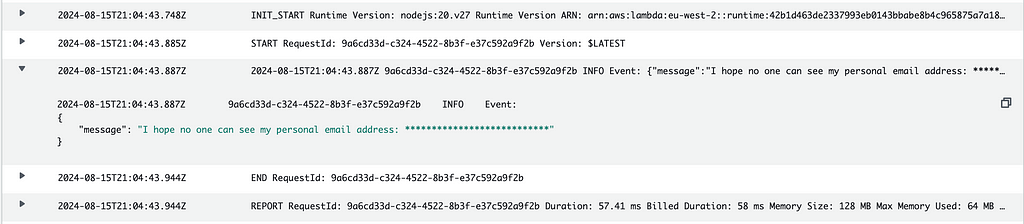
Unmasking the Data 😷
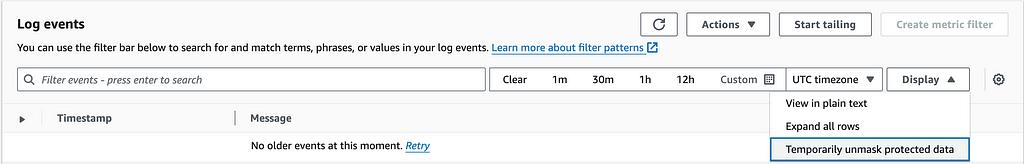
One of the powerful features of CloudWatch masking is the ability for specific users to unmask protected data. To do this, log in with a user that has the logs:Unmask permission.
Navigate back to the same CloudWatch log group, click the Display dropdown, and select Temporarily unmask protected data :
You will now be able to view the previously masked email address:
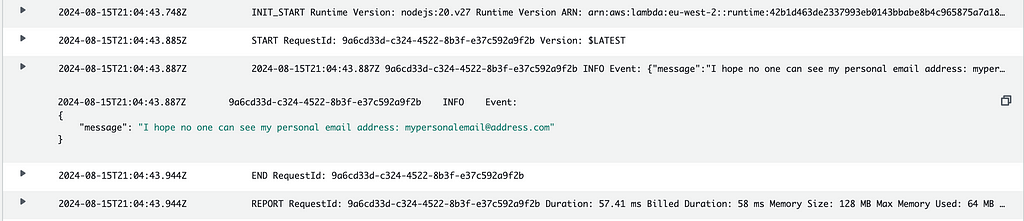
This feature allows you to delegate access to protected data to specific users securely.
Account-Level Data Protection Policies 🌍
Managing data protection policies individually for each log group can be cumbersome, especially in large AWS accounts. AWS provides the option to apply data protection policies at the account level, which will automatically apply to all log groups within the account.
Refer to the AWS documentation for more details on applying account-wide data protection policies. This can also be done using CDK via the CfnAccountPolicy construct.
Summary 🎬
Thanks for reading! In this article, we’ve explored how to apply a data protection policy to CloudWatch logs using AWS CDK. By following these steps, you can better protect sensitive information in your logs and control who can access unmasked data.
Masking Sensitive Data in AWS CloudWatch Logs was originally published in Level Up Coding on Medium, where people are continuing the conversation by highlighting and responding to this story.
This content originally appeared on Level Up Coding - Medium and was authored by Josh Thorne
Josh Thorne | Sciencx (2024-08-18T16:51:28+00:00) Masking Sensitive Data in AWS CloudWatch Logs. Retrieved from https://www.scien.cx/2024/08/18/masking-sensitive-data-in-aws-cloudwatch-logs/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
