This content originally appeared on HackerNoon and was authored by blackheart

\ The Domain Name System (DNS) is often likened to the internet’s phone book, translating human-friendly domain names into IP addresses that computers use to identify each other on the network. While this system is fundamental to the functioning of the internet, it also presents a critical vulnerability that cybercriminals are increasingly exploiting. This article delves into how DNS is being used as a vector for phishing attacks and how these vulnerabilities can be leveraged to compromise even the most secure password managers.
\
The Weak Link: DNS and Its Role in Cybersecurity
DNS is inherently trusting. When a user types a domain name into their browser, the DNS system takes it on faith that the requestor is legitimate and directs them to the corresponding IP address. This openness, while essential for the seamless operation of the internet, creates an attack surface that can be manipulated by bad actors.
\ One of the most common attacks that exploit DNS is DNS spoofing or cache poisoning. In these attacks, the attacker corrupts the DNS cache, causing the DNS server to return an incorrect IP address. As a result, users are unknowingly redirected to malicious websites that can be used to steal credentials or distribute malware.
I can see your DNS from here.
The success of any attack begins with great reconnaissance. After a cyber-criminal determines their target, they will need to conduct through reconnaissance of external assets. The more the attacker knows, the better the chances of success. One such method is DNS reconnaissance. DNS reconnaissance discovers hosts related to a domain. Finding visible hosts from the attacker’s perspective is an important part of the security assessment process.
\ One such tool is known as DNSDumpster. DNSDumpster, an online tool, is our gateway to a treasure trove of domain-related information such as domains, revealing subdomains, DNS records, and other domain-related details. DNSDumpster plays a pivotal role in domain reconnaissance.
\
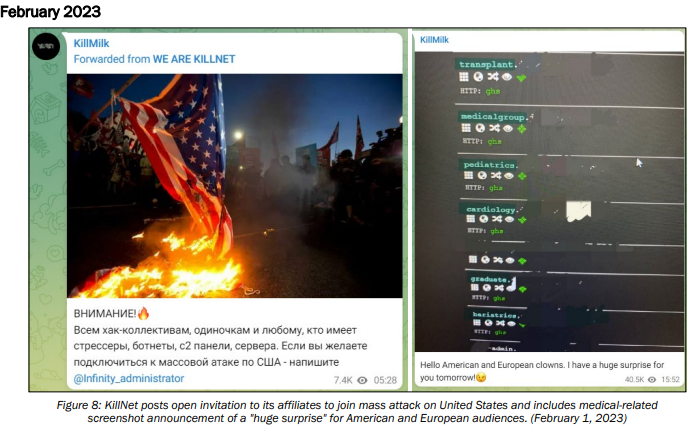
\ One such example of an attack was when KILLNET DDOSD organizations. KILLNET used DNSdumpster to find targets that did not have DDOS protections in place to protect the company assets. DNS is used to provide convince and productivity, but you can start to see where it is also used to help cyber-criminals for DNS related attacks such as Phishing and potentially password managers.
\
One Phish, Two Phish, DNS Phish.
\
This content originally appeared on HackerNoon and was authored by blackheart
blackheart | Sciencx (2024-08-23T18:18:14+00:00) Psst, Your DNS is Showing: Uncovering Vulnerabilities in DNS and Password Managers.. Retrieved from https://www.scien.cx/2024/08/23/psst-your-dns-is-showing-uncovering-vulnerabilities-in-dns-and-password-managers/
Please log in to upload a file.
There are no updates yet.
Click the Upload button above to add an update.
